SafeNet Network HSM
The SafeNet Network HSM 7 (formerly known as Luna SA) is a network HSM which allows users to create a partition to store a key, such as the RA key required to strongly authenticate to the DigiCert® Trust Lifecycle Manager. It includes many features that increase security, connectivity, and ease of administration in dedicated and shared security applications.
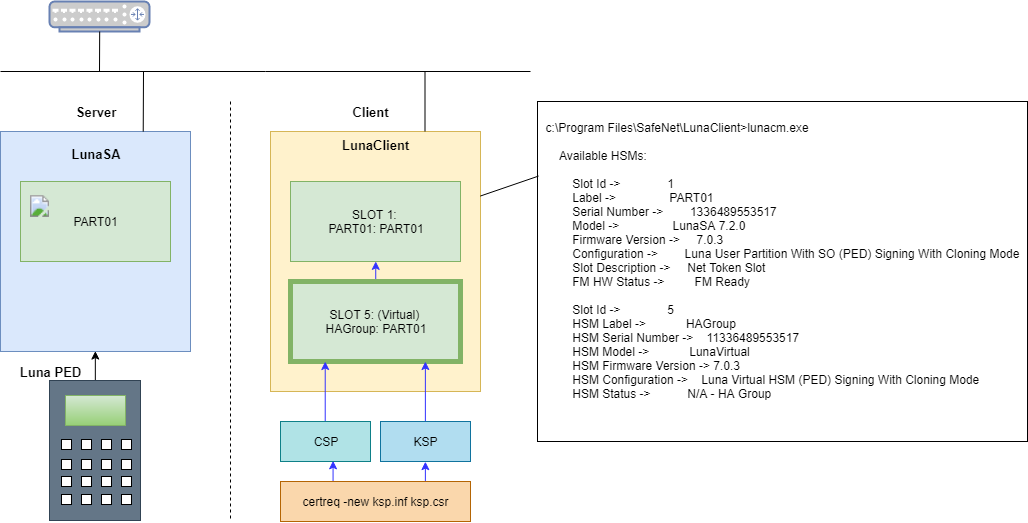
To access the partition of SafeNet Network HSM 7, use the Luna HSM Client through Network Trust Link Service (NTLS).
 |
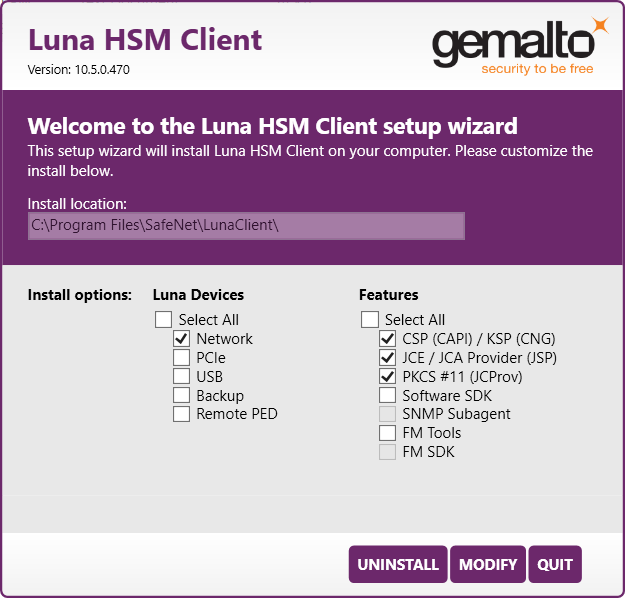
Install Luna HSM Client
Follow the steps below to install the Luna HSM Client software on the client machine:
Run LunaHSMClient.exe as Administrator.
Select Install options and features.
