CertCentral
Change log RSS
Upcoming changes
July 8, 2025
End of life for reusing existing WHOIS-based domain validations
On July 8, 2025, DigiCert will stop reusing existing WHOIS-based domain validations, regardless of whether previously obtained information is within the allowed 397-day reuse period and regardless of the WHOIS method.
These changes affect all web-based WHOIS domain validations, including the following certificate types: TLS, Verified Mark and Common Mark, Secure Email (S/MIME), DirectAssured, and DirectTrust. See End of life for WHOIS-based DCV methods.
How does this affect me?
Have you used WHOIS-based Email or Phone DCV methods to validate your domains? Then you will need to revalidate your domains the next time you want to get a certificate.
Wichtig
End of life for reusing existing WHOIS-based domain validations does not affect your existing certificates. Your certificates will remain valid and trusted until they expire.
What do I need to do?
Do you rely on immediate certificate issuance?
If not, then no action is required until the next time you order a certificate.
The next time you order a certificate, you must choose a non-WHOIS-reliant domain control validation (DCV) method, such as DNS Text Record. To continue validating domains via email, set up a DNS TXT Email Contact or a Constructed Email address.
If yes, then action is required to avoid potential disruption to your certificate issuance.
For those that rely on instant issuance of certificates, you must revalidate your domains using a non-WHOIS-reliant DCV method , such as DNS Text Record, or to continue validating domains via email, set up a DNS TXT Email Contact or a Constructed Email address before July 8.
Why will DigiCert stop reusing existing WHOIS-based domain validations?
The industry recently adopted Ballot SC-80v3: Sunset the Use of WHOIS to Identify Domain Contacts and Relying DCV Methods. To comply with industry changes mandated by the ballot, certificate authorities (CAs), such as DigiCert, must stop using WHOIS to identify domain contacts for email, fax, SMS, postal mail, and phone domain control validation (DCV) methods. Note that DigiCert only supports the email and phone WHOIS-based DCV methods.
References
May 8, 2025
End of life for new WHOIS-based domain validations, regardless of WHOIS lookup method
On May 8, 2025, DigiCert will no longer support WHOIS-based DCV email and phone methods. DigiCert systems will stop querying WHOIS entirely for domain validations.
These changes affect all web-based WHOIS domain validations, including the following certificate types: TLS, Verified Mark and Common Mark, Secure Email (S/MIME), DirectAssured, and DirectTrust. See End of life for WHOIS-based DCV methods.
How does this affect me?
Are you using WHOIS-based Email or Phone DCV methods?
Then, the next time you validate your domains, you must use a different DCV method, such as DNS Text Record. If you want to continue to use DCV email, set up a DNS TXT Email Contact or a Constructed Email address.
Wichtig
The end of life for WHOIS-based DCV methods does not affect your existing certificates. Your certificates will remain valid and trusted until they expire.
Why will DigiCert end support for new WHOIS-based domain validations?
The industry recently adopted Ballot SC-80v3: Sunset the Use of WHOIS to Identify Domain Contacts and Relying DCV Methods. To comply with industry changes mandated by the ballot, certificate authorities (CAs), such as DigiCert, must stop using WHOIS to identify domain contacts for email, fax, SMS, postal mail, and phone domain control validation (DCV) methods. Note that DigiCert only supports the email and phone WHOIS-based DCV methods.
References
January 11, 2025
Upcoming scheduled Europe maintenance
The ADSS signing service, PrimoSign signing service, and some QuoVadis services will be down during scheduled Europe maintenance on January 11, 2025, 17:00 - 19:00 CET (16:00 - 18:00 UTC).
How does this affect me?
ADSS signing service upgrade (Netherlands) – four-hour downtime
The ADSS signing service upgrade starts at 17:00 CET (UTC 16:00). From 17:00 to 20:00 CET (16:00 to 19:00 UTC), the ADSS signing service will be down for approximately four hours.
Note: This upgrade will last four hours, extending the downtime by two hours past the scheduled maintenance window.
ADSS signing service patching (Switzerland) – 10-minute downtime
The ADSS signing service patching starts at 17:00 CET (UTC 16:00). At this time, the ADSS signing services will be down for approximately 10 minutes.
Legacy QuoVadis PrimoSign signing service maintenance – 60-minute downtime
The Legacy QuoVadis PrimoSign signing service maintenance starts at 17:00 CET (UTC 16:00). At this time, this PrimoSign signing service will be down for approximately 60 minutes.
QuoVadis services maintenance – 10-minute downtime
The QuoVadis maintenance starts at 17:00 CET (UTC 16:00). At this time, some QuoVadis services will be down for approximately 10 minutes.
SealSign Cloud
Cert Lookup
QuoVadis Legacy certificate issuance: S/MIME and PrimoSign
idp.quovadisglobal.com
Affected services:
ADSS signing service
Document Trust Manager in the DigiCert® ONE Netherlands location
Document Trust Manager in the DigiCert® ONE Switzerland location
TrustLink Enterprise in our Switzerland location
Legacy QuoVadis PrimoSign signing
Legacy QuoVadis Services
What can I do?
Plan accordingly:
Schedule high-priority ADSS and PrimoSign document signings before or after the maintenance window.
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2025 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
The PrimoSign signing services will be down for approximately 60 minutes during scheduled Global maintenance on January 11, 2025, 22:00 – 24:00 MST (January 12, 05:00 – 07:00 UTC).
How does this affect me?
The maintenance starts at 22:00 MST (05:00 UTC). At this time, the PrimoSign signing services will be down for approximately 60 minutes.
Affected services
Document Trust Manager's PrimoSign signing service in the DigiCert® ONE USA location.
What can I do?
Plan accordingly:
Schedule high-priority PrimoSign signing service document signings before or after the maintenance window.
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Global 2025 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
January 10, 2025
DigiCert moving to new dedicated IPv4 addresses for our DigiCert services and removing support for IPv6 addresses
On January 10, 2025, at 08:00 MST (15:00 UTC), DigiCert must assign new dedicated IPv4 addresses to several services. We will also remove support for IPv6 addresses at this time.
Why is DigiCert adding moving to new dedicated IPv4 addresses and removing support for IPv6 addresses?
Our current CDN (content delivery network) is discontinuing its services, forcing us to move to a new service platform before the services end, which is why we are unable to provide you with more time to prepare. When we move to our new CDN, we will focus only on IPv4 addresses and remove support for IPv6 addresses.
For more details about the new dedicated IPv4 addresses, see our knowledge base article, DigiCert Certificate Status IP Addresses.
What do I need to do?
Does your company use allowlists?
If not, no action is required. Your services will continue to work as they did before the move to the new IPv4 addresses.
