Device authentication
Device certificates contain identity information commonly needed for computer (client) to server, server to server, and device to server authentication. This type of certificate is issued from DigiCert® Trust Lifecycle Manager using the Device Authentication for Microsoft Intune (SCEP) certificate profile template, which consumes Device seats from your account.
The following is an example of a typical certificate configuration. It may not meet your specific application requirements.
You should configure the profiles to meet the technical x.509 certificate profile requirements of your 3rd-party application, as well as abiding by any other IT practices, conventions, and certificate policies for your organization.
DigiCert certificate profile
In DigiCert® Trust Lifecycle Manager (TLM), select Manage Profiles from the left navigation menu, then select Add profile.
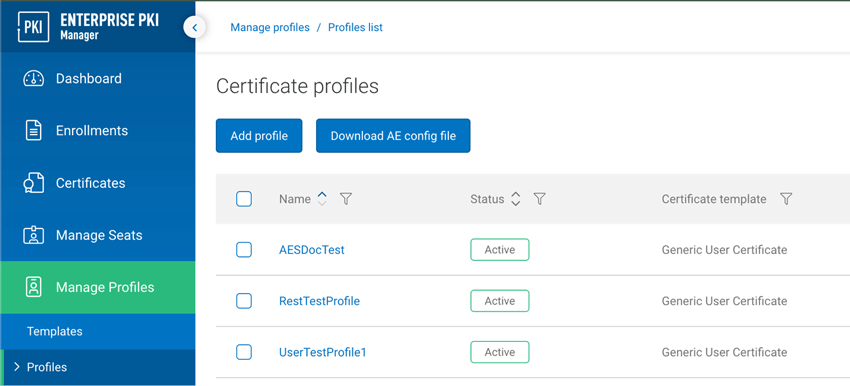
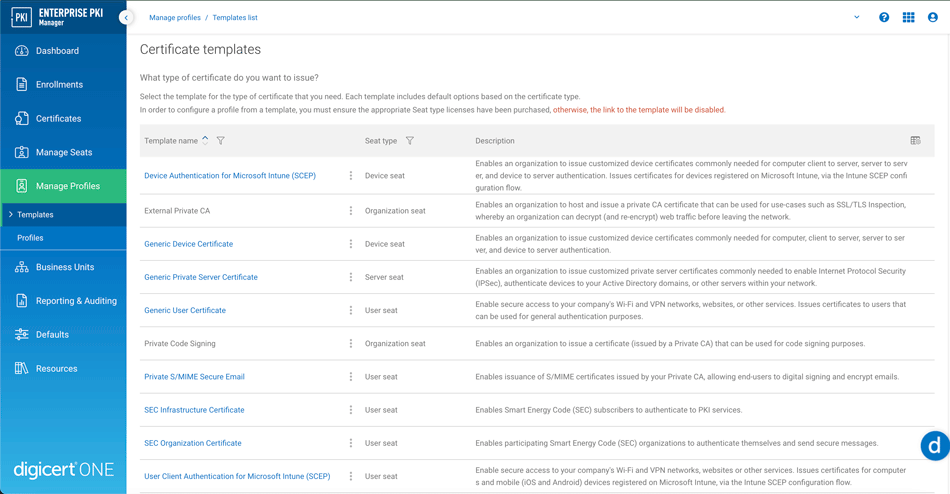
Select either Device authentication for Microsoft Intune (SCEP) or User client authentication for Microsoft Intune (SCEP) from the Certificate templates list, depending on your certificate type requirement.
