Configure iOS/iPadOS enrollment via SCEP
DigiCert® Trust Lifecycle Manager supports web-based iOS/iPadOS certificate enrollments via the Simple Certificate Enrollment Protocol (SCEP) to facilitate direct provisioning of certificates to Apple iPhones and iPads without the need to deploy a full-scale MDM/UEM solution.
Prerequisites
Your Trust Lifecycle Manager account needs the SCEP and Enable iOS/iPadOS features enabled in DigiCert® Account Manager.
You need an issuing CA in DigiCert® Private CA that is configured to Allow CA to decrypt and sign SCEP packets.
Your DigiCert ONE instance must be set up to sign Apple .mobileConfig files using a public CA certificate.
Note
If you use the cloud-hosted version of DigiCert ONE, contact your DigiCert account representative for help with these prerequisites. For on-premises deployments, reach out to your DigiCert system administrator.
Create certificate profile in Trust Lifecycle Manager
To create a certificate profile for iOS/iPadOS enrollment:
From the Trust Lifecycle Manager menu, go to Policies > Certificate profiles.
Select the Create profile from template action at the top of the page.
Select one of the following base templates as the basis for creating the certificate profile:
Generic Device CertificateGeneric User Certificate
Work through the profile configuration wizard, focusing on the iOS/iPadOS-related options described below and making other selections for your business needs and types of certificates you want to issue. After filling out each screen, select Next to move to the next screen.
On the initial Primary options screen of the profile wizard, configure the:
General information: Select the applicable business unit and SCEP-enabled issuing CA to issue certificates.
Enrollment method: Select
iOS/iPadOS.Authentication method:
Enrollment Codeis automatically selected for you for iOS/iPadOS-based enrollments. You can adjust the enrollment code settings.
On the Certificate options screen:
Subject DN and SAN fields: Select the fields to include in the Subject Distinguished Name (DN) and Subject Alternative Name (SAN) of issued certificates.
For each field, select either
Entered/Uploaded by AdminorFixed Valueas the source of the field's value, depending on whether the value will get supplied dynamically by the administrator during enrollment or not.By default, only the Common name is included and configured to have its value
Entered/Uploaded by Admin. If you only need a common name in your certificates and want to set it at enrollment time, you don't need to make any other selections here.
On the Additional options screen:
Certificate delivery format is set to X.509 PEM and cannot be changed, as this is the required delivery format for the SCEP protocol.
On the Advanced settings screen:
Seat ID Mapping: Select one of the available certificate fields to use as the seat ID when enrolling certificates via iOS/iPadOS. The default selection is to use the certificate common name as the seat ID in Trust Lifecycle Manager.
iOS device profile configuration: The
Web authentication settingsuse case is automatically enabled as this is currently the only supported use case for iOS-based enrollments.
Select Create to save the new certificate profile.
Create and enroll seats against the profile in bulk
Create a CSV file
Create a CSV file in the following format to use to create seats and assign enrollment codes to them in Trust Lifecycle Manager:
seat_id,seat_name,enrollment_code,enrollment_email
For example:
seat01,seat01,817902767,seat01@example.com
In this example, 817902767 is the enrollment code needed to validate the enrollment on the Apple device. The enrollment link gets emailed to the address provided in the enrollment_email field.
For more examples of how to create the CSV file, see Bulk enroll multiple seats.
Important
If your Trust Lifecycle Manager account uses the legacy licensing model (with different seat types), you must select a Seat type when enrolling seats individually or in bulk. You can only enroll one seat type at a time. To bulk enroll different seat types, prepare one CSV file per type. To learn more, see Legacy seat types.
Upload CSV to create/enroll seats
Upload the CSV file to create the seat records and register the enrollment codes in Trust Lifecycle Manager:
From the Trust Lifecycle Manager menu, go to Account > Seats.
Select the button to Manage seats in bulk.
In the Operation dropdown, select Create/Update seats.
Select the enroll the Seats against a profile checkbox to enable this option.
Select the CSV file contains enrollment codes generation method.
Select the profile you created from the certificate profiles dropdown.
Upload the CSV file that contains the data for all the seats to enroll.
As soon as you upload a valid CSV file, the system enrolls the corresponding seat records. To see a report of all the enrolled seats and the status of each, select the Download results JSON link.