If yes, you need to update your allowlists to include the new IPv4 addresses before January 10, 2025, to keep your DigiCert services running as they did before the move to the new IPv4 addresses.
Affected platforms:
CertCentral®
CertCentral® Europe
DigiCert® PKI Platform 8
QuoVadis® TrustLink
DigiCert® ONE USA, Netherlands, Switzerland, and Japan instances*
Affected services:
TLS OCSP
TLS CRL
PKI Platform 8 CRLs
PKI Platform 8 Certificate Authority (CA) certificates
PKI client download
Wichtig
*If your Trust Lifecycle, Software Trust, or Document Trust Manager (USA, CH, NL, JP) uses public certificates from CertCentral Global, CertCentral Europe, or PKI Platform 8, you may want to add these IP addresses to your allowlist.
OCSP or CRL distribution endpoints using any of the following subdomains are not affected:
one.digicert.com
one.nl.digicert.com
one.ch.digicert.com
one.digicert.co.jp
one.oracle.digicert.com
January 8, 2025
End of life for HTTPS web-based WHOIS lookups and reuse of domain validations where a WHOIS lookup was used
On January 8, 2025, DigiCert will make the following changes to our domain validation process per new industry requirements:
Stop using manual/HTTPS web-based WHOIS lookups to obtain domain contact information for domain control validation.
No longer reuse existing domain validations where a manual/HTTPS web-based WHOIS lookup was used to collect domain contact information, regardless of whether the previously obtained information is within the allowed 397-day reuse period.
These changes affect all web-based WHOIS domain validations, including the following certificate types: TLS, Verified Mark and Common Mark, Secure Email (S/MIME), DirectAssured, and DirectTrust. See End of life for WHOIS-based DCV methods.
How does this affect me?
Are you using the WHOIS-based Email or Phone DCV methods to validate your domains, and has DigiCert’s automated WHOIS lookup ever failed to retrieve your desired email address for your domains?
If you answered yes to both questions above, then you are probably impacted. Starting January 8, your email or phone domain control validation could fail if it relies on a manual/HTTPS web-based WHOIS lookup by our validation agents.
Wichtig
The manual/HTTPS web-based WHOIS lookup changes do not affect your existing certificates. Your certificates will remain valid and trusted until they expire.
What do I need to do?
Do you rely on immediate certificate issuance?
If not, then no action is required until the next time you order a certificate.
The next time you order a certificate, you must choose a non-WHOIS-reliant domain control validation (DCV) method, such as DNS Text Record. To continue validating domains via email, set up a DNS TXT Email Contact or a Constructed Email address.
If yes, then action is required to avoid potential disruption to your certificate issuance.
For those that rely on instant issuance of certificates, you must revalidate your domains using a non-WHOIS-reliant DCV method , such as DNS Text Record, or to continue validating domains via email, set up a DNS TXT Email Contact or a Constructed Email address before January 8.
Why will DigiCert stop using manual/HTTPS web-based WHOIS lookups and reusing existing domain validations where a manual/HTTPS web-based WHOIS lookup was used?
The industry recently adopted Ballot SC-80v3: Sunset the Use of WHOIS to Identify Domain Contacts and Relying DCV Methods. To comply with industry changes mandated by the ballot, certificate authorities (CAs), such as DigiCert, must stop using WHOIS to identify domain contacts for email, fax, SMS, postal mail, and phone domain control validation (DCV) methods. Note that DigiCert only supports the email and phone WHOIS-based DCV methods.
References
Recent changes
December 9, 2024
DigiCert 2025 maintenance schedules
To make planning your certificate, services, and platform-related tasks easier, DigiCert has scheduled our 2025 maintenance windows in advance. We keep these schedules up to date with all maintenance information, including details about how maintenance will affect your services.
Maintenance schedules:
With customers worldwide, we understand there is no best time for everyone. However, after reviewing the data on customer usage, we selected times that would impact the fewest amount of our customers.
Maintenance schedule guidelines and what to expect:
Maintenance is scheduled for the first weekend of each month unless otherwise noted.
Each maintenance window is scheduled for 2 hours.
Although we have redundancies to protect your service, some DigiCert services may be unavailable.
Normal operations will resume once the maintenance is completed.
To get live maintenance updates, subscribe to the DigiCert Status page. Your subscription includes email alerts for when maintenance begins and when it ends.
If you have questions or need more information about these maintenance windows, contact your account manager or DigiCert Support.
December 7, 2024
Upcoming scheduled Europe maintenance
The ADSS and PrimoSign signing services and QuoVadis TrustLink Enterprise will be down during scheduled Europe maintenance on December 7, 2024, 17:00 - 19:00 CET (16:00 - 18:00 UTC).
How does this affect me?
ADSS maintenance – three-hour downtime
The ADSS signing service upgrade starts at 17:00 CET (UTC 16:00). From 17:00 to 20:00 CET (16:00 to 19:00 UTC), the ADSS signing service in our DigiCert® Document Trust Manager Switzerland location will be down for approximately three hours.
Note: This upgrade will last three hours, extending the downtime by one hour past the scheduled maintenance window.
PrimoSign maintenance – 60-minute downtime
The PrimoSign signing service maintenance starts at 17:00 CET (UTC 16:00). At this time, the PrimoSign signing services in our DigiCert® Document Trust Manager Switzerland location will be down for approximately 60 minutes.
QuoVadis TrustLink Enterprise – 10-minute downtime
The TrustLink Enterprise maintenance starts at 17:00 CET (UTC 16:00). At this time, TrustLink Enterprise in our Netherlands and Switzerland locations will be down for approximately 10 minutes.
Affected services:
ADSS signing service in our DigiCert® Document Trust Manager Switzerland location
PrimoSign signing service in our DigiCert® Document Trust Manager Switzerland location
QuoVadis TrustLink Enterprise in our Netherlands and Switzerland locations
APIs will return "503 services unavailable" errors.
Requests placed during this window that receive a "503 services unavailable" error message will need to be placed again after services are restored.
What can I do?
Plan accordingly:
Schedule high-priority PrimoSign and ADSS signing service document signings before or after the maintenance window.
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
The PrimoSign signing service in our DigiCert® Document Trust Manager USA location will be down for approximately 60 minutes during scheduled Global maintenance on December 7, 2024, 22:00 – 24:00 MST (December 8, 2024, 05:00 – 07:00 UTC).
How does this affect me?
The maintenance starts at 22:00 MST (05:00 UTC). At this time, the PrimoSign signing services will be down for approximately 60 minutes.
Affected services
The PrimoSign signing service in our DigiCert® Document Trust Manager USA location
What can I do?
Plan accordingly:
Schedule high-priority PrimoSign signing service document signings before or after the maintenance window.