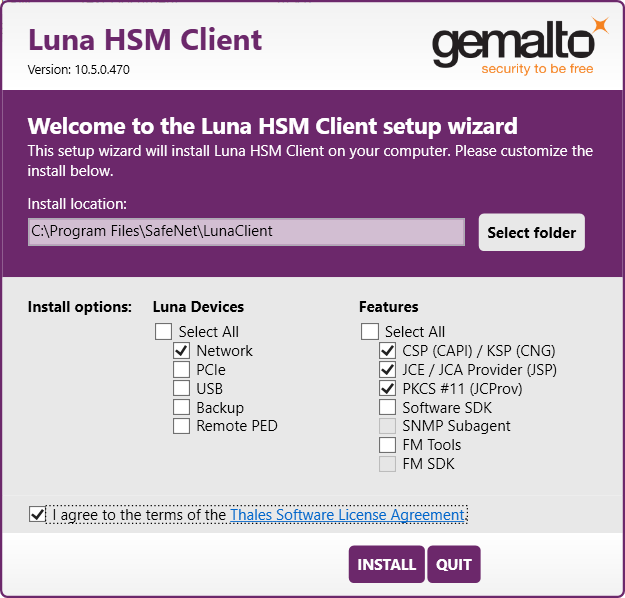
Check the following Luna Devices (some options and features are optional, depending on your environment):
Network
(Optional) Remote PED
Check the following Features (optional features depending on your environment):
CSP(CAPI) / KSP(CNG)
(Optional) JCE / JCA Provider (JSP)
(Optional) PKCS #11 (JCProv)
Check the Software License Agreement, and then select INSTALL.
Wait for completion. The progress bar is displayed at the bottom of the window.
Once the installation is complete, select OK. The UNINSTALL and MODIFY button is displayed. Select QUIT.
Configure Luna HSM Client
Before following the steps listed below, a partition must be created. This is referred to as <PARTITION-NAME> throughout this document.
Follow these steps to configure the Luna HSM Client:
Open a Command Prompt window and run the following commands:
> cd C:\Program Files\SafeNet\LunaClient > lunacm.exe
Create a Network Trust Link (NTL) - this is a one-step setup. If you have already created an NTL, proceed to step 4.
lunacm:> clientconfig deploy -server <SERVER-HOSTNAME> -client <CLIENT-HOSTNAME> -par <PARTITION-NAME> Please wait while we set up the connection to the HSM. This may take several minutes... Please enter appliance admin role user's password: Command Result : No Error lunacm.exe (64-bit) v10.5.0-470. Copyright (c) 2022 SafeNet. All rights reserved. Slot Id -> 1 Label -> <PARTITION-NAME> Serial Number -> 1314971349473 Model -> LunaSA 7.2.0 Firmware Version -> 7.0.3 Configuration -> Luna User Partition With SO (PED) Signing With Cloning Mode Slot Description -> Net Token Slot FM H Status -> FM Ready Current Slot Id: 1 lunacm:> clientconfig v The following Luna SA Slots/Partitions were found: Slot Serial # Label ==== ================ ===== 1 1314971349473 <PARTITION-NAME> Command Result : No Error
If you do not want to follow the one step setup (Step 2 above), follow these steps:
Obtain the Server certificate.
The Server certificate has been created on the HSM, so it needs to be copied from the server.
> pscp -scp admin@<SERVER-HOSTNAME>:server.pem
Add a Server for the Client side.
> vtl addServer -n <SERVER-HOSTNAME> -c server.pem New server <SERVER-HOSTNAME> successfully added to server list.
Create a Client certificate.
> vtl createCert -n <CLIENT-HOSTNAME> Private Key created and written to: C:\Program Files\SafeNet\LunaClient\cert\client\<CLIENT-HOSTNAME>Key.pem Certificate created and written to: C:\Program Files\SafeNet\LunaClient\cert\client\<CLIENT-HOSTNAME>.pem
Upload the Client certificate to the Server.
