Change log: 2023
2023 changes
December 15, 2023
CertCentral: Improvements to the Reissue SSL/TLS certificate process
We updated the process for reissuing SSL/TLS certificates in CertCentral. Now, if certificate revocations are required after reissuing your certificate, we do the following:
Send the requestor a revocation warning email with the subject line: Reissue request will revoke previously issued certificate for order ###### within 72 hours.
Change the Certificate status to Revocation pending with the revocation date and time on the Certificate history page.
Learn more about reissuing an SSL/TLS certificate
Background
When reissuing an SSL/TLS certificate, some changes may require DigiCert to revoke the original certificate and any reissues and duplicates, for example, removing a domain. In CertCentral, we warn you when a change will revoke your certificates.
December 13, 2023
CertCentral Services API: Secure Email (S/MIME) certificate enhancements
We're pleased to announce several enhancements to the API workflows for requesting and reissuing Secure Email (S/MIME) certificates:
Reject orders when DigiCert can't immediately issue the certificate
We updated the Order Secure Email certificate endpoint to support a new request parameter:
reject_if_pending. Iftrue, when DigiCert can't issue and return the certificate immediately, the API returns an error instead of creating the order in a pending state.Get certificates with an RSASSA-PSS signature
We updated the Order Secure Email certificate endpoint to support a new request parameter:
is_rsassa_pss. Iftrue, DigiCert issues the certificate with an RSASSA-PSS signature type.Nota
To get an RSASSA-PSS signature, the issuing ICA must have an RSA signature.
Include a user principle name (UPN) in the SAN extension for Secure Email for Business certificates
We updated the Order Secure Email certificate endpoint to support a new request parameter:
user_principle_name. Include this parameter in thecertificateobject to set the value of the UPN SAN attribute on Secure Email for Business certificates. For example:Nota
Currently, you may include only a single value in the
user_principle_namearray.Include additional subject DN attributes
We updated the Order Secure Email certificate endpoint to support a new object in the request body:
subject. Use thesubjectobject to submit values for optional subject DN attributes, such asemail(supported for all Secure Email products) andtitle,serial number, orpseudonym(supported for Secure Email for Business certificates only).Reissue Secure Email certificates
We updated the Reissue certificate API reference to include details about the request parameters used to reissue a Secure Email certificate.
December 12, 2023
CertCentral: Improvements to the verified contact approval step on pending EV TLS/SSL certificate requests
We are happy to announce we improved the verified contact approval process for approving EV TSL/SSL certificate orders in CertCentral. We updated the Order details page to make completing the verified contact approval step easier on your pending EV TLS certificate requests.
Improvements:
After sending the approval email to the verified contacts, we add a pending Order Approval task under What do you need to do.
We include a Resend approval email link that allows you to do the following:
See who the approval email was sent to the last time it was sent.
Resend the approval email and choose which verified contacts it's sent to.
We include the date the approval email was last sent.
The order status remains pending until you and DigiCert complete all necessary tasks on the request.
Under What does DigiCert need to do, the Verify all EV contacts task shows the verification status of the verified contacts on the request.
Background
Before DigiCert can issue an EV TLS/SSL certificate, a verified contact representing the organization included on the certificate must approve the pending certificate request (new, reissue, and new).
Previously, there was a lack of verified contact transparency on these pending requests:
The order details page lacked information about the verified contact approval step.
You had to contact support to find out who the approval email was sent to and to resend it.
When the verified contact approval step was the only step remaining on the pending order, the order status changed to Finalizing Certificate.
See for yourself
In your CertCentral account, in the left main menu, go to Certificates > Orders.
On the Orders page, select a pending EV TLS/SSL certificate order.
Note that if the certificate requestor is a verified contact for the organization, the EV approval step is automatically completed when they place the request. On the Order details page, the Order Approval task will be marked as completed.
On the certificate's Order details page, you should see the improvements as they are required on the pending request.
Resources
December 8, 2023
CertCentral Services API: New delete organization endpoint
In the CertCentral Services API, we added a new API endpoint for deleting an organization from your CertCentral account. For examples and usage details, visit the API reference: Delete organization.
December 7, 2023
CertCentral: New delete organizations feature
We are happy to announce that we have improved the organization management workflow.
Want to remove an organization from your account that you can never validate because of a typo or misspelling? Want to remove a deprecated organization from your account?
Now, when you need to delete an organization from your CertCentral account, you can. Go to the Organizations page and use the Delete organization feature to delete one or multiple organizations simultaneously.
Previously, you could only deactivate organizations. The Deactivate organization feature allows you to block certificate issuance for an organization until it’s activated. However, the deactivated organization remains in your account.
Items to note about deleting organizations
Only CertCentral administrators can delete organizations.
Deleting an organization hides it from the list of organizations.
Deleting an organization also deletes any domains associated with the organization from your account.
Current certificates that include a deleted organization:
Remain valid until they expire or are revoked.
Cannot be reissued or duplicated.
You cannot delete an organization included on a pending certificate request or pending order.
Requesting new or renewal certificates for a deleted organization will require you to revalidate the organization.
See for yourself
In your CertCentral account, in the left main menu, go to Certificates > Organizations.
On the Organizations page, in the Name column, select the organization you want to delete.
On the Organization details page, in the More actions dropdown, select Delete organization.
In the Delete organization window:
Select Delete organization to delete the organization from your account.
Select Cancel to keep the organization in your account.
Resources
December 6, 2023
CertCentral: End of life for existing automation profiles and ACME Directory URLs configured for 4- to 6-year Multi-year Plans
On December 6, 2023, at 10:00 MDT (17:00 UTC), CertCentral will no longer support existing TLS certificate automation profiles or ACME Directory URLs configured for 4- to 6-year Multi-year Plans. Automation requests that use these retiring automation profiles or ACME Directory URLs will fail.
Background
On October 31, 2023, DigiCert stopped selling new 4- to 6-year Multi-year Plans. Automation and ACME customers configured for 4- to 6-year orders have until December 6 to reconfigure their existing automation profiles and ACME clients to use 1- to 3-year orders instead.
What do I need to do?
Automation profiles
Starting on December 6, existing automation profiles configured for 4 to 6 years of coverage will show an Action needed status and automation requests for these profiles will fail. To avoid outages, you must reconfigure these automation profiles before December 6 to have a coverage length of 1 to 3 years.
To reconfigure automation profiles in the CertCentral console:
For instructions on how to update an existing automation profile, see Edit an automation profile.
On the automation profile edit screen, select the pencil icon in the Multi-year plan details field to edit and select a new coverage length of 1 to 3 years.
To use the API to reconfigure automation profiles:
To update an existing automation profile, see Update profile details.
Use the orderCoverageLength request parameter to update the coverage length of the profile to
1Y,2Y, or3Y.
ACME clients
Starting on December 6, existing ACME Directory URLs for 4 to 6 years of coverage will no longer work. To avoid outages, you must reconfigure any third-party ACME clients that use these retiring credentials to use a replacement ACME Directory URL for 1 to 3 years of coverage.
Consult the documentation for your third-party ACME client for help reconfiguring it. For example, the Certbot documentation is found at https://eff-certbot.readthedocs.io
You can use any ACME Directory URL for 1 to 3 years of coverage to continue requesting certificates with your third-party ACME clients. If you don't already have a suitable replacement ACME Directory URL in your CertCentral account, create a new one to use.
To create an ACME Directory URL in the CertCentral console:
For instructions on how to create a new ACME Directory URL, see Create one or more ACME Directory URLs.
When setting the properties of certificates issued through this ACME Directory URL, select a coverage length of 1 to 3 years in the Multi-year coverage length field.
To use the API to create an ACME Directory URL:
To generate a new ACME Directory URL and External Account Binding (EAB) credentials, see ACME External Account Binding.
Use the order_validity_days or order_validity_years request parameter to set the coverage length of the new ACME Directory URL to a maximum of 3 years.
December 5, 2023
CertCentral two-factor authentication: One-time password email verification authentication method
We are happy to announce that we added the One-time password email verification authentication method to our two-factor authentication requirements in CertCentral.
One-time password email verification authentication method
By default, CertCentral requires you to use your credentials (username and password) and a one-time password (OTP app) to access your account. Now, you can also add OTP email verification as a one-time password (OTP) requirement.
After you enter your credentials, CertCentral sends a temporary password to the email address in your CertCentral account Profile Settings. To access your account, enter the temporary passcode in the verification email.
DigiCert 2024 maintenance schedules
To make it easier to plan your certificate-related tasks, DigiCert has scheduled our 2024 maintenance windows in advance.
We keep these pages up to date with the latest maintenance schedule information:
With customers worldwide, we understand there is no "best time" for everyone. However, after reviewing the data on customer usage, we selected times that would impact the fewest amount of our customers.
About our maintenance schedules
Maintenance is scheduled for the first weekend of each month unless otherwise noted.
Each maintenance window is scheduled for 2 hours.
Although we have redundancies to protect your service, some DigiCert services may be unavailable.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance begins and when it ends.
Contact your account manager or DigiCert Support if you need more information regarding these maintenance windows.
December 4, 2023
December 2, 2023
Upcoming scheduled Europe maintenance
DigiCert will perform scheduled maintenance on December 2, 2023, 09:00 – 11:00 MST (16:00 – 18:00 UTC).
Importante
Maintenance will be one hour later for those who don't observe daylight savings.
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page to get live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2023 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
DigiCert will perform scheduled maintenance on December 2, 2023, 22:00 – 24:00 MDT (December 3, 2023, 05:00 – 07:00 UTC).
Importante
Maintenance will be one hour later for those who don't observe daylight savings.
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page to get live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert global 2023 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
November 20, 2023
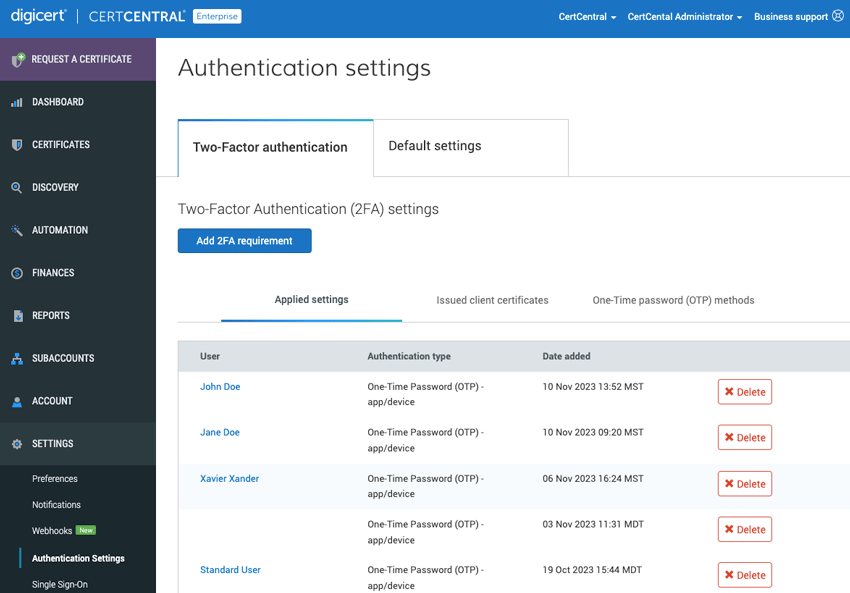
CertCentral: Improved two-factor authentication user interface
We are happy to announce that we improved the process for creating, viewing, and updating your two-factor authentication requirements in CertCentral. See our CertCentral two-factor authentication guide.