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Global 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
November 16, 2024
Upcoming critical maintenance on the ADSS signing service in our Switzerland location
On November 16, 2024, 17:00 - 19:00 CET (16:00 - 18:00 UTC), DigiCert must perform critical maintenance on the ADSS signing service in our DigiCert® Document Trust Manager Switzerland location. During this time, the ADSS signing service will be down for approximately two hours.
How does this affect me?
The ADSS signing service maintenance starts at 17:00 CET (UTC 16:00). From 17:00 to 19:00 CET (16:00 to 18:00 UTC), the ADSS signing services will be down for approximately two hours.
Affected services
Document Trust Manager's ADSS signing service in the DigiCert® ONE Switzerland location
What can I do?
Plan accordingly:
Schedule high-priority document signings before or after the maintenance window.
Expect interruptions if you use the APIs for automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
November 9, 2024
Upcoming scheduled Europe maintenance
DigiCert will perform scheduled maintenance on November 9, 2024, 17:00 - 19:00 CET (16:00 - 18:00 UTC).
How does this affect me?
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
Wichtig
We previously communicated that ADSS signing service maintenance would occur during scheduled maintenance on November 9 with a 60-minute downtime. However, the scope of the work has changed, requiring us to reschedule it to November 16, 2024, and extend the downtime to two hours. See the November 16 change log entry.
What can I do?
Plan accordingly:
Schedule high-priority ADSS signing service document signings before or after the maintenance window.
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
DigiCert will perform scheduled maintenance on November 9, 2024, 22:00 – 24:00 MST (November 10, 2024, 05:00 – 07:00 UTC).
How does this affect me?
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Global 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
October 8, 2024
CertCentral Services API: Bug fix for API order certificate endpoint responses
DigiCert fixed a bug in the Order TLS certificate API endpoints where we returned token and random value information for TLS certificate requests placed using the Email DCV method to validate domains. The random value information was confusing as customers did not expect to receive nor need to use a DCV random value to complete their domain validation.
In the API, this bug caused the TLS certificate response to return the domains: dcv_token object and dcv_random_value. However, this bug only appeared when specific domain validation events related to a domain on the certificate request occurred prior to placing a request.
Starting October 8, 2024, DigiCert will no longer return the domains: dcv_token object and dcv_random_value in the TLS certificate order responses for certificate requests placed using the Email DCV method to validate domains.
Requirements to produce this bug:
Prevalidate the domain using a random value-based domain control validation (DCV) method.
Submit the domain for revalidation using a random value-based DCV method.
Place a TLS certificate order that includes the domain with
dcv_method: email/null.
Result: The TLS certificate order's API response will contain a DCV random value even though that value is not relevant to an order when the Email DCV method is selected.
What do I need to do?
When you place a TLS certificate order with dcv_method: email/null, are you expecting to receive the domains: dcv_token object and the dcv_random_value in your order response?
If not, then no action is required.
If yes, you may need to update your API implementation to no longer expect the
domains: dcv_tokenobject and thedcv_random_valuein your order response. See our Order TLS certificate API endpoint documentation.Since our API returned the correct response in all other situations for TLS certificate requests placed using the Email DCV method to validate domains, one of the following is likely true:
You never received an API response with the token and random value information.
Your API integration handled this bug correctly and did not generate errors.
Example response starting October 8, 2024
The API returned the correct response below for TLS certificate requests placed using the Email DCV method not meeting the bug requirements before October 8, 2024.
Example of a response affected by this bug before October 8, 2024
Only when a TLS certificate request met the requirements mentioned above did the response return the domains: dcv_token object and dcv_random_value.
October 5, 2024
Upcoming scheduled Europe maintenance
Some DigiCert services will be down for approximately 10 minutes during scheduled Europe maintenance on October 5, 2024, 17:00 - 19:00 CEST (15:00 - 17:00 UTC).
How does this affect me?
The maintenance starts at 17:00 CEST (UTC 15:00). At this time, TrustLink Enterprise and the ADSS signing services will be down for approximately 10 minutes.
Affected services
QuoVadis’ ADSS signing service in the following locations:
TrustLink Enterprise Netherlands
TrustLink Enterprise Switzerland
Document Trust Manager's ADSS signing service in the following locations:
DigiCert® ONE Netherlands
DigiCert® ONE Switzerland
QuoVadis TrustLink Enterprise in the following locations:
Netherlands
Switzerland
What can i do?
Plan accordingly:
Schedule high-priority ADSS signing service document signings before or after the maintenance window.
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
DigiCert will perform scheduled maintenance on October 5, 2024, 22:00 – 24:00 MDT (October 6, 2024, 04:00 – 06:00 UTC).
How does this affect me?
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Global 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
September 25, 2024
Common Mark Certificates available now
For customers who don't have a registered trademark or who want to use a different logo that they have not trademarked, you can now get a Common Mark Certificate (CMC).
A CMC allows a company to place a non-trademarked brand logo next to the "sender" field in customer inboxes—even before the message is opened. The logo that acts as confirmation of your domain's DMARC (Domain-based Message Authentication, Reporting, and Conformance) status and your organization's authenticated identity.
DigiCert's CMC support two logo options:
Prior Use Mark
The Prior Use Mark is an unregistered Trademark, often called a Common Law Mark or Common Law Trademark. Unregistered or common law marks often use the "TM" or "SM" symbols.
Prior Use requirements:
You must have used the logo for at least 12 months before the Mark verification date on a domain you control.
We can verify your logo use with the Archive Webpage Archive.org.
Modified Registered Trademark
Learn more about Common Mark Certificates:
Don't see the Common Mark Certificates in your account?
If you do not see Common Mark Certificates in your account, it may be because we are not offering the product to all account types yet.
To get help enabling Common Mark Certificates for your CertCentral account, contact your account manager or DigiCert Support.
It is also possible that the product is available, but one of your CertCentral account’s administrators turned the product off in Product Settings.
To disable CMC or change availability of CMC in your CertCentral account, visit the Product Settings page. In the left main menu, go to Settings > Product Settings.
September 17, 2024
CertCentral Services API: Improved rate limits
DigiCert is happy to announce that we increased the rate limits for our CertCentral Services API. DigiCert APIs now enforce a rate limit of 1000 requests per 3 minutes. The short-term rate limit of 100 requests per 5 seconds remains the same.
Note: Previously, DigiCert APIs enforced a rate limit of 1000 requests per 5 minutes.
September 10, 2024
CertCentral Services API: Making required fields optional for our Edit user/Edit service user endpoint
We updated the Edit user/Edit service user endpoint, and now the username, first_name, and last_name parameters are optional. Previously, these parameters were always required.