> pscp -scp cert\client\<CLIENT-HOSTNAME>.pem admin@<SERVER-HOSTNAME>: admin@<SERVER-HOSTNAME>'s password: <CLIENT-HOSTNAME>.pem | 1 kB | 1.1 kB/s | ETA: 00:00:00 | 100%
Next, at the Server:
Register the Client and connect to the HSM via SSH.
lunash:> client register -client <CLIENT-HOSTNAME> -hostname <CLIENT-HOSTNAME> 'client register' successful. Command Result : 0 (Success)
Assign a partition to a Client and connect to the HSM via SSH.
lunash:> client assignPartition -client <CLIENT-HOSTNAME> -partition <PARTITION-NAME> 'client assignPartition' successful. Command Result : 0 (Success)
Now, at the Client:
Confirm connection settings.
The working directory is C:\Program Files\SafeNet\LunaClient
> vtl listServers Server: <SERVER-HOSTNAME> HTL required: no > vtl verify vtl (64-bit) v10.5.0-470. Copyright (c) 2022 SafeNet. All rights reserved. The following Luna SA Slots/Partitions were found: Slot Serial # Label ==== ================ ===== 1 1314971349473 <PARTITION-NAME>
Configure logging (optional). The working directory is C:\Program Files\SafeNet\LunaClient. The name of the log folder is c:\temp in the following example and it can be changed.
> vtl logging configure c:\temp Success setting log path to c:\temp > vtl logging show Client logging written to: c:\temp\LunaCryptokiLog.htm
Configure High Availability (HA)
Create an HA Group.
Open a Command Prompt window and run the following client commands:
> cd C:\Program Files\SafeNet\LunaClient > lunacm.exe lunacm:> slot set -s <SLOT-NUMBER> lunacm:> hagroup creategroup -se <SERIALNUMBER> -label <HA-LABEL> Enter the password: ************ New group with label "HAGroup" created with group number <SERIALNUMBER>. Group configuration is: HA Group Label: <HA-LABEL> HA Group Number: 11336489553517 HA Group Slot ID: Not Available Synchronization: enabled Group Members: 1336489553517 Needs sync: no Standby Members: <none> Slot # Member S/N Member Label Status ====== ========== ============ ====== 1 1336489553517 <PARTITION-NAME>alive Command Result : No Error lunacm.exe (64-bit) v10.5.0-470. Copyright (c) 2022 SafeNet. All rights reserved. Available HSMs: Slot Id -> 1 Label -> <PARTITION-NAME> Serial Number -> 1336489553517 Model -> LunaSA 7.2.0 Firmware Version -> 7.0.3 Configuration -> Luna User Partition With SO (PED) Signing With Cloning Mode Slot Description -> Net Token Slot FM HW Status -> FM Ready Slot Id -> 5 HSM Label -> <HA-LABEL> HSM Serial Number -> 11336489553517 HSM Model -> LunaVirtual HSM Firmware Version -> 7.0.3 HSM Configuration -> Luna Virtual HSM (PED) Signing With Cloning Mode HSM Status -> N/A - HA Group Current Slot Id: 1
Anmerkung
Both Configure CSP and Configure KSP must be configured again if you run the steps above.
Enable HA Only
lunacm:> slot set -s <HA-SLOT-NO> Current Slot Id: <HA-SLOT-NO> (Virtual HSM 7.0.3 (PED) Signing With Cloning Mode) Command Result : No Error lunacm:> hagroup ho -e "HA Only" has been enabled. Command Result : No Error lunacm:> hagroup ho -s This system is configured to show only HA slots. (HA Only is enabled) Command Result : No Error
Configure CSP
Anmerkung
For the deployment of the Autoenrollment Server, you need to configure CSP.
For SafeNet CSP, the utility register.exe (64-bit version) takes care of the registry. To configure CSP, open a Command Prompt window and run the following commands:
Register CSP Library
C:\Program Files\SafeNet\LunaClient\CSP>register.exe /library register.exe (64-bit) v10.5.0-470. Copyright (c) 2022 SafeNet. All rights reserved. Success registering SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Luna enhanced RSA and AES provider for Microsoft Windows. Success registering SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Luna Cryptographic Services for Microsoft Windows. Success registering SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Luna SChannel Cryptographic Services for Microsoft Windows.
