How to use your ACME credentials
ACME credentials are required to submit certificate lifecycle commands to DigiCert through the ACME client of your choice. Your ACME credentials provide authorization to DigiCert when you submit a certificate request through the ACME client. ACME credentials are:
DigiCert request URL—the DigiCert ACME server where your request is sent and processed.
Key identifier (KID)—unique identifier that links your account to a stored authentication code (the HMAC).
HMAC key—unique credential that authenticates your account to the DigiCert ACME server.
Where do I get ACME credentials?
The certificate authority or other certificate source you use to get your TLS/SSL certificate generates and delivers the ACME credentials. In this case, DigiCert CertCentral generates your ACME credentials.
If you generated bare ACME credentials when starting your certificate request in CertCentral, provide these credentials in your certificate request through your preferred ACME client.
If CertCentral created the full command-line instruction for your certificate request, you shouldn't have to edit it. The command includes your credentials and information needed to request, receive, and install your certificate.
How do I use my ACME credentials?
How you provide your ACME credentials depends on your ACME client. Most commonly, ACME credentials are requested as external account binding or EAB objects.
Your ACME credentials may be embedded in each certificate request, such as in this certificate request example for the Certbot ACME client:
sudo certbot --apache --register-unsafely-without-email --eab-kid zcwmKf9sCnDUZsbCOgnv1ijy46l6UeEYCavSQQirl-g --eab-hmac-key RHZraHBXQUxWTEFGdFhndjRVNmV3S3F6c2VNZDM1QzRURGhjdHF3S1NublJjN3dhVUFObzA0SXJwVHBnU2xnRA --server https://one.digicert.com/mpki/api/v1/acme/v2/directory --config-dir /usr/local/certbot/my_webserver_config/ -d my.host -d alias.my.host
Your ACME credentials may be configured in the client to retrieve them when needed, such as in this Certify the Web ACME client:
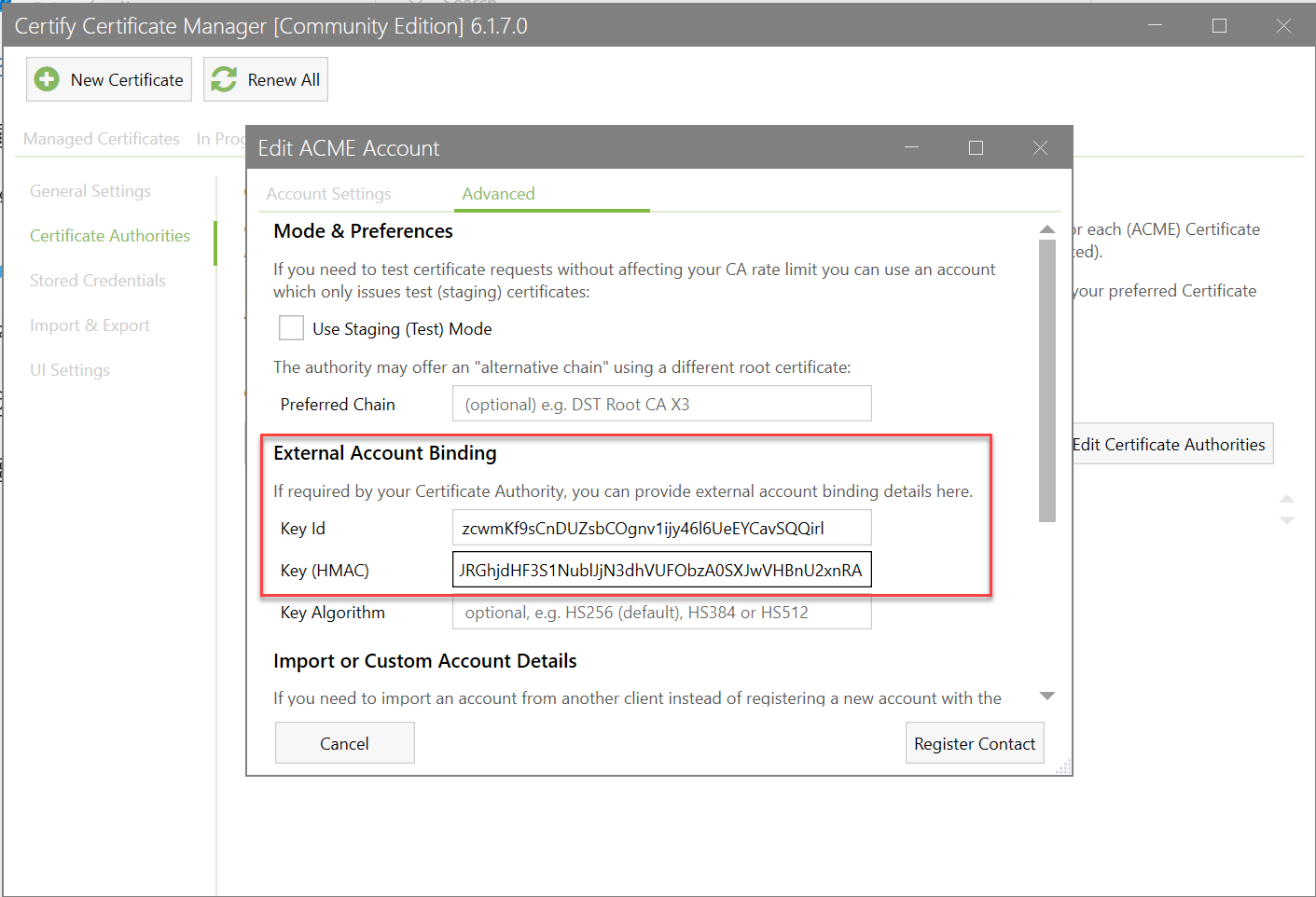
Certificate actions and settings
The certificate request commands, functions, and request parameters that ACME clients support vary from client to client. Refer to your client's documentation and support resources for detailed command and implementation instructions.
To optimize automation of certificate management, be familiar with these functions on your ACME client:
Request a new certificate
Install an issued certificate
Automatically renew an expiring certificate
Revoke a valid certificate
Request a duplicate or reissue a certificate
A, for server compatibility and business policy requirements, you should also be familiar with how to manage these certificate settings through your ACME client:
Common name and subject alternative names
Validity period
Key type and size
Signature hash algorithm
Key management
Certificate templates or profiles
DNS configuration