When editing a CertCentral user, you only need to include the parameters mentioned above in your request if you change the user's first name, last name, or username.
With service users, you can only update the email address associated with the service user. You cannot change the service user's username, first name, or last name.
You only need to include the
emailparameter in your edit service user request.
September 7, 2024
Upcoming scheduled Europe maintenance
Some DigiCert services will be down for approximately 10 minutes during scheduled Europe maintenance on September 7, 2024, 17:00 - 19:00 CEST (15:00 - 17:00 UTC).
How does this affect me?
The maintenance starts at 17:00 CEST (UTC 15:00). At this time, TrustLink Enterprise and the ADSS signing services will be down for approximately 10 minutes.
Affected services:
QuoVadis’ ADSS signing service in the following locations
TrustLink Enterprise Netherlands
TrustLink Enterprise Switzerland
Document Trust Manager's ADSS signing service in the following locations:
DigiCert® ONE Netherlands
DigiCert® ONE Switzerland
QuoVadis TrustLink Enterprise in the following locations:
Netherlands
Switzerland
What can I do?
Plan accordingly:
Schedule high-priority ADSS signing service document signings before or after the maintenance window.
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
DigiCert will perform scheduled maintenance on September 7, 2024, 22:00 – 24:00 MDT (September 8, 2024, 04:00 – 06:00 UTC).
How does this affect me?
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Global 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
September 4, 2024
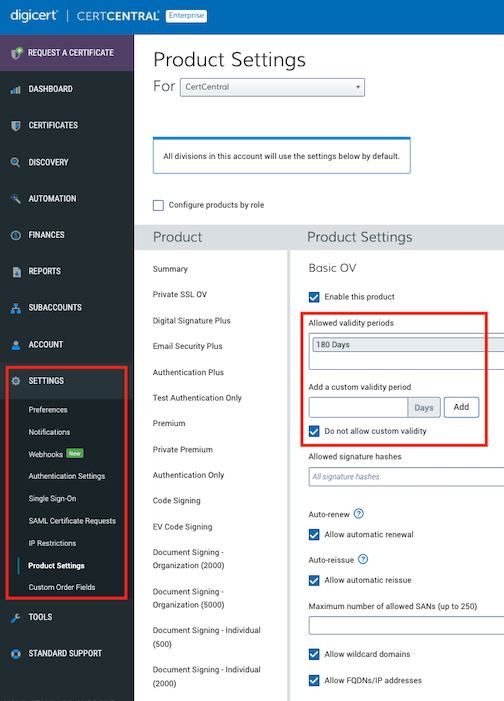
CertCentral: Add a custom validity period to your TLS certificate request forms
We are happy to announce that you can now add custom, allowed validity periods to your TLS certificate request forms. For example, if you want all your Basic OV certificate orders to have a 180-day validity, go to the Product Settings page for a Basic OV certificate and add a 180-day custom validity period to the request form.
Wichtig
Only TLS certificates allow you to add a custom validity period to your certificate request forms.
See for yourself
We will add a 180-day custom validity period to the Basic OV certificate request forms in this example.
In CertCentral, go to Settings > Product Settings.
On the Product Settings page, in the Product column, select Basic OV.
In the Product Settings column for Basic OV, under Add a customer validity period, enter 180 days and select Add.
Scroll to the bottom of the page and select Save Settings.
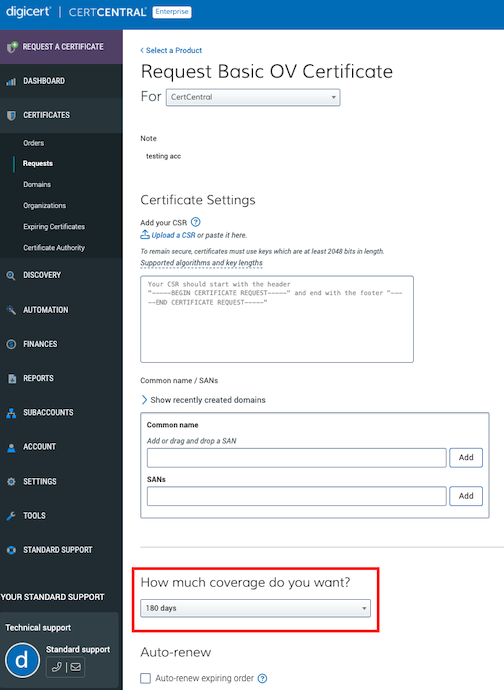
Now, order a Basic OV TLS certificate.
On the Request Basic OV certificate page, in the How much coverage do you want menu, you should see your custom 180 days validity period.
Screenshots
Product Settings
Request Basic OV certificate
September 3, 2024
DigiCert will move all Secure Email (S/MIME) certificate issuance to our new intermediate CA certificates
On September 3, 2024, DigiCert will remove all public Secure Email (S/MIME) Intermediate CAs from our S/MIME certificate issuance process that don’t comply with the S/MIME Baseline Requirements in CA/Browser Forum.
For more details about the affected S/MIME certificates and which ICA certificates we are replacing, see our knowledge base article, New Secure Email (S/MIME) Intermediate CA certificates 2024.
Wichtig
Background
On June 26, DigiCert switched the default issuance of public Secure Email (S/MIME) certificates to new industry-compliant public intermediate CA (ICA) certificates. See our June 26, 2024 change log entry.
However, if you needed more time to make the transition, we allowed you to continue using your current ICA certificate until September 3, 2024.
ICA certificate replacements
See the DigiCert Trusted Root Authority Certificates page to download copies of DigiCert ICA and root certificates.
Platform | New default ICA certificate |
|---|---|
CertCentral Global | DigiCert Assured G2 SMIME RSA4096 SHA384 2024 CA1 |
PKI Platform 8 | DigiCert Assured G2 mPKI SMIME RSA4096 SHA384 2023 CA1 |
Trust Lifecycle |
|
How does switching ICA certificates affect me?
If you install the DigiCert-provided ICA certificate included with your issued Secure Email (S/MIME) certificate, this change will not affect you, and no action will be required. Starting September 3, 2024, the new default ICA certificate will automatically come with your issued Secure Email (S/MIME) certificate (new, renewal, or reissued).
How does switching ICA certificates affect my existing certificates?
Rolling out new ICA certificates does not affect existing certificates. Valid Secure Email (S/MIME) certificates issued from a replaced ICA certificate continue to be trusted until they expire.
Starting September 3, 2024, DigiCert will issue new, renewed, and reissued Secure Email (S/MIME) certificates from new ICA certificates.
Best practices
We recommend always including the DigiCert-provided ICA certificate with every certificate you install. This recommendation has always been the best practice to ensure that ICA certificate replacements do not disrupt your certificate-related processes and that your certificates are trusted.