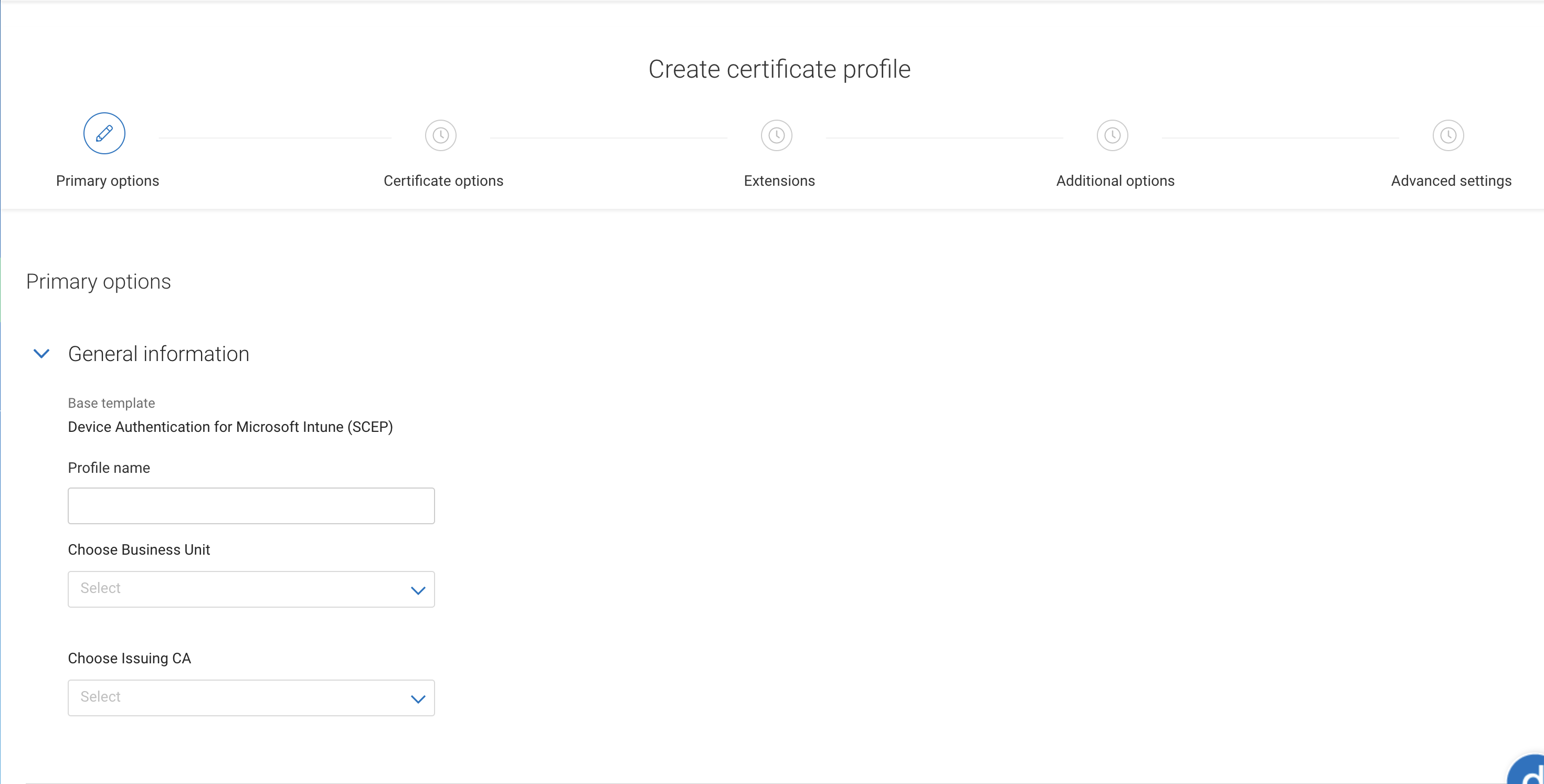
Under Primary options, enter a profile name and select a Business unit and Issuing CA from the dropdown lists.
Under Authentication method, enter the Application ID, Application key and Tenant name previously obtained from your Intune tenant (the Enrollment Method and Authentication Method is pre-selected and grayed out for Intune SCEP certificate profile types).