New layout and organization of rules and settings
We updated the layout, moving to a tab-style page structure to make it easier to create, view, and update the two-factor authentication requirements for your CertCentral users. Now, when you visit the Authentication settings page (in the left main menu, go to Settings > Authentication Settings), instead of scrolling to find information, you can select what you want to view:
Two-factor authentication
Add a two-factor authentication requirement
Applied settings
Issued client certificates
One-time password (OTP) methods
Default settings
Password settings
One-time password (OTP) settings
November 4, 2023
Upcoming scheduled Europe maintenance
DigiCert will perform scheduled maintenance on November 4, 2023, 09:00 – 11:00 MDT (15:00 – 17:00 UTC).
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance starts and when maintenance ends.
See the DigiCert Europe 2023 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
DigiCert will perform scheduled maintenance on November 4, 2023, 22:00 – 24:00 MDT (October 8, 2023, 04:00 – 06:00 UTC).
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance starts and when maintenance ends.
See the DigiCert global 2023 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
October 31, 2023
CertCentral: Changes to Multi-year Plan coverage
On October 31, 2023, DigiCert will no longer sell 4 – 6-year Multi-year Plans for TLS and VMC certificates. We will continue to offer 1, 2, and 3-year Multi-year Plans.
How does this affect me?
For those with existing 4, 5, and 6-year Multi-year Plans, this change does not affect your coverage. You can continue to reissue and duplicate issue certificates for your Multi-year Plan until it expires.
For example, if you purchased a 5-year Multi-year Plan on April 1, 2023, you have coverage until April 1, 2028.
What if I use the CertCentral Services API?
If you use the CertCentral Services API to create 4, 5, and 6-year orders for TLS/SSL or Verified Mark certificates, you need to update your API integrations and remove the 4, 5, and 6-year coverage options from your Multi-year Plan integrations.
For more information, see End of 4 - 6-year Multi-year Plans.
What if I use certificate lifecycle automation tools with 4, 5, and 6-year Multi-year Plans?
Starting on October 31, you can no longer create new automation profiles or ACME Directory URLs for a certificate coverage length of 4 to 6 years. To avoid outages, you have until December 6, 2023 to reconfigure any existing automation profiles or third-party ACME clients that use a 4 to 6 year coverage length to instead use a new coverage length of 1 to 3 years.
What happens when I need to renew my Multi-year Plan?
When it’s time to renew your Multi-year Plan, you can renew it as a 1, 2, or 3-year Multi-year Plan.
Why will DigiCert stop selling 4, 5, and 6-year Multi-year Plans?
We are optimizing our infrastructure to support new and improved e-commerce experiences. Removing these Multi-year Plan options helps us streamline existing product lines into a cleaner, more intuitive shopping environment.
October 19, 2023
CertCentral webhooks: Get webhook notifications in Slack
We’re happy to announce that you can now receive CertCentral webhook notifications in Slack!
When you integrate CertCentral webhooks with Slack, your webhook sends notifications to a channel in your Slack workspace. These notifications have the same triggers and data as standard webhook events, and Slack presents the information as human-readable text instead of raw JSON.
Nota
DigiCert will continue improving the content and formatting of Slack webhook messages to meet customer needs.
Learn more: Get webhook notifications in Slack
October 17, 2023
DigiCert site seal is replacing the Norton site seal
On October 17, 2023, at approximately 10:00 MDT (16:00 UTC), DigiCert will replace the Norton site seal image with our DigiCert site seal image wherever it appears on websites secured by Secure Site or Secure Site Pro TLS certificates. Additionally, we will remove the option to use and download the Norton site seal from CertCentral.
What do I need to do?
No action is required. DigiCert will automatically replace your static Norton site seal image with the DigiCert site seal image on October 17, 2023, at 10:00 MDT (16:00 UTC). However, DigiCert recommends replacing your Norton site seal with the DigiCert Smart Seal.
To use the Smart Seal image, you must install the DigiCert site seal code on your website. To learn more about using the DigiCert Smart Seal, see the following instructions:
Why should I use the enhanced DigiCert Smart Seal?
To make the Smart Seal more interactive and engaging, we added a hover-over effect, animation, and the ability to display your company logo in the site seal.
Hover-over effect
When visitors hover over the seal, it magnifies and gives customers quick information about your organization.
Animation
When visitors come to your site, the seal slowly transitions from the seal image to the additional details about your organization.
Logo
Add your logo to the hover-over effect and the site seal animation. Your logo appears with additional details about your organization. DigiCert must approve your logo before it appears in the Smart Seal on your website.
See The Smartest Way to Boost Trust at Checkout to learn more about the DigiCert Smart Seal.
October 13, 2023
CertCentral: New delete domains feature
We are happy to announce that we improved the domain management workflow in CertCentral.
Want to remove a domain from your account that you can never validate because it has a typo? Want to remove all the subdomains of a base domain?
Now, when you need to delete a domain from your CertCentral account, you can. Go to the Domains page and use the Delete domain feature to delete one or multiple domains simultaneously.
Previously, you could only deactivate domains. The Deactivate domain feature allows you to block certificate issuance for a domain until it’s activated. However, the deactivated domain remains in your account.
Items to note about deleting domains:
Only CertCentral administrators can delete domains.
Deleting a domain hides it from the list of domains.
Current certificates that include the domain are not affected.
Requesting new, reissue, or renewal certificates for a deleted domain may require you to revalidate the domain.
See for yourself
In your CertCentral account, in the left main menu, go to Certificates > Domains.
On the Domains page, in the Domain name column, select the domain you want to delete.
On the Domain details page, in the Deactivate domain dropdown, select Delete domain.
In the Delete domain window, select Delete domain if you want to delete the domain. Select Cancel if you don’t want to delete it.
Resources
CertCentral Services API: New delete domain endpoint
In the CertCentral Services API, we added a new API endpoint for deleting a domain from your CertCentral account. For examples and usage details, visit the API reference: Delete domain.
October 10, 2023
CertCentral Services API: Added functionality to Update order status endpoint
In the CertCentral Services API, we added new functionality to the Update order status API endpoint. Now, if you use the Services API to manage certificate request approvals, you can use the Update order status endpoint to cancel reissue requests that are pending admin approval. Before, this endpoint could only cancel reissues after an administrator approved the request.
For example, the order 12345 has a pending request to reissue the certificate on the order. You can use this cURL request to both cancel the reissue and reject the request:
curl -X PUT \
'https://www.digicert.com/services/v2/order/certificate/12345/status' \
--header 'Content-Type: application/json' \
--header 'X-DC-DEVKEY: {{api_key}}' \
--data-raw '{
"status": "canceled",
"note": "Reissue canceled"
}'When you submit this request:
The reissue is canceled, and the
statusof order12345changes fromreissue_pendingback toissued.The
statusof the correspondingrequestbecomesrejected.The
note(if provided) from the Update order status payload is stored in theprocessor_commentfield on the rejectedrequest.
October 7, 2023
Upcoming scheduled Europe maintenance
DigiCert will perform scheduled maintenance on October 7, 2023, 09:00 – 11:00 MDT (15:00 – 17:00 UTC). Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, including email alerts for when maintenance starts and ends, subscribe to the DigiCert Status page.
See the DigiCert Europe 2023 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
DigiCert will perform scheduled maintenance on October 7, 2023, 22:00 – 24:00 MDT (October 8, 2023, 04:00 – 06:00 UTC). Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, including email alerts for when maintenance starts and ends, subscribe to the DigiCert Status page.
See the DigiCert global 2023 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
September 11, 2023
CertCentral: Updates to client certificate request forms per new industry requirements
With the recent industry changes to S/MIME certificates, we updated our client certificate requests form, making it easier to include the required information to get your certificate.
Now, when you request one of the certificates listed below, you will see two options under Certificate to Request(s):
Email: Enter the email address you want to secure and appear as the certificate's common name.
Name: Enter the recipient's name as the common name and the email address you want to secure.
Affected certificates: Premium, Email Security Plus, and Digital Signature Plus.
See for yourself:
In the left main menu, hover over Request a Certificate.
Then, under Client certificates, select the client certificate you want to order: Premium, Email Security Plus, or Digital Signature Plus.
To learn more, see Order your client certificate.
Background
On August 29, 2023, at 10:00 MDT (16:00 UTC), DigiCert updated our public Secure Email (S/MIME) certificate issuance process to comply with the CA/Browser Forum's new Baseline Requirements for the Issuance and Management of Publicly‐Trusted S/MIME Certificates.
Industry changes now place certificates used to sign, verify, encrypt, or decrypt email into three categories:
Sponsor-validated – Secure Email (S/MIME) for an organization to issue to its organization-sponsored individuals
Organization-validated – Secure Email (S/MIME) certificate for an organization
Mailbox-validated – Secure Email (S/MIME) certificates for individuals
Our Premium, Email Security Plus, and Digital Signature Plus certificates are in the sponsor-validated category. Thus, you can only enter your email address or name as the common name on the certificate.
Learn more about the New industry requirements for public Secure Email (S/MIME) certificates.
September 9, 2023
Upcoming scheduled global maintenance
Some DigiCert services will be down for 60 minutes during scheduled maintenance on September 9, 2023, 22:00 – 24:00 MDT (September 10, 04:00 – 06:00 UTC).
Document Trust Manager PrimoSign signing service maintenance-related downtime
The Document Trust Manager maintenance starts at 22:00 MDT (04:00 UTC). At this time, the PrimoSign signing service will be down for up to 60 minutes.
Affected services
DigiCert ONE USA
Document Trust Manager PrimoSign signing service
What can I do?
Plan accordingly:
Schedule high-priority document signings before or after the maintenance window.
Expect interruptions if you use the APIs for automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance starts and when maintenance ends.