August 27, 2024
CertCentral: Now showing revocation reason on certificate revocation requests
To make it easier for administrators to approve or reject certificate revocation requests, we now show the reason for the revocation on the pending certificate revoke requests. If the reason for the revocation is a key compromise, we also show the revocation date*.
Example: Revoke request for key compromise
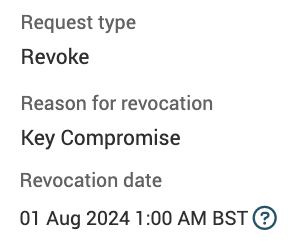
*Note: When revoking a code signing certificate because the private key was compromised, you can set the revocation date to a specific date if you know when the key compromise happened. Code signing signatures applied before the key compromise date remain valid and trusted. Only signatures applied after that date are invalidated and untrustworthy.
CertCentral: Now showing high-risk domain information on our pending certificate orders
To make it easier to track high-risk domains on a pending certificate order, we now include a Check domain risk section when an order includes high-risk domains. DigiCert is responsible for completing the high-risk check. The check returns one of the following statuses: pending, approved, or rejected.
When a domain fails the high-risk check, you can do one of the following:
Cancel the order and place a new one without the high-risk domain.
Edit the pending order and remove the high-risk domain. After the certificate is issued, you can reissue it and add a domain at no extra cost.
Edit the pending order and replace the high-risk domain.
The domain risk information appears on the Order details page, on the Details tab, in the Certificate status section.
OV and EV TLS/SSL certificates
Under What DigiCert needs to do, we include the new Check domain risk section with the risk check status for each high-risk domain.
DV TLS/SSL certificates
Next to What you need to do, we add a What DigiCert needs to do column where we include the new Check domain risk section with the risk check status for each high-risk domain.
Secure Email for Business and Organization certificates
Under What DigiCert needs to do, we include the new Check domain risk section with the risk check status for each high-risk domain.
August 19, 2024
DigiCert shutting down Symantec timestamping service
On August 19, 2024, at 09:00 MDT (15:00 UTC), DigiCert will shut down our Symantec timestamping service. DigiCert customers who are still relying on this service must use the DigiCert timestamping service instead.
Wichtig
Note: The Symantec timestamping service shutdown was originally scheduled for July 24, 2024 and then rescheduled for July 29, 2024 and then August 14, 2024.
How does this affect me?
Do your code or document signing signatures use the Symantec timestamping URLs listed below?
sha256timestamp.ws.symantec.com
sha256timestamp.ws.digicert.com
No, I don't use the Symantec timestamping service.
Then, no action is required. This change will not affect your signing processes or signed code and documents.
Yes, I use the Symantec timestamping service.
Then, action is required. This change may affect software build processes, end users trying to verify if a software update is legitimate or end users trying to verify that a signed document is still valid.
For example:
Software build processes may be broken by executables signed with the legacy Symantec timestamp service starting August 19.
Documents and code signed with the legacy Symantec timestamp service may not retain the desired date of existence or execution starting August 19.
What do I need to do?
By August 19, 2024, you must update your code signing and document signing processes to use the DigiCert timestamping URL: timestamp.digicert.com.
Additionally, you may need to add the DigiCert timestamping service domain or IP address to your allowlist:
timestamp.digicert.com
216.168.244.9
How does this affect existing signatures with Symantec timestamp URLs?
Code and document signing signatures using Symantec timestamping service timestamps applied before August 19 are not affected by this change. You can continue to rely on this timestamping service to verify that your code and document signatures are valid and that the signed code and documents have not been modified or corrupted.
August 14, 2024
DigiCert shutting down Symantec timestamping service
DigiCert has postponed shutting down our Symantec timestamping service to August 19, 2024. See our August 19. 2024 change log entry.
August 6, 2024
CertCentral: Updated the account sign in pages
We updated the DigiCert CertCentral Sign in pages. The next time you sign in to your account, the page will have a new look with a new Other sign-in options menu that includes the following options:
Sign in to CertCentral
CertCentral Europe
We made it easier for our CertCentral Europe customers who accidentally land on our CertCentral landing page to access the CertCentral Europe sign-in page.
My company's SSO
For those using an Identity Provider, we made it easier to find the sign in with company's SSO option.
Sign in to CertCentral Europe
CertCentral
We made it easier for our CertCentral customers who accidentally land on our CertCentral Europe landing page to access the CertCentral sign-in page.
My company's SSO
For those using an Identity Provider, we made it easier to find the sign in with company's SSO option.
Preview the new CertCentral sign in pages
CertCentral: Maximum 30 verified contact limit for adding "new" verified contacts to a certificate request
CertCentral implemented a 30 verified contact limit for adding "new" verified contacts to a certificate request. Now, you can only add up to 30 "new" verified contacts to an EV TSL, Code Signing, EV Code Signing, or Verified Mark certificate request.
This 30 "new" verified limit affects certificate requests made via CertCentral and CertCentral Services API integration.
How does this affect me?
The next time you request a certificate that requires verified contacts, you can only add up to 30 "new" verified contacts.
Is there a limit for adding "existing" verified contacts?
No, there is no limit on the number of "existing" verified contacts you can add. Add as many as needed to get the order approved. However, only one must approve the order.
August 3, 2024
Upcoming scheduled Europe maintenance
The ADSS signing services will be down for approximately 30 minutes during scheduled Europe maintenance on August 3, 2024, 09:00 - 11:00 MDT (15:00 - 17:00 UTC).
How does this affect me?
The ADSS signing service maintenance starts at 09:00 MDT (UTC 15:00). At this time, the ADSS signing services in our Document Trust Manager and TrustLink Enterprise Netherlands and Switzerland locations will be down for approximately 30 minutes.
Affected services:
Document Trust Manager's ADSS signing service in the following locations:
DigiCert® ONE Netherlands
DigiCert® ONE Switzerland
QuoVadis ADSS signing service in the following locations:
TrustLink Enterprise Netherlands
TrustLink Enterprise Switzerland
What can I do?
Plan accordingly:
Schedule high-priority ADSS service document signings before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
DigiCert will perform scheduled maintenance on August 3, 2024, 22:00 – 24:00 MDT (August 4, 2024, 04:00 – 06:00 UTC).
How does this affect me?
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Global 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
July 30, 2024
New DigiCert certificate status IPv6 addresses
On July 30, 2024, at 10:00 MDT (16:00 UTC), DigiCert will assign new dedicated IPv6 addresses to our Online Certificate Status Protocols (OCSPs), Certificate Revocation Lists (CRLs), and a few other DigiCert services.