Register the partition
C:\Program Files\SafeNet\LunaClient\CSP>register.exe register.exe (64-bit) v10.5.0-470. Copyright (c) 2022 SafeNet. All rights reserved. *************************************************************************** * * * Safenet LunaCSP, Partition Registration * * * * Protect the HSM's challenge for the selected partitions. * * * * NOTE: * * This is a WEAK protection of the challenge. * * After you have configured all applications that will use * * the LunaCSP and ran them once, you MUST run: * * register /partition /strongprotect * * to strongly protect the registered challenges. * * * *************************************************************************** This is a destructive procedure and will overwrite any previous registrations. Do you wish to continue?: [y/n]y Do you want to register the partition named '<PARTITION-NAME>'?[y/n]: y Enter challenge for partition '<PARTITION-NAME>' : <Only hit "Enter" then the PED Authentication will be requested> Success registering the ENCRYPTED challenge for partition '<PARTITIONNAME>:1'. Only the LunaCSP will be able to use this data. Registered 1 partition(s) for use by the LunaCSP.
Register the HA partition
Run the following commands if HA is configured.
c:\Program Files\SafeNet\LunaClient\CSP>register.exe /h register.exe (64-bit) v10.5.0-470. Copyright (c) 2022 SafeNet. All rights reserved. *************************************************************************** * * * Safenet LunaCSP, Partition Registration * * * * Protect the HSM's challenge for the selected partitions. * * * * NOTE: * * This is a WEAK protection of the challenge. * * After you have configured all applications that will use * * the LunaCSP and ran them once, you MUST run: * * register /partition /strongprotect * * to strongly protect the registered challenges. * * * *************************************************************************** This is a destructive procedure and will overwrite any previous registrations. Do you wish to continue?: [y/n]y Do you want to register the partition named ''?[y/n]: y Enter challenge for partition '' :************ Success registering the ENCRYPTED challenge for partition ':1'. Only the LunaCSP will be able to use this data. Registered 1 partition(s) for use by the LunaCSP.
Configure KSP
To configure KSP (CNG), run KspConfig.exe (the default location is C:\Program Files\SafeNet\LunaClient\KSP\).
Follow instructions for the use of the graphical KspConfig.exe as described in KSP for CNG in the SDK Reference Guide.
The following window will appear:
 |
Double-click Register Or View Security Library, then confirm the value
C:\Program Files\SafeNet\LunaClient\cryptoki.dll.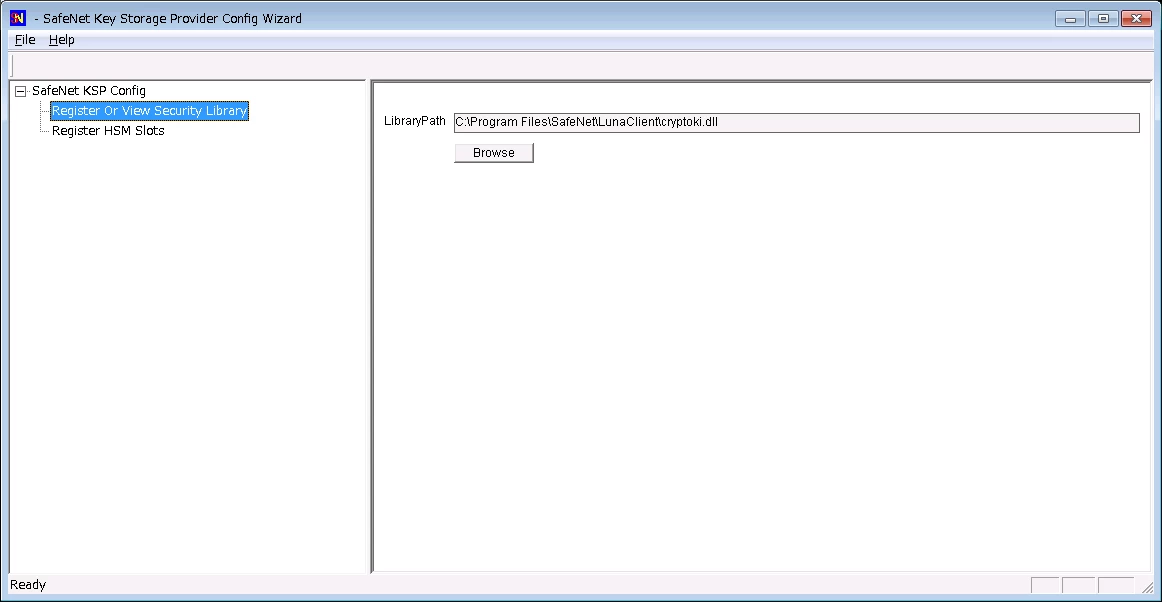
Double-click Register HSM Slots for Administrator/<Domain Name>
Select Administrator
Select <Domain Name>
Select HA Group for Available Slots
Enter Slot Password
Select Register Slot.
