DNS CAA resource record check
Certificate authorities must check the CAA resource records prior to issuing certificates.
Importante
DigiCert to start checking CAA resource records before issuing a Secure Email (S/MIME) certificate with a mailbox address
Starting March 13, 2025, at 10:00 MDT (16:00 UTC), DigiCert will check, process, and abide by your email domains' DNS Certification Authority Authorization (CAA) resource records before DigiCert issues your Secure Email (S/MIME) certificates.
To learn more this change, see our March 13, 2025, change log, DigiCert to start checking CAA resource records before issuing Secure Email (S/MIME) certificates.
Before a Certificate Authority (CA) issues a TLS/SSL certificate or a Secure Email (S/MIME) certificate with a mailbox address, they must check, process, and abide by the domain or mailbox’s (email domain’) DNS Certification Authority Authorization (CAA) resource records.
A CAA resource record is NOT required
A CAA record is NOT REQUIRED for DigiCert to issue a TLS/SSL or a Secure Email (S/MIME) certificate. The information provided below only applies if you are in one of these situations:
Have CAA records set up for your TLS domains and mailbox domains
Plan to add CAA resource records for your TLS domains and mailbox domains
How the CAA resource record check works
Before issuing a TLS/SSL certificate or a Secure Email (S/MIME) certificate, a CA, such as DigiCert, checks the domain's/mailbox domain's CAA records to verify that they are authorized to issue that certificate. A CA can issue the TLS or S/MIME certificate if one of the following conditions is true:
They do not find a CAA record for your domain.
They find a CAA record for your domain authorizing them to issue that certificate.
TLS certificate:
yourdomain CAA 0 issue "digicert.com"and/oryourdomain CAA 0 issuewild "digicert.com"S/MIME certificate:
yourdomain CAA 0 issuemail "digicert.com"
They only find CAA records for your domain without the "
issue", "issuewild", or "issuemail" property tags.
CA authorization for DigiCert brand certificates
DigiCert has multiple certificate brands, and any of the CAA record values below are acceptable for authorizing DigiCert to issue your DigiCert TLS/SSL and Secure Email (S/MIME) certificates. When creating a CAA record and authorizing DigiCert to issue TLS/SSL and Secure Email (S/MIME) certificates for your domain, you authorize DigiCert to issue all DigiCert certificate brands for that domain, like Thawte, GeoTrust, and RapidSSL.
What is a DNS CAA resource record?
Certification Authority Authorization (CAA) resource records allow domain owners to create policies that authorize specific Certificate Authorities (CAs) to issue TLS/SSL and Secure Email (S/MIME) certificates for their associated domains. Domain owners can use CAA records to create security policies for an entire domain, such as example.com, or a specific hostname, like mail.example.com.
When you create a CAA record for your base domain, you create an umbrella policy for its subdomains in that policy unless you create a separate CAA record for a specific subdomain. Do you have a CAA record for example.com but want to create a different security policy for mail.example.com? Create a CAA record specifically for the mail.example.com subdomain.
Now, when you order a TLS/SSL certificate for mail.example.com, the CA queries your DNS for CAA records for that subdomain. If the CA finds a record for mail.example.com, then the search stops, and they apply that policy to the certificate order. If the CA does not see a record for mail.example.com, they continue their DNS query for CAA records at its parent domain, example.com. If the CA finds a record for example.com, they apply the parent domain's policy to the certificate order for mail.example.com.
CAA resource record property tags
You can associate multiple properties with the same domain by publishing multiple CAA records for that domain name. However, each CAA record can only authorize one CA to issue certificates or, in some instances, one type of certificate for your domain. To allow multiple CAs to issue certificates for your domain, you must create at least one CAA record for each CA, and in some instances, two CAA records.
If you need help setting up CAA records for your TLS certificates, see the CAA Record Helper.
Authorize DigiCert to issue wildcard certificates for a domain
When you order a certificate for *.yourdomain, DigiCert includes yourdomain in the certificate at no extra cost. Including the wildcard domain and the domain in the certificate poses a problem when creating "issue" and "issuewild" CAA records for your domains using multiple CAs.
For example, DigiCert includes yourdomain with your certificate order for *.yourdomain. Therefore, if you authorize multiple CAs to issue certificates for yourdomain, use one of the options below so that DigiCert can issue your certificates.
Only use the “issue” property tag and create an “issue” CAA record for DigiCert
Unless you have a specific reason for creating an "issuewild" CAA record for yourdomain, don’t. Managing only "issue" CAA RRs is much simpler:
ejemplo 4. "issue"yourdomain CAA 0 issue "digicert.com"
Create an “issue” CAA record and an “issuewild” for DigiCert
If organization policy allows it, and you must create separate CAA records for yourdomain and *.yourdomain.com, create two rules:
One authorizing DigiCert to issue certificates for yourdomain
One authorizing DigiCert to issue certificates for *.yourdomain
ejemplo 5. "issue" and "issuewild"yourdomain CAA 0 issue "digicert.com" yourdomain CAA 0 issuewild "digicert.com"
Contact Us
If organization policy prevents you from authorizing DigiCert to issue certificates for yourdomain, contact us. We will work to solve the problem of issuing the certificate for *.yourdomain.
