SCEP integration guide for Jamf Pro
DigiCert® Trust Lifecycle Manager facilitates certificate issuance through your Jamf Pro mobile device management (MDM) environment. This guide describes how to integrate with Jamf using the SCEP (Simple Certificate Enrollment Protocol) service of Trust Lifecycle Manager.
注意
The Jamf Pro SCEP integration supports automatic creation of seat records in Trust Lifecycle Manager when Jamf-managed devices enroll certificates. If you prefer to create seats manually beforehand, see SCEP integration guide (manual seat creation).
重要
The SCEP service can authenticate devices using either dynamic or static (global) enrollment codes. DigiCert strongly recommends using dynamic enrollment codes, as they are the most secure option and provide enhanced tracking and management capabilities.
This guide focuses on the use of dynamic enrollment codes for authentication but mentions the static enrollment code option where applicable.
Prerequisites
Contact your DigiCert account representative if you need help verifying these settings.
Your Trust Lifecycle Manager account is enabled for SCEP enrollment.
Issuing CA in your account configured to Allow CA to decrypt and sign SCEP packets.
Consult with your local admin or Jamf Pro documentation for questions regarding Jamf configuration and use.
Active Jamf Pro account with the target devices for enrollment added to it.
Your Jamf Pro account is configured with an Apple MDM Push certificate if you intend to issue certificates to Apple iOS devices.
(Recommended) Create Smart Groups in Jamf Pro for each logical group of devices or computers to enroll. For more information, refer to the official Jamf Pro documentation.
Workflow
To set up the Jamf Pro integration via SCEP, complete these tasks in order.
Task | Section | |
|---|---|---|
1. | Enable API access to your Trust Lifecycle Manager account and decide how to identify devices. | |
2. | Define the properties of the certificates to issue in Trust Lifecycle Manager. | |
3. | Create Jamf configuration profiles with the required SCEP settings to enroll certificates from DigiCert. | |
4. | Verify the certificates are getting issued in Trust Lifecycle Manager and provisioned by Jamf Pro. |
Prepare the integration
Dynamic SCEP-based enrollments require API access from Jamf Pro to your Trust Lifecycle Manager account and a common way to identify the devices in both platforms.
To use dynamic enrollment codes with SCEP, Jamf Pro needs API access to your Trust Lifecycle Manager account using a client authentication certificate.
注意
For tracking purposes, DigiCert recommends using a dedicated API service user for the integration, as described below. You can also generate the client authentication certificate for a standard user with the User and certificate manager role or equivalent permissions.
The SCEP integration requires a common way to identify devices to both DigiCert and Jamf. You can use any identifier from Jamf Pro as long as it's present for all the devices to enroll. This identifier gets added to the certificates and assigned to the corresponding seat records for the devices in Trust Lifecycle Manager.
To ensure the identifier is present for all the devices, DigiCert recommends using one of the following Jamf Pro identifiers, depending on the general device type.
Device type | Recommended Jamf Pro identifier |
|---|---|
Institutionally-owned | |
Personally-owned (BYOD) | |
Create certificate profiles in Trust Lifecycle Manager
A certificate profile defines the issuing CA and general properties for a type of certificate you can issue in Trust Lifecycle Manager. Using a base template as the starting point, create a profile for each type of certificate you want to enroll via Jamf Pro.
Use one of the following base templates as the starting point when creating certificate profiles in Trust Lifecycle Manager for use with Jamf Pro.
Both templates support SCEP-based enrollments and issue private trust certificates from CAs in DigiCert® Private CA.
Make sure you have available seat licenses allocated to the business unit in Trust Lifecycle Manager where you will issue the certificates.
Template name |
|---|
|
|
To create a certificate profile in Trust Lifecycle Manager to use with Jamf Pro:
In the Trust Lifecycle Manager menu, select Policies > Certificate profiles.
Select the Create profile from template button.
Select one of the templates from the Available base templates section as the basis for creating the certificate profile.
Follow the profile creation wizard, focusing on the Jamf-related options described below and making other selections for your business needs.