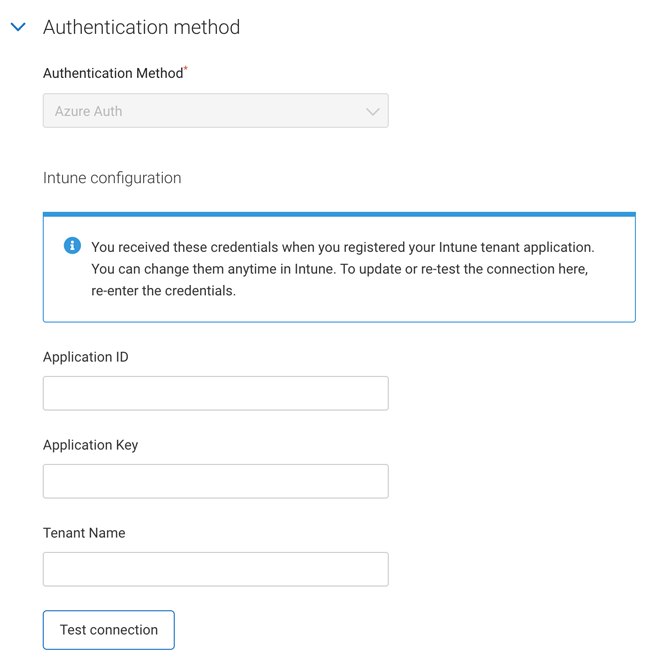
Select Test connection to confirm that DigiCert ONE can successfully connect with the Intune tenant details you provided. If successful, a dialog message is shown in the top right corner of the screen:
Select Next.
Note that you need to update the Intune tenant values whenever they are changed in your Intune portal. Once these credentials are updated, you can retest the connection to confirm the update was a success.
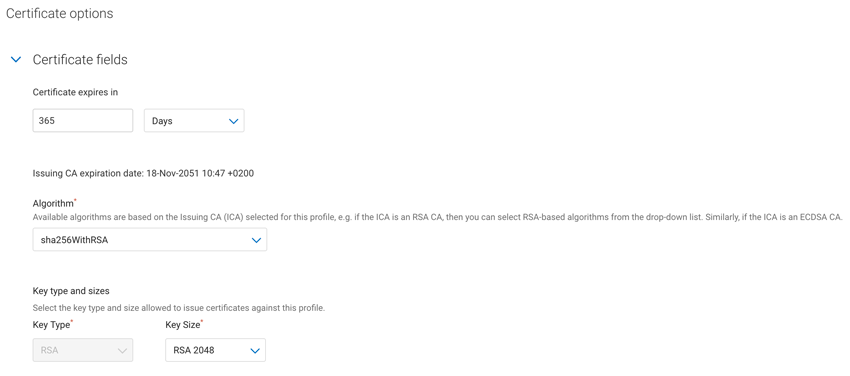
Under Certificate fields, specify the certificate validity period and units (under Certificate expires in), Algorithm, and Key type and Key size for the profile.
Note that the SCEP protocol only supports RSA keys. SCEP certificate profiles in DigiCert ONE DigiCert® Trust Lifecycle Manager pre-populate Key type with RSA.
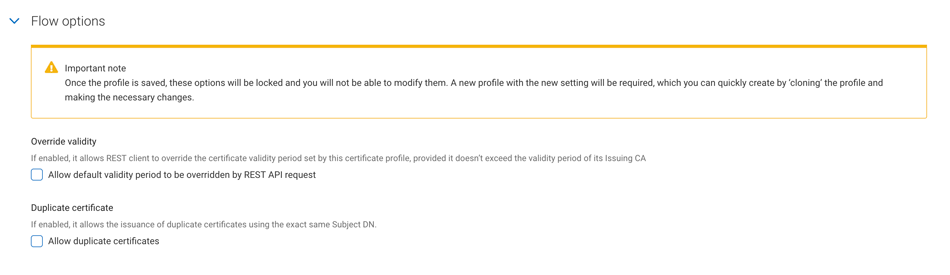
Under Flow options, specify whether the profile allows for certificate validity periods to be overridden by API requests, and whether the profile allows for duplicate certificates, by checking the relative checkboxes.
Under Renewal options, select a Renewal window duration, either from the default values in the dropdown list, or by selecting Custom and specifying a value between 1 and 30 days.