See the DigiCert global 2023 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
September 5, 2023
Industry changes to TLS certificates' BasicConstraints extension
On September 5, 2023, at 10:00 MDT (16:00 UTC), DigiCert will only issue public TLS certificates with the BasicConstraints extension set to critical per new industry requirements. Going forward, we will stop supporting the BasicConstraints extension's noncritical setting in public TLS certificate profiles.
Why is DigiCert making this BasicConstraints extension change?
To comply with industry changes mandated by the root program, all certificate authorities (CAs), such as DigiCert, must stop allowing users to set the BasicConstraints extension to noncritical in public TLS certificates.
For more details about the compliance changes affecting the BasicConstraints extension in certificate profiles, see the CA/Browser Forum's Ballot SC62v2-Certificate profiles update.
How does this affect me?
Does your TLS certificate process require the BasicConstraints extension to be set to noncritical?
No, it does not.
You shouldn't notice any difference in your certificate issuance process. Your public TLS certificates are not affected by this change.
Yes, it does.
You can continue to include the BasicConstraints extension set to noncritical in your public TLS certificate issued before September 5, 2023. Make sure to complete the required domain and organization validation for these orders before September 5.
What if I need the BasicConstraints extension set to noncritical in my TLS certificates after September 5?
You can use private TLS certificates. The root-program BasicConstraints extension change does not apply to private TLS certificates. If private TLS certificates meet your needs, contact your account manager to make sure the correct Private Root CA hierarchy is available for your account.
How does this affect my public TLS certificates with the BasicConstraints extension set to noncritical?
Your existing certificates are not affected by this change. However, if you reissue, duplicate issue, or renew a certificate after September 5, 2023, 10:00 MDT (16:00 UTC), we will set the BasicConstraints extension to critical when we issue the certificate.
How does this affect my API integration?
In the Services API, order requests for public TLS certificates that specify a certificate.profile_option of basic_constraints_critical_true will return a 400 error with an error code value of invalid_profile_option.
Update your API integration and remove the basic_constraints_critical_true profile option from your public TLS certificate requests by September 5, 2023.
End of issuance for individual validation TLS certificates
On September 5, 2023, at 10:00 MDT (16:00 UTC), DigiCert will stop issuing individual validation TLS certificates. This means you can no longer get an organization validation (OV) TLS certificate with a person's name in the subject field.
Affected certificates:
Secure Site Pro SSL
Secure Site OV
Basic OV
GeoTrust® TrueBusiness ID OV
Thawte® SSL Webserver OV
Why will DigiCert stop issuing individual validation TLS certificates?
To comply with industry changes mandated by the root program, DigiCert will only issue OV TLS certificates with an organization name in the subject field. For more details about the compliance changes affecting the individual validation TLS certificates, see the CA/Browser Forum's Ballot SC62v2-Certificate profiles update.
How does this affect me?
Your existing individual validation OV TLS certificates will continue to secure your domains until they expire. This change doesn't apply to certificates issued prior to September 5, 2023.
However, starting September 5, you cannot reissue, duplicate, or renew an existing individual validation OV TLS certificate. You can still revoke a certificate if needed.
What if I need a new individual validation TLS certificate?
Get needed certificates before September 5.
You can continue to include your name in OV TLS certificates issued before September 5. Make sure to complete the required domain and individual validation for these orders by September 5.
Use domain validation (DV) TLS certificates.
Starting September 5, 2023, if you need a TLS certificate for an individual, we recommend purchasing a DV TLS certificate instead. On September 5, 2023, we will enable the GeoTrust DV SSL certificate for your CertCentral account.
September 2, 2023
Upcoming scheduled Europe maintenance
Some DigiCert services will be down for 90 minutes during scheduled maintenance on September 2, 2023, 09:00 – 11:00 MDT (15:00 – 17:00 UTC).
Document Trust Manager's PrimoSign signing service maintenance-related downtime
The DigiCert® Document Trust Manager maintenance starts at 09:00 MDT (15:00 UTC). At that time, the PrimoSign signing service will be down for up to 90 minutes.
Affected services:
DigiCert ONE Netherlands instance
DigiCert® Document Trust Manager PrimoSign signing service
DigiCert ONE Switzerland instance
DigiCert® Document Trust Manager PrimoSign signing service
What can I do?
Plan accordingly
Schedule high-priority document signings before or after the maintenance window.
Expect interruptions if you use the APIs for automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance starts and when maintenance ends.
See the DigiCert Europe 2023 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
August 29, 2023
Changes coming for public Secure Email (S/MIME) certificates
On August 29, 2023, at 10:00 MDT (16:00 UTC), DigiCert will make the changes listed below to our public Secure Email (S/MIME) certificate issuance process to comply with the CA/Brower Forum's new Baseline Requirements for the Issuance and Management of Publicly‐Trusted S/MIME Certificates.
These changes will apply to all newly issued certificates containing the emailProtectionextentedKeyUsage and at least one email address. If you can use your certificate to sign, verify, encrypt, or decrypt email, then your new, reissued, and renewed certificates will be affected by these new industry requirements starting August 29, 2023, at 10:00 MDT (16:00 UTC).
What can I do?
Get needed Secure Email S/MIME certificates before August 29, 2023
If you have S/MIME certificate renewals, reissues, or new orders scheduled for the end of August and the month of September, do these certificate-related activities early—before August 29. That way, your S/MIME certificate issuance will remain the same, eliminating potential surprises from the modifications to certificate profiles and the validation process. Certificates issued before August 29, 2023, can still contain the organization unit information and email-validated addresses, as needed.
Move to private Secure Email (S/MIME) certificates
DigiCert recommends moving to privately trusted S/MIME certificates if public trust is not required. The rules for public S/MIME certificates do not apply to locally trusted S/MIME certificates. Contact your account representative or DigiCert Support to learn about DigiCert Private Secure Email (S/MIME) certificates.
Platform-specific changes
One of the benefits of the new S/MIME certificate baseline requirements is that it will standardize public S/MIME certificates for all certificate authorities and, more specifically, for all DigiCert platforms.
To learn more about the changes coming to your platform and what you need to do to prepare for the changes to DigiCert's public Secure Email (S/MIME) certificate issuance process, see the applicable section of our knowledge base article:
CertCentral: Document Signing Certificate changes
On August 29, 2023, at 10:00 MDT (16:00 UTC), DigiCert will no longer include the email addresses in the subject field when issuing Document Signing certificates.
Starting August 29:
You can no longer use the newly issued Document Signing certificate to sign your emails.
Your email address will not appear in signatures applied to documents using a newly issued or reissued Document Signing certificate.
The following certificates are affected by this change:
Document Signing - Organization (2000/5000)
Document Signing - Individual (500/2000)
Why will DigiCert start issuing Document Signing certificates without the email address in the subject?
We are making this change to align with upcoming industry changes affecting the issuance and management of publicly trusted secure email (S/MIME) certificates.
Starting August 29, under the new S/MIME certificate requirements, a document signing certificate must undergo a new validation process for digitally signing emails. DigiCert's Document Signing certificates do not include this validation process and, therefore, can no longer include email addresses and be used to sign emails after August 29.
How do these changes affect my Document Singing certificates?
Newly issued Document Signing certificates.
Starting August 29, 2023, at 10:00 MDT (16:00 UTC), all newly issued Document Signing certificates, including new, reissued, and renewed certificates, will no longer include the email addresses in the subject field and can no longer be used to sign emails.
Existing Document Signing certificates.
The industry changes do not affect Document Signing certificates issued before August 29, 2023, 10:00 MDT (16:00 UTC). You can continue to use these existing certificates to sign emails if needed until they expire. Remember, starting August 29, the changes to Document Signing certificates will affect your certificate replacements and renewals.
What can I do?
Get needed Document Signing certificates with email signing before August 29, 2023.
If you have Document Signing renewals, reissues, or new orders scheduled for the end of August and September, do these certificate-related activities before August 29. That way, your Document Signing certificates will include the email address and can be used to sign emails.
Get a Secure Email (S/MIME) certificate.
If you need a certificate to sign your emails, get one of DigiCert's secure email certificates that meets the new S/MIME requirements. These certificates will be available for purchase in CertCentral starting August 29.
August 22, 2023
CertCentral: Only show "Comments to Administrator" when the approval step is enabled for a user
In CertCentral, we updated our OV TLS, EV TLS, code signing, and document signing certificate request forms. Now, we will only include the Comments to Administrator field when the approval step is enabled for the user making the request.
This field allows you to provide additional information to the person approving the request. When an order skips the approval step, the field no longer serves its purpose.
Background
By default, CertCentral accounts are configured for one-step certificate request approvals. An account administrator must approve a certificate request before DigiCert can process the order (validating the organization, etc.).
However, on the Preferences page (go to Settings > Preferences), in the Certificate Requests section, you can remove the approval step from the OV and EV TLS, code signing, and document signing certificate issuance workflows for your CertCentral administrators and managers. Even with skip approval enabled, you must still approve requests submitted by standard users, limited users, and finance managers.
August 15, 2023
Industry changes to key usage extensions allowed in Public TLS certificates.
On August 15, 2023, at 10:00 MDT (16:00 UTC), DigiCert will stop supporting the following key usage extensions in public TLS certificates:
Data encipherment
Non-repudiation
Note that these key usage extensions are not included in public TLS certificates by default.
Why is DigiCert making these key usage extension changes?
To comply with industry changes mandated by the root program, all certificate authorities (CAs), such as DigiCert, must stop allowing users to include these key usage extensions in public TLS certificates: data encipherment and non-repudiation.
For more details about the compliance changes affecting key usage extensions in certificate profiles, see the CA/Browser Forum Baseline Requirements for the Issuance and Management of Publicly‐Trusted Certificates, Section 7.1.2.7.10.
How does this affect me?
Do you currently use these key usage extensions in your public TLS certificates?
No, I don't.
Then no action is required. Your public TLS certificates are not affected by this change.
Yes, I do.
You can continue to include the data encipherment or non-repudiation key usage extensions in your public TLS certificate issued until August 15, 2023. Make sure to complete the required domain and organization validation for these orders by August 15.
What if I need to include the data encipherment or non-repudiation key usage extensions in my TLS certificates after August 15?
You can use private TLS certificates. The root-program key usage extension change does not apply to private TLS certificates. If private TLS certificates will meet your needs, contact your account manager to make sure the correct Private root CA hierarchy is available for your account.
How does this affect my existing certificates that include these key extensions?
Your existing certificates are not affected by this change. However, if you reissue or duplicate issue a certificate with one of these key usage extensions after August 15, we will remove the data encipherment or non-repudiation extension before we reissue the certificate.