On the Primary options screen:
General information:
Profile name: Give the profile a readily identifiable name. You will select the profile by name when configuring Jamf Pro. To ensure compatibility, avoid special characters like "(" in the profile name, use hyphens instead of whitespace as word separators, and limit the name to 34 characters or less.
Business unit: Select the applicable business unit to assign the certificates to in Trust Lifecycle Manager.
Issuing CA: Select the certificate authority (CA) to issue the certificates. The issuing CA you select must have the Allow CA to decrypt and sign SCEP packets option enabled, otherwise the
SCEPenrollment method is not available below.
Enrollment method: Select
SCEP.Authentication method: Select one of the following authentication types and configure options for it:
Dynamic enrollment code options: Authenticate each Jamf device using a dynamic enrollment code. With this option, each device has its own enrollment code.
重要
DigiCert strongly recommends using Dynamic enrollment codes for authentication. This is the most secure option and provides enhanced tracking and management capabilities.
Global enrollment code options: Authenticate all Jamf devices using a static code that you configure in the profile. With this option, all Jamf devices share the same enrollment code and do not need to be registered in Trust Lifecycle Manager beforehand.
警告
If you use a Global enrollment code for authentication, any client that knows the code can potentially issue a certificate from the profile.
Under Certificate options > Subject DN and SAN fields, configure the fields to include in certificates issued from this profile:
By default, each certificate includes a Common name in the Subject DN, which gets it value from the SCEP request.
(Optional) Use the dropdown to add more fields to the certificates. For the Source of the field's value, select either:
SCEP request: To assign the value dynamically from the SCEP enrollment request.
Fixed value: To enter a static value to assign to all certificates.
重要
Important notes:
Each certificate profile must include at least one field (for example, the Common name) that gets its value from the SCEP request, which will be used to carry the device identifiers from Jamf Pro.
To use the certificate profile redistribution method to ensure certificates get reissued when they are nearing expiration, add an Organization units (OU) field to the Subject DN that gets its value from the SCEP request.
You will configure the Jamf configuration profile to supply corresponding values for the SCEP request fields when a device requests a certificate.
Under Advanced settings > Seat ID Mapping:
Seat ID: Select the certificate field that will carry the Jamf Pro device identifiers used as the
Seat IDvalues in the corresponding seat records in Trust Lifecycle Manager. For example, to read the device identifiers from the certificate common name, set this toSubject DN: Common name.
To save the new certificate profile, select Create on the final wizard screen.
Copy and save the certificate profile’s SCEP Server URL for use in your Jamf Pro mobile device configuration profile.
Configure Jamf for SCEP enrollments
To enable endpoint devices to enroll certificates from DigiCert ONE, you need to create a Jamf Pro configuration profile with the SCEP settings for your certificate profile in Trust Lifecycle Manager. The scope of the Jamf profile must include the target users and devices to enroll.
注意
For more details about Jamf configuration profiles, refer to the official Jamf Pro documentation.
To create a new configuration profile in Jamf Pro:
In the Jamf Pro portal, navigate to either the Computers or Devices tab, depending on where your devices are set up.
Select Content Management > Configuration Profiles.
Select New to create a new configuration profile.
In the General tab, configure the following settings:
Name: Enter a name to help identify this configuration profile.
Level: Select one of the following:
Device LevelorComputer Level: To make the profile available to all users on the device or computer.提示
For MDM purposes, most Jamf configuration profiles should use either the
Device LevelorComputer Levelsetting.User Level: To associate the profile with a specific user account on a computer. This setting is not as commonly used and is primarily applicable to computers shared by multiple users.
Distribution Method: Select
Install Automatically.
In the SCEP tab, configure the SCEP settings for the certificate profile you created in Trust Lifecycle Manager:
URL: Enter the SCEP Server URL for the corresponding profile to issue certificates from in Trust Lifecycle Manager. Refer to the Create certificate profiles section for details.