For more details about the new IPv6 addresses, see our knowledge base article, DigiCert Certificate Status IP Addresses.
What do I need to do?
Does your company use allowlists, and does it support or plan to support IPv6 addresses?
If not, no action is required. Your services will continue to work as before the addition of the new IPv6 addresses.
If yes, you need to update your allowlists to include the new IPv6 addresses by July 30, 2024, to keep your DigiCert services running as before the addition of the new IPv6 addresses.
Affected platforms
CertCentral®
CertCentral® Europe
PKI Platform 8
QuoVadis TrustLink®
DigiCert® ONE*
Wichtig
*If your Trust Lifecycle, Software Trust, or Document Trust Manager (USA, CH, NL, JP) uses public certificates from CertCentral Global, CertCentral Europe, or PKI Platform 8, you may want to add these IPv6 addresses to your allowlist.
OCSP or CRL distribution endpoints using any of the following subdomains are not affected:
one.digicert.com
one.nl.digicert.com
one.ch.digicert.com
one.digicert.co.jp
one.oracle.digicert.com
July 29, 2024
DigiCert shutting down Symantec timestamping service
DigiCert has postponed shutting down our Symantec timestamping service to August 19, 2024. See our August 19. 2024 change log entry.
July 24, 2024
DigiCert shutting down Symantec timestamping service
DigiCert has postponed shutting down our Symantec timestamping service to August 19, 2024. See our August 19. 2024 change log entry.
July 23, 2024
CertCentral: New DCV method for validating your domains
We are happy to announce that we now support a new domain control validation (DCV) method in CertCentral and the CertCentral Services API—HTTP Practical Demonstration with unique filename.
How does HTTP Practical Demonstration with unique filename work?
With this method, you host a file with a random filename that contains a DigiCert-generated random value (provided for the domain in your CertCentral account) at a predetermined location on your website, for example http://{domain-name}/.well-known/pki-validation/9ur837JIY4134jc20J39jdl3.txt.
Once the file is created and placed on your site, DigiCert visits the specified URL to confirm the presence of our random value.
Wichtig
DV TLS certificates do not support the HTTP Practical Demonstration with unique filename DCV method.
Example use case
Use 302 redirects to point addresses to a central authentication server. The server hosts all HTTP authentication files with unique file names.
Documentation
API documentation
July 13, 2024
Upcoming scheduled Europe maintenance
The QuoVadis TrustLink Enterprise Netherlands instance will be down for approximately 40 minutes during scheduled Europe maintenance on July 13, 2024, 09:00 - 11:00 MDT (15:00 - 17:00 UTC).
How does this affect me?
The maintenance starts at 15:00 UTC. From 09:00 – 09:40 MDT (15:00 to 15:40 UTC), our TrustLink Enterprise Netherlands instance will be down for approximately 40 minutes while we do infrastructure-related maintenance requiring server restarts.
Affected QuoVadis Services
TrustLink Enterprise Netherlands instance
API notes
APIs will return "503 services unavailable" errors.
Requests placed during this window that receive a "503 services unavailable" error message will need to be placed again after services are restored.
What can I do?
Plan accordingly:
Schedule high-priority certificate-related tasks before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
DigiCert will perform scheduled maintenance on July 13, 2024, 22:00 – 24:00 MDT (June 2, 2024, 04:00 – 06:00 UTC).
How does this affect me?
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Global 2024 maintenance schedule for maintenance dates and times
Services will be restored as soon as the maintenance is completed.
July 11, 2024
CertCentral: New minimum password length requirement for account sign-in
On July 11, 2024, DigiCert updated the minimum password length requirements for CertCentral from 10 to 12 characters. If your password is less than 12 characters, the next time you change it (your password expired or you forgot it), you will be required to create a 12-character password instead of a 10- or 11-character one.
What do I need to do?
No action is required. If your password is less than 12 characters, CertCentral will require you to start using a 12-character password the next time you need to change it. However, DigiCert recommends changing it the next time you sign in to CertCentral.
How do I change my password?
In CertCentral, in your "name" menu (top right), select My Profile.
On the Profile Settings page, select Update Password.
Enter your current password, enter your new 12-character or longer password and confirm it, then select Save Changes.
July 8, 2024
CertCentral: Improvements to CSR browser generation for Secure Email certificates
We are happy to announce that we improved the CSR browser generation option for Secure Email certificates. Now, you can choose the algorithm and key size for generating your CSR via your browser.
To use the RSA algorithm, select an RSA key size: 2048, 3072, or 4096.
To use the ECC algorithm, select an ECC key size: p-256 or p-384.
Previously, the CSR browser generation option only supported RSA 2048-bit certificates.
See for yourself
In your CertCentral account, in the left main menu, go to Request a Certificate > Secure Email Certificates and select a Secure Email certificate.
On the Request Secure Email Certificate page, in the Add your CSR section, select Generate CSR in the browser.
Under Additional certificate options, in the Certificate key size menu, you can select the algorithm and key size you want to use to generate your CSR.
For more detailed instructions on how to order your Secure Email certificate, see Secure Email Certificates.
CertCentral: Improvements to signing algorithm selection for Secure Email certificates
We are happy to announce that you can now use the RSASSA-PSS signing algorithm to sign your emails when placing Secure Email certificate orders in CertCentral. Previously, this was only supported when placing Secure Email certificate orders via the Services API. See the change log entry for December 13, 2023.
Items to note about the RSASS-PSS signing algorithm:
To get an RSASSA-PSS signature, you must use an ICA certificate with an RSA signature.
The industry does not support issuing ECC certificates with an RSASSA-PSS signing algorithm. If you require an RSASSA-PSS signature, get an RSA certificate instead.
See for yourself
In your CertCentral account, in the left main menu, go to Request a Certificate > Secure Email Certificates and select a Secure Email certificate.
On the Request Secure Email Certificate page, in the Add your CSR section, select Generate CSR in the browser.
Note: You can also select I have my CSR and add an RSA CSR. Then, skip to step 4.
Under Additional certificate options, in the Certificate key size menu, select the RSA algorithm and key size you want to use to generate your CSR.
In the Signature hash menu, you can select the RSA signature hash and an RSA or RSASSA-PSS signing algorithm.
SHA-256 with RSA
SHA-384 with RSA
SHA-512 with RSA
SHA-256 with RSASSA-PSS
SHA-384 with RSASSA-PSS
SHA-512 with RSASSA-PSS
For more detailed instructions on how to order your Secure Email certificate, see Secure Email Certificates.
June 26, 2024
DigiCert moving to new Secure Email (S/MIME) intermediate CA certificates
On June 26, 2024, at 10:00 MDT (16:00 UTC), DigiCert will move the default issuance of public Secure Email (S/MIME) certificates to new industry-compliant public intermediate CA (ICA) certificates.