How does this affect my API integration?
In the Services API, order requests for public TLS certificates that specify a certificate.profile_option of data_encipherment, non_repudiation, or non_repudiation_and_data_enciph will return a 400 error with an error code value of profile_option_not_allowed.
Update your API integration and remove these profile options from your public TLS certificate requests by August 15, 2023.
Upgrading the DigiCert Support Plans
On August 15, 2023, DigiCert will upgrade our support plans to provide you with a better, more customizable experience. These plans are scalable and backed by our technical experts to ensure your success.
New plans:
Standard support
Our free support plan is available to all DigiCert customers. It includes 24-hour, Monday – Friday chat and email technical support and access to our comprehensive product documentation and developer portal hub, knowledge base articles, and other self-service tools.
Business support
Our mid-level paid service plan includes everything in our Standard plan plus 24-hour, Monday – Friday phone technical support, faster service hold times, and business service level agreements.
Premium support
Our highest-level paid service plan includes access to everything in the Business plan plus priority service hold time.
The Premium plan is the only plan that includes the following:
24-hour, 7-day-a-week technical support with local language service during business hours and English language services after hours.
Priority validation.
Access to DigiCert ONE testing environment.
Premium service level agreements.
Root cause analysis for service degradation incidents.
Access to a Premium Client Manager for one-on-one incident resolution, strategic planning, and project coordination.
For more details about what these plans include, see the following:
How does this affect me?
To show our appreciation, on August 15, 2023, DigiCert will upgrade all existing customers to either Business or Premium support plans for a limited time at no additional charge.
How the limited-time upgrade works:
Platinum support plans will be upgraded to Premium support for the duration of the contract.
You will receive validation SLAS in addition to your current support benefits. You will also retain your current Platinum Client Manager (now called a Premium Client Manager).
Gold or Platinum-Lite support plans will be upgraded to Premium support for the duration of your contract.
You will have all Premium support benefits except for a Premium Client Manager.
Included (non-paid) DigiCert support will be upgraded to Business support for up to one year.
On August 14, 2024, if you have not selected a new go-forward support plan, you can continue with a Business support plan, upgrade to a Premium support plan, or return to our free, Standard support plan.
Need help?
If you have questions or concerns, contact your account manager. See our knowledge base article.
August 8, 2023
CertCentral: Submitting organizations for SMIME – SMIME Organization Validation prevalidation
Starting August 8 at approximately 10:00 MDT (16:00 UTC), when you order a client certificate containing the emailProtection extentedKeyUsage and at least one email address, we will automatically submit the organization included in the order for SMIME organization prevalidation. When you visit the organization's details page, you will see a pending validation for SMIME – SMIME Organization Validation.
Affected client certificates:
Digital Signature Plus
Email Security Plus
Premium
Class 1 S/MIME
This change also affects orders submitted via the CertCentral Services API. To learn more about organization prevalidation, see our Submit an organization for prevalidation instructions.
Why is DigiCert submitting these organizations for SMIME prevalidation?
As part of the new requirements for public Secure Email (S/MIME) certificates, certificate authorities (CAs), such as DigiCert, must validate the organization included in a certificate containing the emailProtection extentedKeyUsage and at least one email address for S/MIME validation before we can issue the certificate.
DigiCert will submit organizations included in these types of certificate requests for SMIME organization prevalidation starting August 8 to prepare for these new requirements.
How does this affect my client certificate process?
The pending SMIME organization validation does not prevent your client certificates from being issued at this time. Until we update our process, for client certificates containing the emailProtection extentedKeyUsage and at least one email address, DigiCert will continue to require OV - Normal Organization Validation to validate the organization included in the certificate.
Then starting August 29, 2023, DigiCert must validate the organization included in these client certificates for the new SMIME organization validation before we can issue them.
OV - Normal Organization Validation
Per industry requirements, DigiCert will continue to validate the organization included in a certificate containing the emailProtection extentedKeyUsage and at least one email address for OV - Normal Organization Validation until August 29.
SMIME – SMIME Organization Validation
Starting August 29, 2023, at 10:00 MDT (16:00 UTC), all newly issued certificates containing the emailProtection extentedKeyUsage and at least one email address, including new, reissued, and renewed certificates, must comply with the new Baseline Requirements for the Issuance and Management of Publicly‐Trusted S/MIME Certificates.
CertCentral Webhooks: Include certificate and chain in certificate issued events
CertCentral webhooks now support the option to include the certificate chain in certificate_issued events for public and private TLS/SSL certificates.
Now, you can get your issued TLS certificate in the same webhook event that notifies you the certificate is ready. Before, you needed to trigger a callback API request to download the certificate from CertCentral.
Example certificate_issued event with certificate chain:
{
"event": "certificate_issued",
"data": {
"order_id": 1234,
"certificate_id": 1234,
"certificate_chain": [
{
"subject_common_name": "example.com",
"pem": "-----BEGIN CERTIFICATE-----\r\nMII...\r\n-----END CERTIFICATE-----\r\n"
},
{
"subject_common_name": "DigiCert Global G2 TLS RSA SHA256 2020 CA1",
"pem": "-----BEGIN CERTIFICATE-----\r\nMII...\r\n-----END CERTIFICATE-----\r\n"
},
{
"subject_common_name": "DigiCert Global Root G2",
"pem": "-----BEGIN CERTIFICATE-----\r\nMII...\r\n-----END CERTIFICATE-----\r\n"
}
]
}
}Nota
CertCentral only sends the certificate chain in certificate_issued events for public and private TLS/SSL certificates. For other product types, certificate_issued events never include the certificate chain.
Learn how to include the certificate chain in certificate_issued events: Customize certificate issued events.
CertCentral Services API: Add issuing CA certificate details to subaccount order info response
In the CertCentral Services API, we updated the Subaccount order info API endpoint to return the name and id of the issuing CA certificate for the primary certificate on the order. This data is returned in the ca_cert object in the certificate section of the JSON response.
Example JSON response with ca_cert object, truncated for brevity:
{
"certificate": {
"ca_cert": {
"id": "A937018B9FAF6CC2",
"name": "DigiCert Global G2 TLS RSA SHA256 2020 CA1"
},
...
},
...
}
CertCentral Services API: Add product shim details to subaccount product list
In the CertCentral Services API, we updated the List subaccount products API endpoint to return details about the product shims configured for the subaccount.
Nota
CertCentral uses product shims to map requests for legacy products to the newer products that replaced them.
Now, the List subaccount products API endpoint returns these parameters:
is_product_shim_enabled(boolean): Returned at the root of the JSON response. If true, product shims are configured for the subaccount. Otherwise, false.product_shim_map(array of objects): In theproductslist, any product with legacy products mapped to it returns aproduct_shim_maparray. This array is a list of objects with theproduct_name_idandproduct_nameof the legacy product with an active shim.
Example JSON response, truncated for brevity:
{
"currency": "JPY",
"pricing_method": "custom",
"balance_negative_limit": "-1",
"products": [
{
"product_name_id": "ssl_dv_geotrust_flex",
"product_name": "GeoTrust DV SSL",
"product_shim_map": [
{
"product_name_id": "ssl_dv_geotrust",
"product_name": "GeoTrust Standard DV"
}
],
},
{
"product_name_id": "ssl_securesite_flex",
"product_name": "Secure Site OV",
"product_shim_map": [
{
"product_name_id": "ssl_plus",
"product_name": "Standard SSL"
},
{
"product_name_id": "ssl_securesite",
"product_name": "Secure Site SSL"
}
],
},
...
],
"is_product_shim_enabled": true
}August 5, 2023
Upcoming scheduled Europe maintenance
Some DigiCert services will be down for up to 30 minutes, while others may experience interruptions during scheduled maintenance on August 5, 2023, 09:00 – 11:00 MDT (15:00 – 17:00 UTC).
Upcoming scheduled global maintenance
DigiCert will perform scheduled maintenance on August 5, 2023, 22:00 – 24:00 MDT (August 6, 2023, 04:00 – 06:00 UTC). Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance starts and when maintenance ends.
See the DigiCert global 2023 maintenance schedule for scheduled maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
August 1, 2023
CertCentral: New SMIME – SMIME Organization Validation
In CertCentral, we added a new validation type to the organization prevalidation workflow, SMIME – SMIME Organization Validation. Starting August 29, 2023, DigiCert must validate the organization included in Secure Email (S/MIME) certificates with the new validation type, SMIME – SMIME Organization Validation, before we can issue the certificate. To learn more about organization prevalidation, see our Submit an organization for prevalidation instructions.
Why is DigiCert adding SMIME – SMIME Organization Validation?
As part of the new requirements for public Secure Email (S/MIME) certificates, certificate authorities (CAs), such as DigiCert, must validate the organization included in a Secure Email certificate for S/MIME validation before we can issue the certificate.
How does this affect my client certificate process?
DigiCert will continue to require OV - Normal Organization Validation to validate the organization included in a Secure Email (S/MIME) certificate until we update our process on August 29, 2023. Then, we will require the organization included in a Secure Email certificate to be validated for the new SMIME – SMIME Organization Validation.
OV - Normal Organization Validation
Per the current industry requirements, DigiCert will continue to validate the organization included in Secure Email (S/MIME) certificates for OV - Normal Organization Validation until August 29.
SMIME – SMIME Organization Validation
Starting August 29, 2023, at 10:00 MDT (16:00 UTC), all newly issued S/MIME certificates, including new, reissued, and renewed certificates, must comply with the new Baseline Requirements for the Issuance and Management of Publicly‐Trusted S/MIME Certificates.
CertCentral Services API: New product validation type for client certificates on Order info API response
In the CertCentral Services API, for client certificate orders, we updated the Order info API endpoint to return data describing the type of organization validation DigiCert will use for client certificates after August 29.
Background
The Order info API endpoint returns a product object with information about the type of certificate on the order. For certificates that require organization validation, the product object includes parameters describing the type of organization validation used for the product:
validation_typevalidation_descriptionvalidation_name
After today's update, for client certificates that require organization validation, these fields return values associated with SMIME Organization Validation. For example:
{
...
"product": {
"csr_required": false,
"name": "Premium",
"name_id": "client_premium",
"type": "client_certificate",
"validation_description": "SMIME Organization Validation",
"validation_name": "SMIME",
"validation_type": "smime"
},
...
}Before, these fields returned values associated with Normal Organization Validation. For example:
{
...
"product": {
"csr_required": false,
"name": "Premium",
"name_id": "client_premium",
"type": "client_certificate",
"validation_type": "ov",
"validation_name": "OV",
"validation_description": "Normal Organization Validation",
},
...
}How does this affect my API client integration?