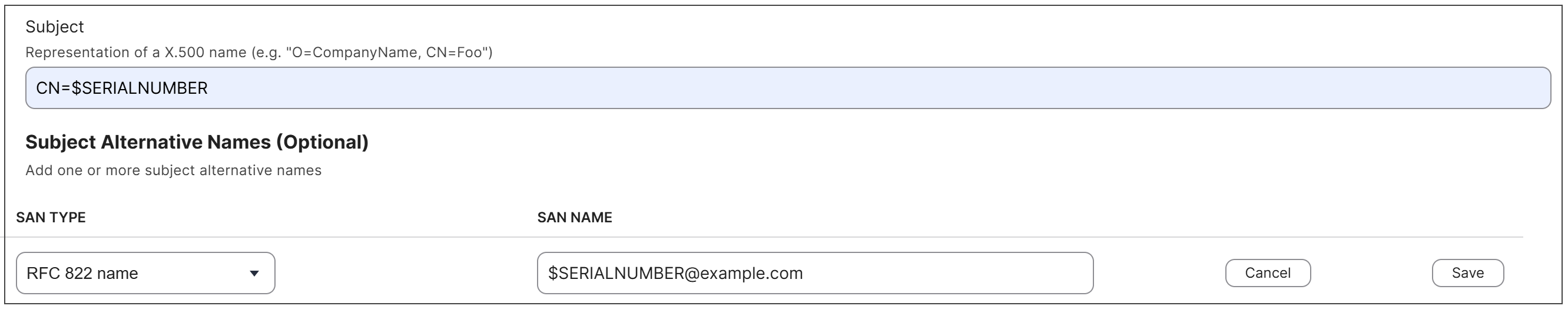
Subject: Enter the Subject DN value string to add to the certificates. For example, enter
CN=$SERIALNUMBERto dynamically insert the serial number of each device as the common name in SCEP enrollment requests.Subject Alternative Name: (Optional) If your certificate profile in Trust Lifecycle Manager includes fields in the Subject Alternative Name (SAN) extension that get their values from the SCEP request, use the Add button to add matching field types and enter value strings for them.
In the following example, the SCEP certificate settings in the Jamf profile include each device's serial number in the Subject common name, plus a SAN RFC 822 field with the serial number as part of the email address.
重要
Important notes:
Every certificate field configured in the Trust Lifecycle Manager certificate profile that gets its value from the SCEP request must have a corresponding value in the Jamf configuration profile.
For a list of payload variables you can use in your Jamf configuration profiles, refer to the official Jamf Pro documentation. Payload variables are case-sensitive.
Any certificate field configured with a Fixed value in the Trust Lifecycle Manager certificate profile must not be present in the Jamf configuration profile.
To use the certificate profile redistribution method to ensure certificates get reissued when they are nearing expiration, add
OU=$PROFILE_IDENTIFIERto the Subject field. This adds the ID value of the Jamf configuration profile as an organization unit in each certificate and is especially important when mapping the certificate's common name to the seat ID value in Trust Lifecycle Manager.
Challenge Type: Select one of the following and fill in the options for it:
Static: Select this if your certificate profile in Trust Lifecycle Manager is configured to use a Global enrollment code. Enter the enrollment code in the Challenge and Verify Challenge inputs.
Dynamic-DigiCert Trust Lifecycle Manager: Select this if your certificate profile uses Dynamic enrollment codes. Configure the following fields:
PKI Instance: Select the applicable integration for your Trust Lifecycle Manager account as configured in your global Jamf Pro settings. Refer to the Prepare the integration section for more information.
Certificate Profile: Select the name of the profile to issue certificates from in Trust Lifecycle Manager. After making a selection, the GUID of the profile is shown for verification and so you can cross-check it against the certificate profile in Trust Lifecycle Manager.
Seat ID: Select the device identifier to use for the
Seat IDvalues in the corresponding seat records in Trust Lifecycle Manager. For example, select:Serial Number: To use Jamf Serial Numbers as the seat IDs.Device UDID: To use Jamf UDID (Unique Device Identifier) values as the seat IDs.
Seat Type: Select one of the following seat types for the certificate profile in Trust Lifecycle Manager, depending on the base template used to create the profile:
User: If the profile was created from theGeneric User Certificatebase template.Device: If the profile was created from theGeneric Device Certificatebase template.警告
Make sure the seat type you select matches the profile, otherwise certificate enrollments may fail.