Wichtig
Update: DigiCert has postponed the move to new ICA certificates to June 26, 2024. We originally planned this move for June 25, 2024.
For more details about the affected S/MIME certificates and which ICA certificates we are replacing, see our knowledge base article, New Secure Email (S/MIME) Intermediate CA certificates 2024.
ICA certificate replacements
To download copies of DigiCert ICA and root certificates, see the DigiCert Trusted Root Authority Certificates page.
Platform | New default ICA certificate |
|---|---|
CertCentral Global | DigiCert Assured G2 SMIME RSA4096 SHA384 2024 CA1 |
PKI Platform 8 | DigiCert Assured G2 mPKI SMIME RSA4096 SHA384 2023 CA1 |
Trust Lifecycle |
|
How does switching ICA certificates affect me?
If you install the DigiCert-provided ICA certificate included with your issued Secure Email (S/MIME) certificate, this change will not affect you, and no action will be required. Starting June 26, 2024, the new default ICA certificate will automatically come with your issued Secure Email (S/MIME) certificate (new, renewal, or reissued).
How does switching ICA certificates affect my existing certificates?
Rolling out new ICA certificates does not affect existing certificates. Active Secure Email (S/MIME) certificates issued from a replaced ICA certificate continue to be trusted until they expire.
Starting June 26, 2024, DigiCert will issue new, renewed, and reissued Secure Email (S/MIME) certificates from new ICA certificates. When installing your S/MIME certificates, always include the DigiCert-provided ICA certificate.
Best practice
We recommend always including the DigiCert-provided ICA certificate with every certificate you install. This recommendation has always been the best practice to ensure that ICA certificate replacements do not disrupt your certificate-related processes and that your certificates are trusted.
PKI Platform 8 items to note
Starting June 26, 2024, DigiCert will begin migrating your PKI Platform 8 public S/MIME issuance to the new, industry-compliant, shared CA. See ICA certificate replacements above.
Those using Local Key Management Storage (LKMS) to store their private keys must add the new ICA certificate to their local LKMS once available. Otherwise, you cannot continue to store your private keys locally.
What if I need more time before switching ICA certificates?
Contact your account manager or DigiCert Support. We will set up your account so you can continue to use the ICA certificates you are using now.
However, on September 3, 2024, DigiCert must move you to the new ICA certificates. The current ICA certificates are no longer industry-compliant and cannot be used to issue Secure Email (S/MIME) certificates after that date.
CertCentral: New way to create API keys for your account
Tired of replacing API keys when a developer gets promoted, changes departments, retires, or leaves the company?
We are happy to announce that you can now create user-independent API keys for your CertCentral account. Instead of adding an API key linked directly to a user in your account, you can create a service user.
What is a service user?
A service user has API-only access to your account. Only administrators can create service users. When creating a service user, you link the administrator's permissions to the key.
Wichtig
Service user creation is tracked in your CertCentral audit logs: Date & Time, User, Activity, Source, IP Address, Division, and Country.
By default, the service user is authorized to perform any actions the administrator can. However, you can limit the API key permissions as needed.
When managing your service users, you can create multiple service users, or you can create a service user and add multiple API keys for the service user.
See for yourself
In CertCentral, in the left main menu, go to Automation > API Keys.
On the API Keys page, select Add API Key.
In the Add API Key window, enter a Description for the new key.
In the User menu, select Create new service user.
Exit or continue the process as needed. For more detailed instructions, see Generate an API key.
Documentation
June 25, 2024
DigiCert moving to new Secure Email (S/MIME) intermediate CA certificates
On June 25, 2024, at 10:00 MDT (16:00 UTC), DigiCert will move the default issuance of public Secure Email (S/MIME) certificates to new industry-compliant public intermediate CA (ICA) certificates.
Wichtig
Update: DigiCert has postponed the move to new ICA certificates to June 26, 2024. See our June 26, 2024, change log entry.
June 11, 2024
CertCentral: Renewing the certificate for DigiCert's SAML metadata
On June 11, 2024, at 10:00 MDT (16:00 UTC), DigiCert will replace the expiring certificate for CertCentral's SAML metadata. For most, this replacement will go unnoticed.
However, if you are using SAML Single Sign-on (SSO) or the SAML certificate requests feature, you may need to update your SAML integration to keep it working as it did before we replaced the certificate.
I use SAML SSO/certificate requests – What should I do?
When configuring your SAML to CertCentral connection, you must add the DigiCert service provider (SP) metadata to your identity provider's (IdP) metadata. You either added the dynamic URL for DigiCert's SP metadata or the XML formatted SP metadata provided by DigiCert.
I added the Dynamic URL for DigiCert's SP metadata.
No action is required.
With the dynamic URL, your DigiCert SP metadata is updated automatically in your IdP if the DigiCert SP metadata ever changes.
I added the static XML formatted SP metadata provided by DigiCert.
Action is required!
With static XML, you must manually update your DigiCert SP metadata in your IdP if the DigiCert SP metadata ever changes.
On June 11, 2024, at 10:00 MDT (16:00 UTC), you must manually update the DigiCert SP metadata in your IdP.
To update your IdP, sign in to your CertCentral account, download an updated static XML file with DigiCert's SP metadata, and then add it to your IdP.
To learn more:
June 4, 2024
CertCentral: Improved DCV polling cadence
We are happy to announce that we’ve updated our automatic domain control validation (DCV) checks, also called DCV polling, for DNS TXT, DNS CNAME, and HTTP practical demonstration DCV methods.
What changed?
Now, DCV polling runs for ten days after you submit your public SSL/TLS certificate order, submit a domain for prevalidation, or change the DCV method for a domain. Additionally, we extended Interval 3, checking every fifteen minutes for one day, and combined Intervals 4 and 5, checking every hour for ten days.
New DCV polling cadence:
Interval 1—Every one minute for the first 15 minutes
Interval 2—Every five minutes for an hour
Interval 3—Every fifteen minutes for a day
Interval 4—Every hour for 10 days
Previous DCV polling cadence:
Interval 1—Every minute for the first 15 minutes
Interval 2—Every five minutes for an hour
Interval 3—Every fifteen minutes for four hours
Interval 4—Every hour for a day
Interval 5—Every four hours for a week
For more information about DCV polling and supported DCV methods:
June 1, 2024
Upcoming scheduled Europe maintenance
The QuoVadis TrustLink Enterprise Netherlands instance will be down for approximately 40 minutes during scheduled Europe maintenance on June 1, 2024, 09:00 - 11:00 MDT (15:00 - 17:00 UTC).