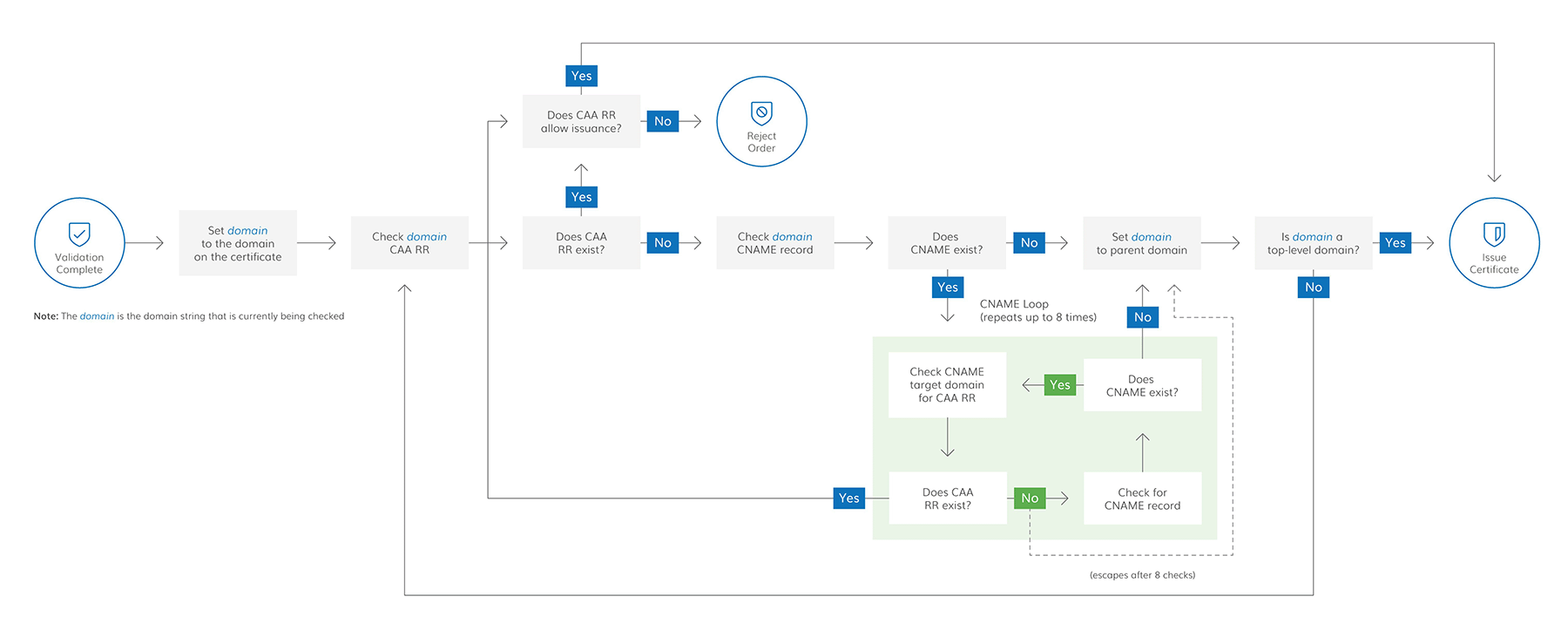
How CAA resource records and CNAME work together
When requesting a TLS/SSL or Secure Email (S/MIME) certificate for a domain (for example, my.blog.example.com) that contains a CNAME record pointing to another domain (for example, my.blog.example.net), the CA follows a specific process laid out in the baseline requirements to find a CAA record authorizing them to issue your certificate.
CNAME targets
As a preventative measure against resource exhaustion attacks, a CA only has to follow up to 8 CNAME targets (8 CNAME records: blog.example.com is a CNAME for blog.example.net, which is a CNAME for blog.example.org, and so on, eight levels deep).
The process starts at the domain name on the certificate request and continues to the top-level domain. The process will stop at any point if the CA finds CAA records. Once found, the CAA records determine whether the CA can issue your certificate.
Step 1: CA checks the CAA record for the domain name on the certificate request–my.blog.example.com
The search stops if the CA finds a CAA record for the domain on the certificate request. The CA checks to see if a CAA record authorizes them to issue your certificate. If they find the record, the CA issues the certificate. If they don't find the record, the CA cannot issue the certificate.
If the CA does not find a CAA record for the domain on the certificate request, the CAA record search continues.
Step 2: CA checks the CAA records for the CNAME target domain–my.blog.example.net
The search stops if the CA finds a CAA record for the CNAME target domain. The CA checks to see if a CAA record authorizes them to issue your certificate. If they find the record, the CA issues the certificate. If they don't find the record, the CA cannot issue the certificate.
If the CA doesn't find a CAA record for the domain on the certificate request, the CAA record search continues.
CA checks the CAA records for the original domain's parent domain–blog.example.com
The search stops if the CA finds a CAA record for the original domain's parent domain. The CA checks to see if a CAA record authorizes them to issue your certificate. If they find the record, the CA issues the certificate. If they don't find the record, the CA cannot issue the certificate.
If the CA doesn't find a CAA record for the original domain's parent domain, the CAA record search continues.
Step 4: CA checks the CAA records for the original domain's base domain–example.com
The search stops if the CA finds a CAA record for the original domain's base domain. The CA checks to see if a CAA record authorizes them to issue your certificate. If they find the record, the CA issues the certificate. If they don't find the record, the CA cannot issue the certificate.
If the CA doesn't find a CAA record for the original domain's base domain, the CAA record search continues.
Step 5: CA checks the CAA records for the original domain's top-level domain–com
The search stops.
If the CA finds a CAA record for the original domain's top-level domain. The CA checks to see if a CAA record authorizes them to issue your certificate. If they find the record, the CA issues the certificate. If they don't find the record, the CA cannot issue the certificate.
If the CA doesn't find a CAA record for the original domain's top-level domain, the CA issues the certificate.