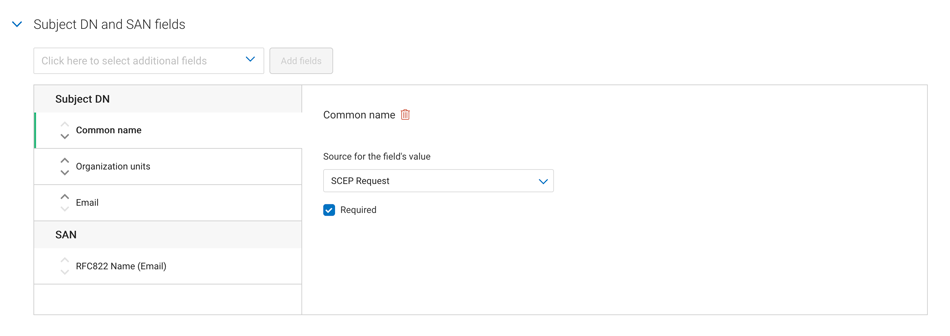
Under Subject DN and SAN fields, select the certificate subject fields you require from the dropdown list and specify the source for each field’s value (SCEP request or Fixed value).
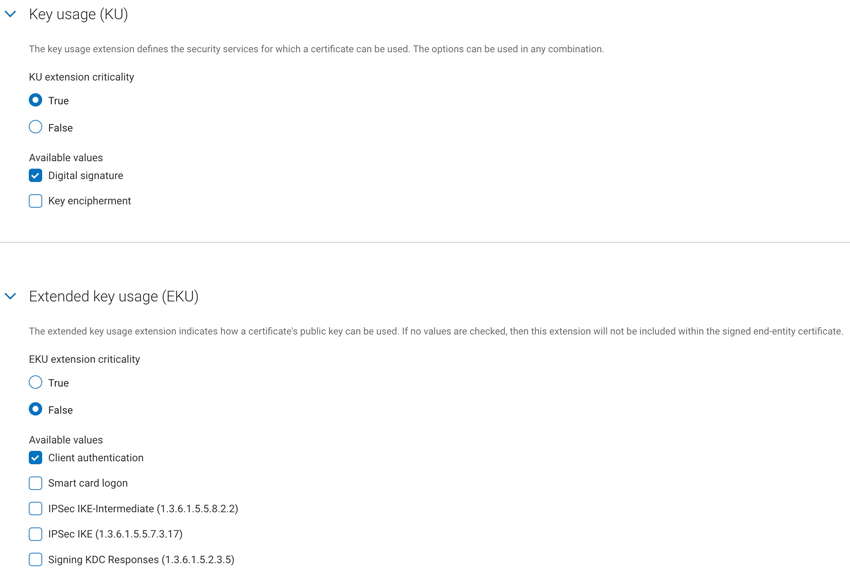
Under Extensions, select the required Key usage (KU) and Extended key usage (EKU) values for the certificate profile. Note that KU extension criticality defaults to True and EKU extension criticality defaults to False, but the criticality for each can be changed by selecting the relevant radio button.
Under Additional options, the Certificate delivery format is preselected as X.509 PEM for SCEP certificate profiles. Select Next.
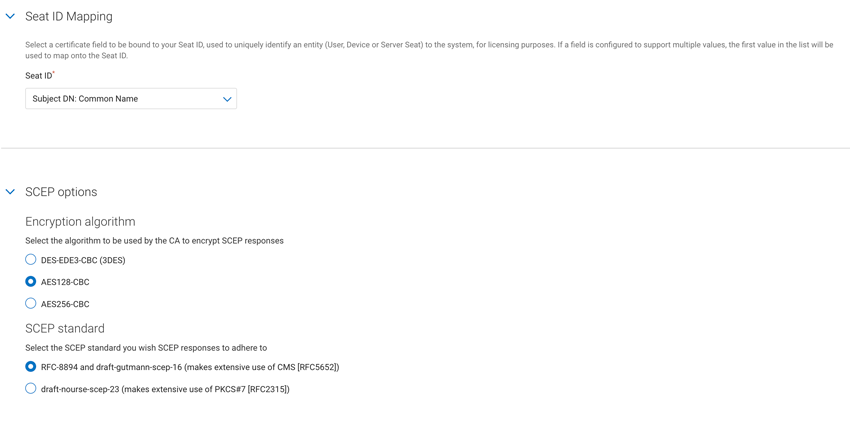
Under Advanced settings, select the certificate field to be bound to your Seat ID (Seat ID mapping) and the Encryption algorithm and SCEP standard (SCEP options).
Select Create.