When you're finished, select the Ok button to return to the main Account > Seats page.
The seat records you created should now be present in the table here.
Select Inventory > Enrollments to check the pending code-based enrollments.
Validate the enrollment and install the certificate on the Apple device
Warning
The Safari web browser is required to complete these steps.
After validating the enrollment and downloading the .mobileConfig file, you must install the profile within 8 minutes or it gets automatically deleted by iOS/iPadOS as a security precaution. To avoid issues, complete both of the following steps in a single session.
Validate the enrollment and download the profile
The enrollment link gets emailed to the address used when creating/enrolling the seat in Trust Lifecycle Manager.
Use the Safari web browser to open the enrollment link on the Apple device where you want to install the certificate.
Enter the corresponding enrollment code for the seat record in Trust Lifecycle Manager.
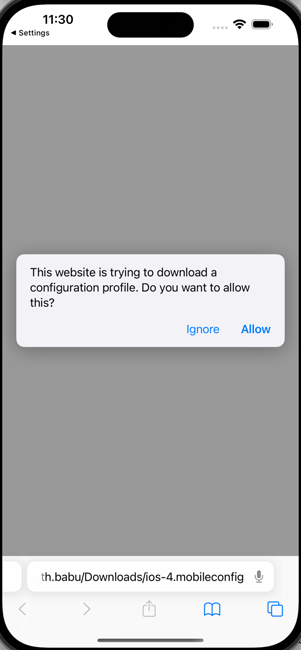
Upon successful validation, the response includes the signed .mobileConfig file.
Select Allow to enable Safari to download the profile.
Install the profile and certificate
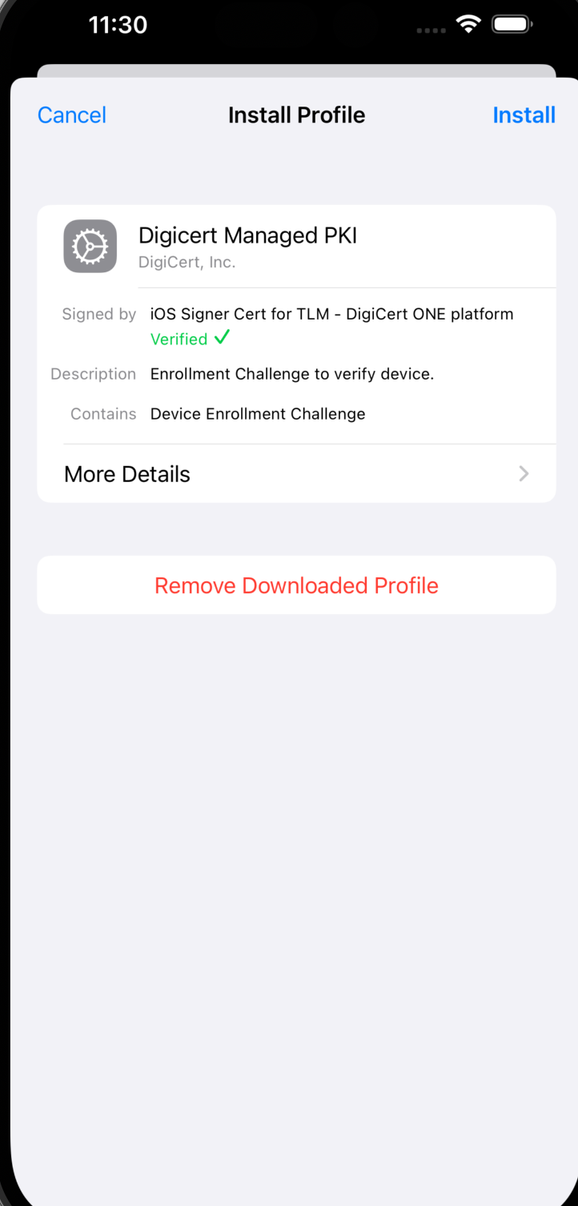
Go to Settings > General > Device Management on the Apple device.
Verify the profile details and select Install to install it.
iOS sends a certificate request to Trust Lifecycle Manager and installs the resulting certificate profile and payload on the device.