If you use the Order info API endpoint to retrieve validation information from the product object, make sure your integration can handle the new validation type values for client certificates.
Otherwise, this change is compatible with existing workflows for validating organizations and requesting client certificates:
Until August 29, you can continue ordering client certificates for organizations with an active Normal Organization Validation (OV).
After August 29, when ordering client certificates for an organization without active SMIME Organization Validation, DigiCert will automatically submit the organization for SMIME validation.
Stay informed about updates to client certificate API workflows
As we update our systems to comply with the new Secure Email (S/MIME) baseline requirements, we will continue updating Services API workflows for managing S/MIME certificates in CertCentral. Visit our developer portal for a comprehensive list of these changes: Services API updates for client certificate certificate workflows. Make sure to save this page and check it frequently, as we will update this article as new information becomes available.
CertCentral Webhooks: New event types, event logs, and notifications for immediately issued certificates
New CertCentral events
We updated CertCentral webhooks to send notifications for these event types:
Domain expired
Domain revalidation notice
Domain validated
Organization expired
Organization revalidation notice
Organization validated
Order rejected
Subscribe to these events when creating or updating a webhook in CertCentral. Learn more: CertCentral event types
Webhook event logs
We're excited to announce that webhook event logs are now available.
Every time CertCentral sends an event to your webhook listener, we create a new webhook event log entry. Each entry includes the event timestamp, event data, and response code that your webhook listener returned to CertCentral. Event logs make it easier to review your event history and troubleshoot the connection between CertCentral and your webhook listener.
Learn more: Webhook event logs
Get notified for immediately issued certificates
Now, you can choose to receive certificate issued events even when certificates are issued immediately. Before, you could only receive certificate issued events for certificates that weren't issued immediately.
Learn more: Customize certificate issued events
CertCentral Services API: Choose a recipient when emailing site seal code
In the CertCentral Services API, we updated the Email site seal API endpoint. Now, when emailing site seal code, you can choose who receives the email by including the optional parameter recipient_email in your request. If omitted, DigiCert emails the site seal to the authenticated user (the user that owns the API key in the request).
Example cURL request:
curl 'https://www.digicert.com/services/v2/order/certificate/{{order_id}}/site-seal/email-seal' \
--header 'X-DC-DEVKEY: {{api_key}}' \
--header 'Content-Type: application/json' \
--data-raw '{
"recipient_email": "john.doe@example.com"
}'For more information, visit the API reference documentation: Email site seal.
July 17, 2023
CertCentral Services API: Create and validate organizations with a single API request
We updated the CertCentral Services API documentation to describe how to create an organization and submit it for validation with a single API request. Learn more: Create organization.
Improve your organization validation workflows
Before this update, the API workflow to create an organization and submit it for validation required two API calls:
One to create the organization.
A second to submit the organization for validation.
The Services API still supports this workflow. However, if you know the intended use for an organization at the time of its creation, we recommend performing both of these operations in the same request. Consider updating your integration if you need to improve latency for your end-users, avoid rate limiting, or reduce the number of requests you submit to the Services API for another reason.
July 11, 2023
CertCentral Services API: Remove unexpected data from Order info response
On July 11, 2023, at 10:00 MDT (16:00 UTC), DigiCert will fix an issue causing the Order info API endpoint to return unexpected verified_contacts data. We will restore the Order info response to its original behavior and stop returning verified_contacts inside the organization object.
To get verified contacts for an organization, use the Organization endpoints:
Example Order info response before and after July 11
Before the fix
Truncated JSON response with organization.verified_contacts[] array:
{
...
"organization": {
"id": 12345,
"name": "Example Organization, LLC",
"display_name": "Example Organization, LLC",
"is_active": true,
"city": "Saratoga Springs",
"state": "Utah",
"country": "us",
"telephone": "555-555-5555",
"verified_contacts": [
{
"id": 1234,
"user_id": "5678",
"name": "John Doe",
"first_name": "John",
"last_name": "Doe",
"job_title": "Developer",
"telephone": "555-555-5555",
"email": "john.doe@example.com"
}
]
},
...
} After the fix
Truncated JSON response without organization.verified_contacts[] array:
{
...
"organization": {
"id": 12345,
"name": "Example Organization, LLC",
"display_name": "Example Organization, LLC",
"is_active": true,
"city": "Saratoga Springs",
"state": "Utah",
"country": "us",
"telephone": "555-555-5555",
},
...
} July 8, 2023
Upcoming scheduled global maintenance
DigiCert will perform scheduled maintenance on July 8, 2023, 22:00 – 24:00 MDT (July 9, 2023, 04:00 – 06:00 UTC). Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
Upcoming scheduled Europe maintenance
DigiCert will perform scheduled maintenance on July 8, 2023, 09:00 – 11:00 MDT (15:00 – 17:00 UTC). Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
June 13, 2023
CertCentral Services API: Update order-level organization and technical contact
In the CertCentral Services API, we added a new endpoint that you can use to update the order-level organization and technical contact for existing certificate orders.
Use the new endpoint to perform these operations:
Add an order-level technical contact.
Replace or modify the existing order-level technical contact.
Replace or modify the existing order-level organization contact.
For usage information, parameter descriptions, and example requests, visit the API reference: Update organization and technical contact for an order.
June 6, 2023
CertCentral admin can set client certificate CSR policy for all organization users
CertCentral admins can now establish an organization-wide setting for users to follow when requesting client certificates. The options are:
Require user to paste or upload CSR
User must have a CSR at time of enrollment.
Require email recipient to generate CSR in browser
The user can postpone CSR generation by naming an email recipient, who will be prompted to create the CSR and certificate.
No preference
User can choose to enter a CSR or leave the CSR field empty (requiring the email recipient to generate the CSR).
June 3, 2023
Scheduled global maintenance
Some DigiCert services will experience service delays and performance degradation during scheduled maintenance on June 3, 2023, 22:00 – 24:00 MDT (June 4, 2023, 04:00 – 06:00 UTC).
Infrastructure maintenance-related service delay and performance degradation
The infrastructure maintenance starts at 22:00 MDT (04:00 UTC). Then for approximately 10 minutes, the services listed below will experience service delays and performance degradation that affect:
CertCentral® and Services API
Certificate Issuing Service (CIS)
CertCentral Simple Certificate Enrollment Protocol (SCEP)
Direct Cert Portal and API
API notes
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance starts and when maintenance ends.
See the DigiCert global 2023 maintenance schedule for scheduled maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Europe maintenance
Some DigiCert services will be down for up to 60 minutes during scheduled maintenance on June 3, 2023, 09:00 – 11:00 MDT (15:00 – 17:00 UTC).
DigiCert ONE infrastructure maintenance-related downtime
The DigiCert ONE infrastructure maintenance starts at 09:00 MDT (15:00 UTC). At that time, DigiCert ONE Netherlands and Switzerland instances, along with access to their managers, services, and APIs, will be down for up to 60 minutes.
DigiCert ONE Netherlands instance
Trust Lifecycle Manager
IoT Trust Manager
Software Trust Manager
Document Trust Manager
DigiCert Private CA
Account Manager
DigiCert ONE Switzerland instance
Trust Lifecycle Manager
IoT Trust Manager
Software Trust Manager
Document Trust Manager
DigiCert Private CA
Account Manager
API note
APIs will return "503 services unavailable" errors.
Requests placed during this window that receive a "503 services unavailable" error message will need to be placed again after services are restored.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance starts and when maintenance ends.
See the DigiCert Europe 2023 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
June 1, 2023
Code signing certificates: New private key storage requirement
Starting on June 1, 2023, at 00:00 UTC, industry standards will require private keys for code signing certificates to be stored on hardware certified as FIPS 140 Level 2, Common Criteria EAL 4+, or equivalent.
DigiCert’s timeline to meet the new private key storage requirement
DigiCert’s timeline ensures we update our code signing certificate process so that private keys for code signing certificates are stored on hardware certified as FIPS 140 Level 2, Common Criteria EAL 4+, or equivalent by May 30, 2023.
Our timeline also allows you to transition to the supported provisioning methods by May 16, 2023.
Learn more about the DigiCert code signing certificate change timeline
CertCentral Services API: Webhooks
CertCentral supports webhook notifications when a certificate is issued or revoked.
You can now receive notifications for certificate events without regularly querying the Orders API for certificate status. Your external application (listener) can wait to receive notification that the certificates are ready, then send a callback request to download the certificate or programmatically alert the certificate owner.
Learn more: CertCentral webhooks
May 30, 2023
Code Signing certificate changes
CertCentral: Authenticate webhook events with secret keys
We are happy to announce that you can now add custom secret keys to CertCentral webhooks. With secret keys, you can ensure the authenticity of webhook events, enhancing the security of your webhook listener.
How webhook secret keys work
When creating or updating a webhook, you can choose to add a custom secret key. If a webhook has a secret key, webhook events include the secret key value in the custom request header X-WEBHOOK-KEY.
To prevent your webhook listener from processing invalid events, configure the endpoint for your webhook listener to validate the X-WEBHOOK-KEY value for each event it receives.
Learn more:
May 20, 2023
CertCentral Services API: Update for Encryption Everywhere DV order requests
In the CertCentral Services API, we updated the request body for creating an Encryption Everywhere DV order to stop using the use_auth_key parameter. Now, DigiCert always ignores the use_auth_key parameter in your requests to create an Encryption Everywhere DV order.
How does AuthKey domain validation work for Encryption Everywhere DV orders?
When you submit an Encryption Everywhere DV order request, DigiCert checks to see if an AuthKey exists in your CertCentral account.
AuthKey exists for the account
DigiCert automatically checks the DNS records for AuthKey request tokens. If we find a valid AuthKey request token for each domain on the order, we validate the domains and the API returns your issued certificate. Otherwise, the API returns an error.
No AuthKey exists for the account
The API returns an error. You must create an AuthKey before you can request Encryption Everywhere DV certificates.
Learn more about using AuthKey request tokens: DV certificate immediate issuance.
Background
For Encryption Everywhere DV certificates, DigiCert has always required completing domain control validation using AuthKey request tokens. A change we released on May 16, 2023 made it possible to pass in a false value for the use_auth_key parameter when creating an Encryption Everywhere DV order.
Now, for Encryption Everywhere DV orders, we use the certificate type to trigger the AuthKey request token check instead of looking for the use_auth_key parameter. This change makes the API easier to use and prevents Encryption Everywhere DV orders from being created in a state where the domains cannot be validated and the order must be rejected.
May 16, 2023
CertCentral Services API: New use_auth_key default for DV certificate requests
Nota
Update: We are postponing these changes until May 16, 2023. We originally planned to release this update on May 10, 2023.
