Generate signature hash
Use this feature to generate signatures against the selected input file. These signatures can be used to check if the file has been tampered with or not.
참고
We are not digitally signing the file but generating a signature hash to ensure data integrity.
To generate signature by using stored certificate,
Select the three dots on the certificate details row using which you want to generate the signature.
Select Generate signature.
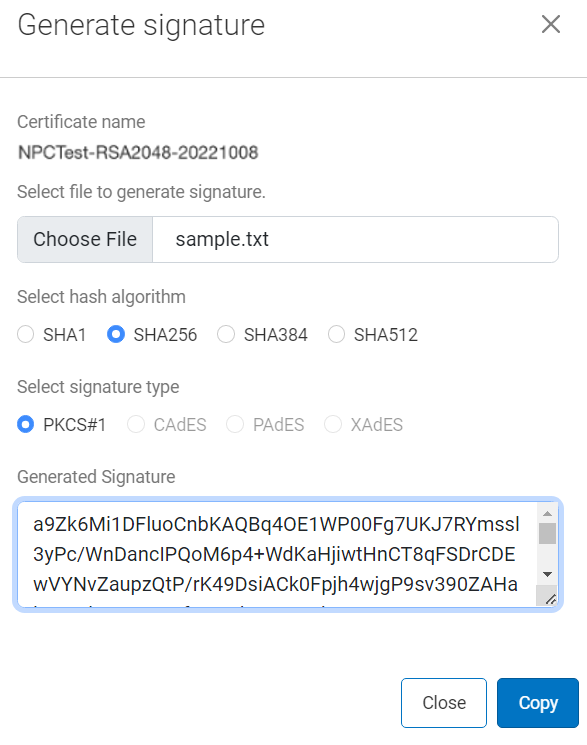
Choose file for signature generation.
Select hash algorithm.
Select signature type.
Now click Generate signature in the dialog box.
The generated signature appears into the field. Copy the generated signature.
 |
When you generate signatures for hardware token, you see a dialog box as it accesses the stored private key.Enter your PIN and click OK .
After the signature is generated, you can copy it and share with the target audience. This helps them to cross-verify the signature, provided they have the pubKey from the same certificate which was initially used to generate the signature.
Copy and paste the generated signature in a file with sample.sgn extension.
Use the Download function on DigiCert Trust Assistant to export the certificate used for generating the signature in x509 fromat.
Use the command below to convert the DER format certificate to PEM format.
$ openssl x509 -in certificate.cer -inform DER -out certificate.pem -outform PEM |
Use the command below to extract the pubKey:
$ openssl x509 -pubkey -noout -in certificate.pem > certificate.pub |
Use the command below to decode the base64 signature:
For Linux:
$ cat sample.sgn | base64 --decode > sig.bin |
For Windows:
# certutil -decode sample.sgn sig.bin |
Considering your file, for which you generated the signature is sample.txt, use the command below to verify the signature:
$ openssl dgst -verify certificate.pub -keyform PEM -sha256 -signature sig.bin -binary sample.txt |
Sample output if file is not tampered with
$ Verified OK |
Sample output if file is tampered with
$ Verification Failure |