(Optional) Make additional selections if needed to match the configuration of your certificate profile in Trust Lifecycle Manager.
Select Save on the bottom-right to save the new Jamf configuration profile.
To start enrolling computers/devices and users from the Jamf profile, configure the scope of the profile:
In the Jamf Pro portal, navigate to either the Computers or Devices tab, depending on where your devices are set up.
Select Content Management > Configuration Profiles.
Select the configuration profile.
Select Edit on the bottom-right.
Select the Scope tab below the profile name at top.
To set the scope, update the Target selections for computers/devices or users to one of the following:
All: Allow all computers/devices or users to enroll from the profile.
Specific: Allow only specific computers/devices or users to enroll:
Use the Add button to add the target computers/devices or users that can get certificates from this configuration profile.
Under Add Deployment Targets, select individual targets or target groups to enroll.
重要
Important notes:
DigiCert recommends setting the scope to Specific and using Smart Groups to control which computers/devices or users can get certificates.
To avoid issues from enrolling too many devices at once, select and apply target Smart Groups one at a time or in small batches. For more details, refer to the Distribute the Jamf profile to more targets section below.
Select Save on the bottom-right to apply your changes.
The Jamf configuration profile gets distributed to all the selected targets, prompting them to enroll certificates from Trust Lifecycle Manager.
To avoid issues from enrolling too many devices at once, distribute the Jamf configuration profile to Smart Groups one at a time or in small batches. After enrolling one group of devices, update the profile scope to distribute it to the next group.
To distribute the Jamf profile to the next group of devices:
In the Jamf Pro portal, navigate to either the Computers or Devices tab, depending on where your devices are set up.
Select Content Management > Configuration Profiles.
Select the configuration profile.
Select Edit on the bottom-right.
Select the Scope tab below the profile name at top.
Update the Target selections to add the new target computers/devices or users to enroll.
Select Save on the bottom-right to apply your changes.
In the Redistribution Options dialog, select one of the following options:
Distribute to All: The Jamf configuration profile gets distributed to all target devices, even those that already have the profile installed. This causes all the devices to enroll new certificates from Trust Lifecycle Manager.
Distribute to Newly Assigned Devices Only: The Jamf configuration profile only gets distributed to the newly selected target devices. Only the new devices you added will enroll certificates from Trust Lifecycle Manager.
重要
DigiCert recommends enrolling certificates in rolling groups, using the Distribute to Newly Assigned Devices Only option.
Select Save to finish and distribute the configuration profile to the selected targets, based on the selected distribution option.
Repeat this process to enroll the next group of devices.
Verify certificate enrollments
After enrolling a target device, verify the certificate got issued in Trust Lifecycle Manager and provisioned by Jamf Pro.
To view the issued certificate in Trust Lifecycle Manager:
Go to your Inventory page.
Use the view functions to display the certificate, filtering by fields such as the Common name or Seat ID.
Select a certificate by its Common name to see more details about it.
To verify profile distribution and certificate issuance for a single computer or device in the Jamf Pro portal:
In the Jamf Pro portal, navigate to either the Computers or Devices tab, depending on where your devices are set up.
Select Inventory > Search Inventory.
Select the Search button on the top-right.
Select the computer or device from the list to see the details for it.
Verify details in the computer or device record:
Inventory > Profiles: Lists all the configuration profiles installed on the device, including the identifier for each. If you configured your profiles to enable SCEP redistribution, this is the IDENTIFIER value that gets added as an organization unit (OU) in the certificate subject.
Inventory > Certificates: Lists all the certificates installed on the device, including expiration date and status of each. Select a certificate to see more details about it.
Management > Management Commands: Review this tab to see the deployment status of a Jamf configuration profile, including any errors that have been reported to Jamf Pro from DigiCert.
To see all certificates issued through Trust Lifecycle Manager in your Jamf Pro account:
More information
For more information about the integration, refer to the following Jamf technical paper: Integrating with DigiCert Using Jamf Pro.