On May 16, 2023, at 10:00 AM MDT (16:00 UTC), DigiCert will change the default behavior for DV TLS/SSL orders in CertCentral accounts using AuthKeys.
Starting May 16, DV TLS certificate orders and reissues created with the CertCentral Services API will always use a default value of false for the use_auth_key request parameter.
After this change, to validate domains on a DV order or reissue using AuthKey request tokens, you must include the use_auth_key parameter with a true value in the body of your certificate request:
{
...
"use_auth_key": true
...
}Nota
Today, if an AuthKey exists in your account, DigiCert uses AuthKey request tokens to validate domains on DV TLS/SSL orders and reissues by default. To opt out of this default, you must include the use_auth_key parameter with a value of false in your DV certificate order requests.
How does this affect me?
Starting May 16, for DV TLS orders and reissues that omit the use_auth_key request parameter, DigiCert will stop using AuthKey request tokens to complete domain validation.
For all DV products except Encryption Everywhere DV, DigiCert will still accept the request. However, we will not check domains on the order for an AuthKey request token. This means we cannot immediately complete domain validation and return the certificate data in the API response. Instead, the API will return a random value (
dcv_random_value) that you can use to complete domain validation after the order is created:{ "id": 123456, "certificate_id": 123456, "dcv_random_value": "icru1984rnekfj" }For Encryption Everywhere DV certificates (
ssl_dv_ee), DigiCert will reject the order. Domains on Encryption Everywhere DV certificates can only be validated using AuthKey request tokens.
What do I need to do?
First, see if this change affects your API client integration.
This change affects you if you meet all of the following criteria:
Your CertCentral account has an AuthKey.
To check if an AuthKey exists in your account, use the AuthKey details endpoint.
You use the API to request or reissue any of these DV SSL/TLS certificates:
Product identifier
Name
ssl_dv_geotrustGeoTrust Standard DV SSL Certificate
ssl_dv_rapidsslRapidSSL Standard DV SSL Certificate
ssl_dv_thawteThawte SSL123 DV
ssl_dv_eeEncryption Everywhere DV
wildcard_dv_geotrustGeoTrust Wildcard DV SSL Certificate
wildcard_dv_rapidsslRapidSSL Wildcard DV SSL Certificate
cloud_dv_geotrustGeoTrust Cloud DV
ssl_dv_geotrust_flexGeoTrust DV SSL
Next, update your code.
Review any requests to the Services API that create a DV certificate order or reissue for domains you want to validate with an AuthKey request token. See if these requests already include the
use_auth_keyparameter with a true value.If yes:
No action is required. After May 16, 2023, DigiCert will continue using AuthKey request tokens to validate the domains on your orders and reissues.
If not:
Before May 16, 2023, update your requests to include the
use_auth_keyparameter with a true value:{ ... "use_auth_key": true ... }
Why is DigiCert making this change?
To improve security. By default, the API should assume clients want to complete DCV using DigiCert-generated random values. DigiCert should only check for user-generated AuthKey request tokens when clients explicitly request this behavior.
To make the API more deterministic and easier to use. After this change, API requests that omit the
use_auth_keyparameter will always generate the same results, regardless of whether an AuthKey exists in the account.To align our system with future API enhancements. This change makes it possible to deliver enhancements that behave the same way for different product types.
Code Signing certificate changes
May 9, 2023
CertCentral Services API: Added support for order-level organization contacts
To give API clients more control over the contacts assigned to new and renewal orders, we updated the CertCentral Services API to support order-level organization contacts.
Now, when requesting or renewing a certificate, you can assign an organization and technical contact directly to the order instead of using the contacts assigned to the organization on the request. If you do, DigiCert creates the order using the order-level contacts. The organization and technical contact for the organization remain unchanged.
Nota
Before, DigiCert always created orders using the organization contact assigned to the organization on the order. Creating an order with a different organization contact required replacing the organization contact for the organization.
To submit an order-level organization and technical contact with your order, include the organization_contact and technical_contact objects at the root of your JSON request body. If omitted, DigiCert uses the organization and technical contact assigned to the organization on the order.
Example JSON request
{
"certificate": {
"common_name": "example.net",
"csr": "<csr>"
},
"organization_contact": {
"first_name": "Jane",
"last_name": "Doe",
"job_title": "Manager",
"telephone": "555-555-5555",
"email": "jane.doe@example.com"
},
"technical_contact": {
"first_name": "John",
"last_name": "Doe",
"job_title": "Site Reliability Engineer",
"telephone": "555-555-5556",
"email": "john.doe@example.com"
},
"organization": {
"id": <organization_id>
},
"order_validity": {
"years": 6
},
"payment_method": "balance"
}Supported products
The API supports the option to add an order-level organization contact for all certificates that require an organization contact.
May 6, 2023
Scheduled global maintenance
DigiCert will perform scheduled maintenance on May 6, 2023, 22:00 – 24:00 MDT (May 7, 2023, 04:00 – 06:00 UTC).
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Europe maintenance
Some DigiCert services will be down for up to 60 minutes during scheduled maintenance on May 6, 2023, 09:00 – 11:00 MDT (15:00 – 17:00 UTC).
DigiCert ONE infrastructure-related maintenance downtime
The DigiCert ONE infrastructure-related maintenance starts at 15:00 UTC. At that time, DigiCert ONE Netherland and Switzerland instances, along with access to their managers, services, and APIs, will be down for up to 60 minutes.
DigiCert ONE Netherlands instance
Trust Lifecycle Manager
IoT Trust Manager
Software Trust Manager
Document Trust Manager
DigiCert Private CA
Account Manager
DigiCert ONE Switzerland instance
Trust Lifecycle Manager
IoT Trust Manager
Software Trust Manager
Document Trust Manager
DigiCert Private CA
Account Manager
API notes
APIs will return "503 services unavailable" errors.
Requests placed during this window that receive a "503 services unavailable" error message will need to be placed again after services are restored.
Services will be restored as soon as the maintenance is completed.
May 2, 2023
Code Signing certificate changes
April 25, 2023
Secure email certificates for individuals and businesses
We are happy to announce that DigiCert is now offering enhanced Secure Email Certificates (S/MIME) at two levels, Secure Email for Individual and Secure Email for Business.
These certificates offer:
Secure email encryption and signing
Validation that your emails come from you
Secure Email for Individual is automatically validated and quick to generate – you can begin using your certificate within minutes.
Secure Email for Business includes an extra level of validation, authenticating your organization as an email sender, and includes support options.
To add these certificates to your CertCentral account, select Secure email certificates on the request page.
Don’t see Secure Email for Individual and Secure Email for Business in your account? Contact your account manager or DigiCert Support.
Nota
Not available in Japan.
April 19, 2023
CertCentral Orders page: Improved order status search
We updated the Issued filter in the Order Status search feature on the CertCentral Orders page to only return your issued certificates. Previously, the issued filter returned issued, renewed, expired, and reissue pending orders in the search results, making it difficult to find only your issued certificates.
See for yourself
In the left main menu, go to Certificates > Orders.
On the Orders page, in the Order Status dropdown, select Issued and then select Go.
How the Order Status filter work
When using the Order Status search feature, you can only use one filter at a time. See the table below for information on the results that each filter returns in its search.
For multiple status searches, leave the Order Status search as Unfiltered and download a CSV file. You can also use the Reports library to build a custom report (in the left main menu, go to Reports).
Filter | Search results |
|---|---|
Active | Issued, pending, and pending reissue certificates |
Issued | Issued certificates |
Pending | Pending certificates |
Reissue pending | Reissue pending certificates |
Revoked | Revoked orders |
Rejected | Rejected pending certificates |
Expired | Expired certificates and orders |
Renew | Renewed certificates |
April 11, 2023
CertCentral Services API: Enhanced response when editing domains on an OV or EV certificate order
We improved how the API returns data when using the endpoint to edit domains on pending OV or EV orders and reissues. After this change, when editing domains on a pending OV or EV order:
A successful request returns a response status code of
200 OK.The API returns a list of
domainswith an object for each domain on the order. Each object has thenameandidof the domain in your account that you must validate to prove control over the domain on the order.
Before this change, successful requests to edit domains on pending OV or EV orders and reissues returned a response status code of 204 No Content. The response did not include any data, even if the request created new domains in your account.
Nota
There is no change to the API behavior when updating domains on DV orders. Successful requests to edit domains on DV orders continue to return a response status code of 204 No Content.
Example response for a successful call to edit domains on a pending OV or EV order:
In this example, every domain (dns_name) on the order is submitted for validation under the scope of the base domain example.org. This means each object in the domains array returns the name and id for example.org.
Learn more: Edit domains on a pending order or reissue
April 8, 2023
Scheduled global maintenance
Some DigiCert services will be down or experience delayed responses for up to 10 minutes during scheduled maintenance on April 8, 2023, 22:00 – 24:00 MDT (April 9, 04:00 – 06:00 UTC).
Infrastructure-related maintenance downtime
The infrastructure-related maintenance starts at 22:05 MDT (04:05 UTC). At that time, the services listed below will be down for up to 10 minutes.
Affected services
Certificate Issuing Service (CIS) and CertCentral Simple Certificate Enrollment Protocol (SCEP)
Certificate requests submitted during this time will fail.
Resubmit failed requests after services are restored.
CertCentral certificate issuance
Certificate requests submitted during this time will fail.
Resubmit failed requests after services are restored.
CertCentral Automation
Reschedule automation events around maintenance.
Retry failed events after services are restored if events cannot be rescheduled.
QuoVadis® TrustLink® certificate issuance
TrustLink certificate requests submitted during this time will fail.
Resubmit failed requests after services are restored.
Direct Cert Portal certificate issuance
Certificate requests submitted during this time will fail.
Resubmit failed requests after services are restored.
PKI Platform 8 new domain and organization validation
New domains and organizations submitted for validation during this time will be delayed.
Requests will be queued and processed after services are restored.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance starts and when maintenance ends.
See the DigiCert global 2023 maintenance schedule for scheduled maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Europe maintenance
Some DigiCert services will be down for up to 10 minutes during scheduled maintenance on April 8, 2023, 09:00 – 11:00 MDT (15:00 – 17:00 UTC).
CertCentral Infrastructure-related maintenance downtime
The infrastructure-related maintenance starts at 10:05 MDT (16:05 UTC). At that time, CertCentral certificate issuance may be down or experience delayed response for up to 10 minutes.
Items to note:
Certificate requests submitted during this time will fail.
Resubmit failed requests after services are restored.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance starts and when maintenance ends.