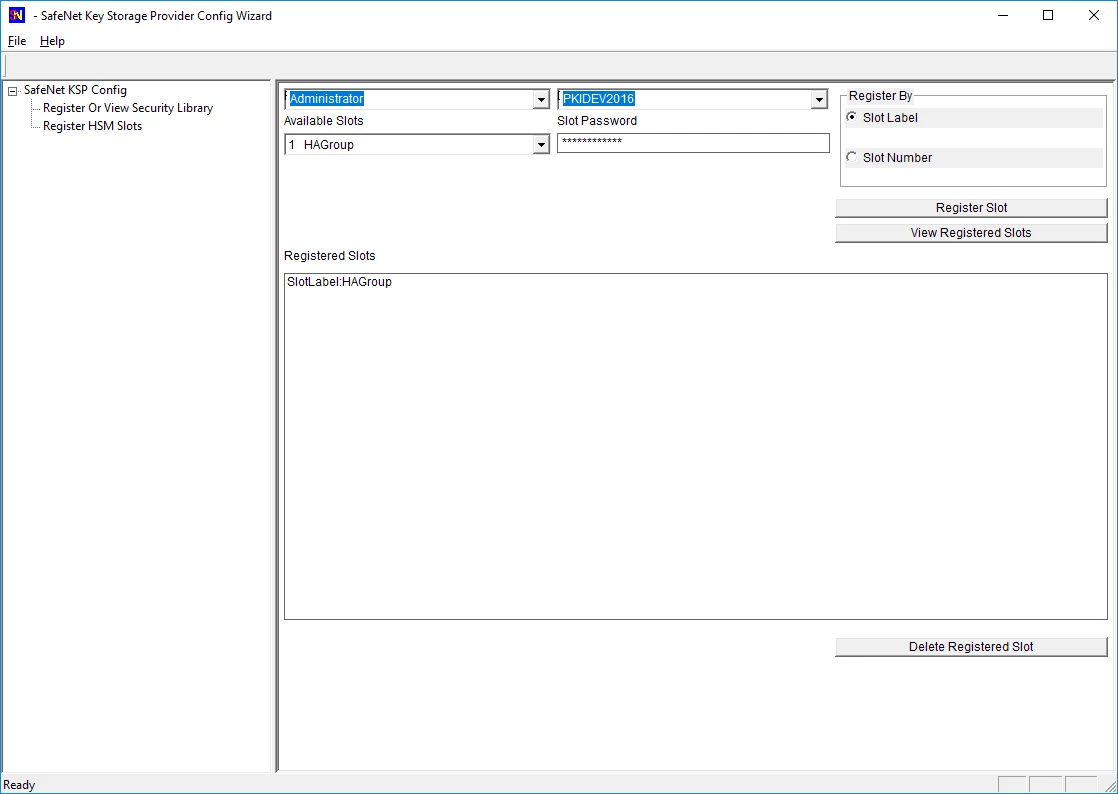
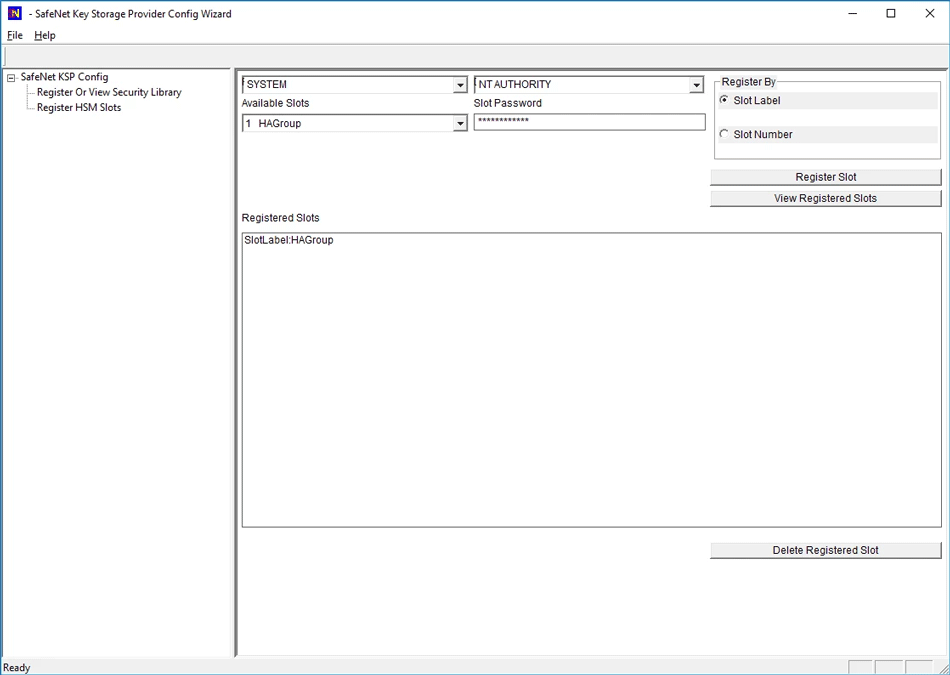
Double-click Register HSM Slots for SYSTEM/NT AUTHORITY.
Select SYSTEM
Select NT AUTHORITY
Select HA Group for Available Slots
Enter Slot Password
Select Register Slot.
Anmerkung
When you click Register Slot, there is no change on Registered Slot, but this step is necessary.
When registering the Luna KSP (with the Luna KSPConfig utility), use the following user and domain combinations:
The user and domain performing these procedures.
The user and domain running the web application and using the private key.
The local user and NT Authority domain user.
The LocalSystem and NTAuthority of the system.
Anmerkung
If you implement the Autoenrollment server, you must also install and register the Luna CSP. Refer to the SafeNet product documentation for details.
Generate CSR
Create the information file for the CSR. To generate the CSR using certreq.exe through CSP, the ProviderName must be Luna Cryptographic Services for Microsoft Windows. The .inf file looks as follows:
[NewRequest] KeyUsageProperty = "NCRYPT_ALLOW_ALL_USAGES" RequestType = PKCS10 ProviderName = "Luna Cryptographic Services for Microsoft Windows" ProviderType = 1 Subject = "CN=Registration Authority" KeyContainer = "CSPRA20220725" MachineKeySet = TRUE HashAlgorithm = SHA256 KeyAlgorithm = RSA KeyLength = 2048
Generate the CSR through HSM.
Anmerkung
<inf-file> is the file created in step 1, <csr-file> is an output file.
Open command prompt and run the following command:
> certreq -new <inf-file> <csr-file>
The CSR file will be generated as follows;
-----BEGIN NEW CERTIFICATE REQUEST----- MIIDjzCCAncCAQAwITEfMB0GA1UEAwwWUmVnaXN0cmF0aW9uIEF1dGhvcml0eTCC .... C610uaqncn6FvLu5pygZYFEVtOanCXNQRRUWiDGWKjHF+10GMh+V5YUur55T4W80 0uwK -----END NEW CERTIFICATE REQUEST-----
Get a client authentication certificate.
Refer to section Get a client authentication certificate
Install RA certificate.
Refer to the section Install RA certificate