See the DigiCert Europe 2023 maintenance schedule for scheduled maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
March 28, 2023
CertCentral: Value added tax (VAT) numbers
We are happy to announce that CertCentral now allows you to add a valued added tax (VAT)* number to all your transactions, such as purchasing a certificate and depositing funds. DigiCert will append the VAT number supplied as a reference on payment records. Remember that if you do not provide your VAT number, your orders may include unexpected taxes that would have been excluded had you provided the VAT ID number.
Importante
VAT numbers are not supported by DigiCert USA and DigiCert Japan billing entities. Contact your account manager to learn more about your account’s billing entity.
You can add a VAT number to your account or division. When requesting a certificate, depositing funds, and creating a purchase order, you can use the account or division VAT number or add a custom VAT number that applies to that transaction only. The VAT number appears on your invoice/receipts and purchase orders (POs).
Importante
DigiCert’s inclusion of VAT numbers in payment documentation is for customers’ use and convenience only. DigiCert does not validate the VAT numbers and is not responsible for inaccurate information provided by customers. See DigiCert’s Master Service Agreement.
CertCentral: Taxes included split out on monthly auto-invoices for negative account balances
For CertCentral customers with negative account balances, we have updated your monthly invoice to display the total amount due and how much is from sales tax. Additionally, the monthly auto-invoices will now display the customer's value added tax (VAT) ID number if they have provided it in their CertCentral account.
For customers where sales tax is required by local law, the monthly auto-invoices have always included the taxes charged as part of each purchase in the total invoice amount. However, until now, monthly auto-invoices did not split out how much of the total invoice was taxed.
CertCentral Services API: Enhanced Order validation status response
In the CertCentral Services API, we updated the Order validation status API to return a new response parameter for domains pending validation: dns_name_validations[].name_scope.
The name_scope parameter returns the domain you must validate to prove control over the domain on the certificate order. This is useful when you need to validate a domain on the certificate by completing a DCV check for either the base domain or for a subdomain between the FQDN and base domain.
For example:
{
...
"dns_name_validations": [
{
"name_scope": "sub.example.com",
"status": "unapproved",
"method": "email",
"dns_names": [
"sub.example.com"
],
"base_domain": "example.com"
}
]
...
}Notes:
For all orders, the API omits the
dns_name_validations[].name_scopeparameter for validated (approved) domains.For DV orders, the API returns a
dns_name_validations[].name_scopeparameter for all pending (unapproved) domains.For OV and EV orders, the API omits the
dns_name_validations[].name_scopeparameter unless the order specifies a domain-level validation scope for the domain. To validate domains with noname_scope, use the domain validation scope chosen for the order (order_name_scope).
CertCentral Services API: Bugfix for API endpoint to get DV order validation status
Nota
Update: We are postponing these changes until March 28, 2023. We originally planned to release this update on March 22, 2023.
On March 28, 2023, at 10:00 MDT (16:00 UTC), DigiCert will fix a bug with the Order validation status API endpoint. This bug causes the API to return different values for DV TLS orders versus OV and EV TLS orders in the dns_name_validations[].dns_names array.
Starting March 28, the dns_name_validations[].dns_names array in the Order validation status API response will always contain the exact FQDN associated with the given validation details.
This fix standardizes what is returned for DV, OV, and EV TLS orders in the dns_name_validations[].dns_names array. It also aligns the API behavior with the description of the dns_names array in the API documentation.
Currently:
For DV orders, the
dns_name_validations[].dns_namesarray contains the domain that was submitted for validation. Depending on the DCV scope set for the order, the domain submitted for validation may be a higher-level domain than the FQDN on the order.For OV and EV TLS orders, the
dns_name_validations[].dns_namesarray already contains the exact FQDN on the order.
What do I need to do?
Check your code to determine if this change affects your API integration.
This change affects you if you meet all of the following criteria:
You use the Order validation status API endpoint to get the validation status of DV orders.
Your integration expects the API to return a
dns_name_validations[].dns_namesarray with the domain name submitted for validation instead of the exact FQDN on the order.
Determine if action is required.
Do you meet all of the criteria listed above?
If not, no action is required. You can safely ignore this change.
If yes, update your code before March 28, 2023.
Wherever you handle response data from the Order validation status endpoint, make sure your integration always expects the
dns_name_validations[].dns_namesarray to contain the exact FQDN from the order.
Aviso
Failing to update your code may result in unexpected behavior after we make this change.
Examples
This example shows how the dns_name_validations[].dns_names array will change. Each JSON object shows what the Order validation details API returns when querying a DV order for the FQDNs sub.example.net and sub.example.org. The order in this example uses a DCV scope of base domain.
Before March 28, 2023 bugfix | After March 28, 2023 bugfix |
|---|---|
{
...
"dns_name_validations": [
{
"status": "unapproved",
"method": "email",
"dns_names": [
"example.net"
],
"base_domain": "example.net"
},
{
"status": "unapproved",
"method": "email",
"dns_names": [
"example.org"
],
"base_domain": "example.org"
}
]
...
} | {
...
"dns_name_validations": [
{
"status": "unapproved",
"method": "email",
"dns_names": [
"sub.example.net"
],
"base_domain": "example.net"
},
{
"status": "unapproved",
"method": "email",
"dns_names": [
"sub.example.org"
],
"base_domain": "example.org"
}
]
...
} |
March 15, 2023
DCV method information updates to Domain details pages
We updated the individual domain validation process (often referred to as domain prevalidation) to improve how we display the domain’s domain control validation (DCV) method.
Note that before, we always showed the last submitted DVC method. This wasn’t very clear for customers whose last submitted DCV method was different from the last method used to validate the domain.
Now, when a domain is pending validation or revalidation, we show the last submitted DCV method (in other words, the method currently being used to validate the domain). After you validate the domain, we show the DCV method last used to complete the validation.
CertCentral Services API: New Domain info response parameter
We added the dcv_approval_method parameter to the Domain info API response. This parameter returns the DCV method used to complete the most recent DCV check for the domain.
Aviso
This differs slightly from the value of the dcv_method response parameter, which returns the latest DCV method configured for the domain. When using a different DCV method to revalidate a domain, the latest DCV method configured for the domain (dcv_method) may differ from the DCV method used to complete the most recent DCV check (dcv_approval_method).
We only return the dcv_approval_method parameter when the request URL contains ?include_dcv=true.
March 8, 2023
DigiCert moving to G2 root and intermediate CA (ICA) certificate hierarchies
Update:
To provide more time to increase our fifth-generation (G5) root ubiquity, DigiCert has delayed our move to our new single-purpose root and ICA certificate hierarchies. Instead, we will move to second-generation root and ICA certificate hierarchies in the interim to comply with Mozilla’s root distrust timeline for DigiCert first-generation root certificates.
On March 8, 2023, at 10:00 MST (17:00 UTC), DigiCert will begin updating the default public issuance of TLS/SSL certificates to our second-generation (G2) root and intermediate CA (ICA) certificate hierarchies. See our DigiCert root and intermediate CA certificate updates 2023 knowledge base article for more information.
How do switching root and ICA certificates affect me?
Switching to a different certificate hierarchy typically doesn't require additional work as long as you always install the DigiCert-provided ICA certificate when installing your TLS certificate.
With the change to G2 certificate hierarchies, no action is required unless you do any of the following:
Pin ICA/Root certificates
Hard-code the acceptance of ICA/Root certificates
Operate a trust store
If you do any of the above, we recommend updating your environment before March 8, 2023. Stop pinning or hard-coding root or ICA certificate acceptance or make the necessary changes to ensure certificates issued from the G2 certificate hierarchy are trusted (in other words, they can chain up to their trusted G2 root certificate).
How do switching root and ICA certificates affect my existing certificates?
Switching to the G2 hierarchy does not affect your existing certificates. DigiCert has timed the move to G2 root certificate hierarchies to ensure your existing certificates will not be affected by the Mozilla distrust policy. Active TLS/SSL certificates issued from a G1 hierarchy will remain trusted until they expire.
However, newly issued, renewed, reissued, and duplicate certificates issued after March 8, 2023, will chain to the G2 root hierarchy. When installing your certificates, make sure to include the DigiCert-provided ICA certificate.
What if I need more time to update my environment?
If you need more time to prepare, contact DigiCert Support. We will set up your account so you can continue to use the root and ICA certificates you are using now.
When deciding how long to stay on your current root, remember that Mozilla root distrust includes the ICA certificate and TLS/SSL certificates linked to the root. To remain trusted, all active certificates, including reissues and duplicates, must be reissued from a G2 or newer root hierarchy before the root certificate distrust date.
March 4, 2023
Upcoming scheduled maintenance
Some DigiCert services will be down for approximately 5 minutes during scheduled Europe maintenance on March 4, 2023, 09:00 - 11:00 MST (16:00 - 18:00).
QuoVadis platform maintenance-related downtime
During the two-hour maintenance window, QuoVadisQ platform services will be down for approximately 5 minutes while we do some infrastructure-related maintenance that requires server restarts.
What can I do?
Schedule high-priority tasks before or after the maintenance windows.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance starts and when maintenance ends.
See the DigiCert Europe 2023 maintenance schedule for scheduled maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
February 28, 2023
Verified Mark Certificates (VMC): Image and certificate file hosting and government marks
We are happy to announce that DigiCert has added two new features to our Verified Mark Certificates:
Government mark support
Instead of using a trademarked logo in your Verified Mark Certificate, you can now use a government mark.
Image and certificate file hosting
Instead of hosting the logo image and Verified Mark Certificate file yourself, you can now allow DigiCert to host the files on your behalf.
What are government marks?
A government mark is a logo that a government grants to an organization.
To get a VMC for a government mark, you provide your government mark’s enabling legislation instead of trademark registration. The law or government record that grants the logo to your organization proves the mark’s legitimacy to get a VMC.
What is image and certificate file hosting?
Our image and certificate file hosting feature allows DigiCert to host your VMC and SVG logo files on your behalf.
With DigiCert hosting, you set up your domain’s DNS record once, and then we keep your VMC and SVG logo files up-to-date. When you renew or reissue your certificate, we automatically push the latest version of your files to our hosted server with no changes required in your DNS or other configuration.
CertCentral Services API: Enhancements for VMC file hosting and government marks
To support VMC file hosting and government marks in API integrations, we made several additive enhancements to the endpoints for managing VMC orders.
Improvements to verified contacts selections when requesting SSL/TLS and code signing certificates
We are happy to announce that we have improved the verified contact selection process when ordering EV SSL/TLS, Code Signing, and EV Code Signing certificates.
Now when you select an organization with existing verified contacts, you can see if a contact is validated (green check mark) or pending validation (yellow timer). Before, you could not see the validation status for the organization’s verified contacts.
February 17, 2023
Verified Mark Certificates (VMC): Six new approved trademark offices
We are happy to announce that DigiCert now recognizes three more intellectual property offices for verifying the logo for your VMC certificate. These offices are in Denmark, France, Netherlands, New Zealand, Sweden, and Switzerland.
New approved trademark offices:
Denmark - Danish Patent and Trademark Office
France - French Patent and Trademark Office
Netherlands - Benelux Organization for Intellectual Property
New Zealand - Intellectual Property Office of New Zealand
Sweden - Swedish Intellectual Property Office
Switzerland - Swiss Federal Institute of Intellectual Property
Other approved trademark offices:
Australia - IP Australia
Brazil - National Institute of Industrial Property
Canada - Canadian Intellectual Property Office
European Union - European Union Intellectual Property Office
Germany - German Patent and Trade Mark Office
India - Office of the Controller General of Patents, Designs and Trade Marks
Japan - Japan Patent Office
Republic of Korea (South Korea) - Korean Intellectual Property Office
Spain - Spanish Patent and Trademark Office
United Kingdom - Intellectual Property Office
United States - United States Patent and Trademark Office
What is a Verified Mark Certificate?
Verified Mark Certificates (VMCs) are a new type of certificate that allows companies to place a certified brand logo next to the “sender” field in customer inboxes.
Your logo is visible before the message is opened.
Your logo acts as confirmation of your domain’s DMARC status and your organization’s authenticated identity.
February 15, 2023
New Dedicated IP addresses for DigiCert Services
Update: IP Address change postponed until February 15, 2023
When we sent notifications in June 2022 about the IP address change, one of the IP addresses was incorrect. The same IP address was incorrect in this change log. We fixed that, and the information in the change log has been corrected.
To provide you with time to verify and update the IP addresses in your allowlist, we have postponed the IP address change until February 2023.
What if I already updated my allowlists?
Verify that the IP addresses in your allowlist match those in the New dedicated IP Addresses list below.
On February 15, 2023, at 08:00 MST (15:00 UTC), DigiCert will assign new dedicated IP addresses to several DigiCert services.
For more details about these IP addresses, see our New Dedicated IP Addresses knowledge base article.
If you have questions or need help, contact your account manager or DigiCert Support.
February 14, 2023
Change log RSS feed returns
We are happy to announce that we’ve reimplemented the RSS Feed for the CertCentral® Change log. You can find the new change log feed here: https://docs.digicert.com/en/certcentral/change-log.rss.
RSS feed items to note
The RSS feed returns the 15 most recent change log entries.
To make upcoming changes easier to identify, we labeled them Upcoming changes.
The Change log RSS feed follows RSS 2.0 specifications and is compatible with RSS 2.0 compliant feed aggregators.
RSS feed reader tips
All major browsers have RSS feed extensions to automatically access your selected RSS feeds and organize the results for you.
The new RSS feed is also auto-discoverable from the Change log web page.
February 09, 2023
CertCentral: Improved OV and EV TLS certificate domain control validation
We are happy to announce that we updated the Prove control over your domain popup window for pending OV and EV TLS certificate orders, making it easier to see what you need to do to complete the domain validation for all domains included on your certificate.
Now, when you select a domain control validation (DCV) method, you can see basic instructions for completing the domain validation along with a link to more detailed instructions on our product documentation website.
CertCentral Services API: Expiration date now available for order-level DCV random values
We updated the CertCentral Services API to return the expiration date for order-level DCV random values.
Now, when you submit a request to the Get order DCV random value or Change order DCV method API endpoints, the response includes the expiration date (expiration_date) of the random value:
{
"dcv-random_value": "fjqr7th5ds",
"expiration_date": "2023-02-24T16:25:52+00:00"
}February 4, 2023
Upcoming scheduled maintenance
Some DigiCert services will be down for up to 10 minutes during scheduled Europe maintenance on February 4, 2023, 09:00 - 11:00 MST (16:00 - 18:00)
QuoVadis platform maintenance-related downtime
During the two-hour maintenance window, QuoVadis platform services will be down for up to 10 minutes in total while we do some infrastructure-related maintenance that requires service restarts: 5 minutes for a monthly patching restart and 5 minutes for a database restart.
What can I do?
Plan accordingly:
Schedule high-priority tasks before or after the maintenance windows.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance starts and when maintenance ends.
See the DigiCert Europe 2023 maintenance schedule for scheduled maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
January 25, 2023
CertCentral now supports SSO federation through OpenID Connect
To improve security and better integrate with current Single Sign-On technology, DigiCert now supports SSO federation through Open ID Connect (OIDC).
I already connect CertCentral to my identity provider using SAML. Do I need to switch to OIDC?
No, you can continue using your existing setup. However, you may wish to migrate to OIDC because it is easier to implement, works more smoothly on mobile devices, and is more accessible to APIs.
How do I connect my identity provider with CertCentral using OIDC?
January 23, 2023
CertCentral: Guest URL support for Verified Mark Certificates
We are happy to announce that we added Verified Mark Certificates (VMCs) to the available products for Guest URLs for CertCentral Enterprise and CertCentral Partner.
Previously, you had to add someone to your account before they could order a Verified Mark Certificate (VMC). Now, you can create a Guest URL that allows a person to order a VMC without needing to be a user in your account.
Bugfix: Pending verified contacts missing from Organization details pages
We fixed a bug that prevented pending verified contacts from being displayed on the Organization details page. Note that after we validated a contact, they were automatically added to the page (i.e., you could see the “validated” verified contacts but not those pending validation).
Now when you submit a verified contact for validation, they appear in the Verified Contacts section along with the pending validation types: EV, EV CS, or CS.
January 17, 2023
CertCentral: Set the domain validation scope when reissuing TLS certificates
We are happy to announce that you can now set the domain validation scope when reissuing your TLS/SSL certificates.
On the TLS/SSL certificate reissue forms, we added a DCV scope dropdown that allows you to set the domain validation scope to use when validating the domains on your reissued certificate: validate base domains or validate exact domain names. This setting makes it easier to see the default domain validation scope you will use to validate the domains when reissuing your certificate and update the scope if needed.
Nota
The domain scope setting does not change the account domain validation scope setting. It only sets the domain validation scope for your reissued certificate.
January 16, 2023
CertCentral: Legacy order # renamed to Alternate order #
On January 16, we will rename Legacy order # in CertCentral. We will change the name to Alternate order # to better align with the API and the purpose of this second order number.
Nota
Alternate order numbers do not replace the unique order number that DigiCert assigns to each order request.
CertCentral Services API
When ordering a certificate via the CertCentral Services API, you can assign a custom alphanumeric ID to an order by passing in the alternative_order_id parameter with your certificate request. Currently, CertCentral displays the alternative_order_id as the Legacy order #.
Legacy order number background
After DigiCert purchased Symantec’s TLS/SSL division, DigiCert implemented the Legacy order number as a way for customers to track their Symantec orders after importing them into CertCentral. This same feature is used by customers who want to use their own order numbers to track their CertCentral orders.
Additional information
See the Orders section of the CertCentral Services API to learn more about alternate order numbers. For example, on the Order Basic OV endpoint page, in the Request parameters table, you will find an alternative_order_id parameter entry. This entry provides more details about using alternate order numbers. The same information is provided in each of the Order endpoints.
January 13, 2023
Improvements to CertCentral change log structure
To make it easier to find information about updates to CertCentral and the CertCentral APIs, we improved the structure of the CertCentral change log. Now, DigiCert publishes all CertCentral change log entries to a single page with these sections:
Upcoming changes
Information about upcoming changes that could impact your CertCentral experience. Entries are sorted by date with the furthest pending change on top.
Recent changes
Information about recent changes made to CertCentral and the CertCentral APIs. Entries are sorted by date with the most recent change on top.
With the new structure, you can use Control + F (Windows) or Command + F (Mac) to search the entire catalogue of entries on this page for the information you need.
January 10, 2023
Bugfix: Users don’t see expiring certificate alerts in CertCentral
We fixed a bug that prevented standard and limited users from viewing the Expiring DigiCert Certificates widget on the Dashboard and the expiring certificate and order alerts on the Orders page. It also prevented them from viewing the Expiring Certificates page.
Nota
This bug did not prevent these users from viewing their expiring certificates on the Orders page; it only prevented them from viewing the expiring certificate and order alerts.
Now, when standard and limited users sign in to their CertCentral account, they see:
Expiring DigiCert Certificates widget on the Dashboard (in the left main menu, select Dashboard)
Expiring certificate and order alerts on the Orders page (in the left main menu, go to Certificates > Orders)
Expiring Certificates page (in the left main menu, go to Certificates > Expiring Certificates)
January 7, 2023
Upcoming scheduled maintenance
Some DigiCert services will be down for up to 120 minutes during scheduled maintenance on January 7, 2023.
January 5, 2023
CertCentral: Improved Order details page for pending code signing certificate orders
DigiCert is happy to announce that we updated the Order details page for pending EV and standard code signing certificate orders.
To make it easier to see what you need to do and what DigiCert needs to do to issue your EV and standard code signing certificates, we added two new sections to the Certificate status section of the Order details page:
What do you need to do – see the tasks you need to complete
What does DigiCert need to do – see the tasks DigiCert needs to perform
January 4, 2023
CertCentral: Set the domain validation scope for your new TLS certificate orders
We are happy to announce that you can now set the domain validation scope when ordering a new TLS/SSL certificate.
On the TLS/SSL certificate request forms, we added a DCV scope dropdown that allows you to set the domain validation scope to use when validating the domains on your certificate: validate base domains or validate exact domain names. This setting makes it easier to see the default domain validation scope you will use to validate the domains on your certificate and update the scope if needed.
Nota
The domain scope setting does not change the account domain validation scope setting. It only sets the domain validation scope for your certificate order.
CertCentral Services API: Set domain validation scope for new TLS certificate orders and reissues
We are happy to announce that you can now set the domain validation scope when ordering or reissuing a TLS/SSL certificate with the Services API. Use the certificate_dcv_scope parameter to define the domain validation scope for the order, overriding the domain validation scope setting for the account.
The certificate_dcv_scope parameter accepts these values:
base_domain:Validate each domain and subdomain in the request at the base domain level (for example, when submitting sub.example.com and example.com, validate example.com).fqdn:Validate each domain and subdomain included in the order exactly as named in the request.When using
fqdn::If a domain is a subdomain of another domain included on the order, complete the DCV check for the higher-level domain.
For OV and EV certificates only, if a higher-level domain exists in the account with an active validation, we validate the domain under the scope of the existing domain.