How does this affect me?
The maintenance starts at 15:00 UTC. From 09:00 – 09:40 MDT (15:00 to 15:40 UTC), our TrustLink Enterprise Netherlands instance will be down for approximately 40 minutes while we do infrastructure-related maintenance requiring server restarts..
Affected QuoVadis Services
TrustLink Enterprise Netherlands instance
API notes
APIs will return "503 services unavailable" errors.
Requests placed during this window that receive a "503 services unavailable" error message will need to be placed again after services are restored.
What can I do?
Plan accordingly:
Schedule high-priority certificate-related tasks before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
DigiCert will perform scheduled maintenance on June 1, 2024, 22:00 – 24:00 MDT (June 2, 2024, 04:00 – 06:00 UTC).
How does this affect me?
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Global 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
May 25, 2024
Upcoming critical maintenance for CertCentral Global
On May 25, 2024, 22:00 – 24:00 MDT (May 26, 04:00 – 06:00 UTC), DigiCert must perform critical maintenance on CertCentral Global. During this time, CertCentral will be down or experience service degradation for 30 minutes.
How does this affect me?
The CertCentral maintenance-related downtime/service degradation happens in two 15-minute periods.
Part 1: From 22:00 to 22:15 MDT (04:00 to 04:15 UTC), CertCentral will be down or experience service degradation for up to 15 minutes.
Part 2: From 22:45 to 23:00 MDT (04:45 to 05:00 UTC), CertCentral will again be down or experience service degradation for up to 15 minutes.
Affected services
This maintenance only affects CertCentral Global. It does not affect our Certificate Issuing Service (CIS), CertCentral Simple Certificate Enrollment Protocol (SCEP), or CertCentral Europe.
API notes
APIs may return "503 services unavailable" errors.
Requests placed during this window that receive a "503 services unavailable" error message must be placed again after services are restored.
What can I do?
Plan accordingly
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page to receive live maintenance updates, including email alerts for when maintenance begins and ends.
See the DigiCert Global 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
May 9, 2024
CertCentral: We removed the Maintain active organization validation setting
In CertCentral, on the Preferences page, we removed the Active Validation section and the Maintain active organization validation setting.
How does this affect my organization validation process?
DigiCert will continue to validate your organizations when included in your certificate request, and you can continue to submit your organizations for prevalidation.
Wichtig
Per industry standards:
EV organization validation is valid for 13 months.
OV organization validation is valid for 825 days.
References:
May 4, 2024
Upcoming scheduled Europe maintenance
DigiCert will perform scheduled maintenance on May 4, 2024, 09:00 – 11:00 MDT (15:00 – 17:00 UTC). Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page to receive live maintenance updates, including email alerts for when maintenance begins and when it ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
DigiCert will perform scheduled maintenance on May 4, 2024, 22:00 – 24:00 MDT (May 5, 2024, 04:00 – 06:00 UTC). Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page to receive live maintenance updates, including email alerts for when maintenance begins and when it ends.
See the DigiCert Global 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
April 15, 2024
CertCentral Services API: Improved Order validation status endpoint
We updated the Order validation status endpoint and added a new URL query parameter, include_risk_check. Use this parameter to check the domain risk for the order. You only need to include ?include_risk_check=true on non-DV TLS orders, as we always return the risk_status for DV TLS certificates.
cURL example:
curl -X GET \
'https://www.digicert.com/services/v2/order/certificate/{{order_id}}/validation?include_risk_check=true' \
-H 'Content-Type: application/json' \
-H 'X-DC-DEVKEY: {{api_key}}'April 6, 2024
Upcoming scheduled Europe maintenance
DigiCert ONE Switzerland and TrustLink Switzerland locations could experience downtime for approximately 30 minutes during scheduled maintenance on April 6, 2024, 09:00 – 11:00 MDT (15:00 – 17:00 UTC).
If everything goes as planned, the maintenance will not affect our DigiCert ONE Switzerland and TrustLink Switzerland customers. However, there could be service downtime if things don't go as planned.
The maintenance starts at 09:00 MDT (15:00 UTC). From 09:00 to 10:00 MDT (15:00 to 16:00 UTC), our DigiCert ONE Switzerland instance and its Managers and our TrustLink Switzerland instance could be down or experience service degradation for approximately 30 minutes.
Affected services
DigiCert ONE Switzerland
Trust Lifecycle Manager
Software Trust Manager
IoT Trust Manager
Document Trust Manager
KeyLocker
Account Manager
CA Manager
TrustLink Switzerland
API notes
APIs may return "503 services unavailable" errors.
Requests placed during this window that receive a "503 services unavailable" error message will need to be placed again after services are restored.
What can I do?
Schedule high-priority certificate-related tasks and signings (code and documents) before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page to receive live maintenance updates, including email alerts for when maintenance begins and when it ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
DigiCert will perform scheduled maintenance on April 6, 2024, 22:00 – 24:00 MDT (April 7, 2024, 04:00 – 06:00 UTC).
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page to receive live maintenance updates, including email alerts for when maintenance begins and when it ends.
See the DigiCert Global 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
March 26, 2024
CertCentral Services API: New DigiCert® KeyLocker signature endpoints
We are happy to announce, we added two endpoints to the CertCentral Services API: View KeyLocker signatures and Purchase KeyLocker signatures.
These endpoints make it easier to manage the signatures for your code signing certificate orders using the DigiCert KeyLocker provisioning method:
Get details about the number of signatures purchased and used for a code signing certificate order.
Purchase signatures for your code signing certificate order.
Wichtig
Signature purchases not yet available for subaccounts.
March 19, 2024
CertCentral: Changes to the DigiCert® KeyLocker provisioning method for Code Signing certificates
On March 19, 2024, DigiCert began enforcing technical controls on code signing certificates provisioned in DigiCert® KeyLocker, our cloud-based HSM. Additionally, we changed how KeyLocker pricing works.
New technical controls starting March 19
1,000 signatures included with each certificate provisioned on KeyLocker.
When you order or renew a code signing certificate using KeyLocker provisioning, you get 1,000 signatures per certificate. See Signature limit.
However, you can purchase more signatures as needed to meet your signing needs. See Get more KeyLocker signatures.
Only one user at a time can be assigned to a code signing certificate in KeyLocker.
For certificates issued from March 19, 2024, you can no longer use an unassigned certificate in KeyLocker to sign code. You must now be assigned to a certificate in KeyLocker to sign code with it. See User limit. See User limit.
Previously, you could leave a certificate unassigned, and any KeyLocker Signer or Key Locker Lead in your account sign code with it.
Wichtig
A KeyLocker account user with the KeyLocker lead role can update the assigned user anytime during the code signing certificate lifecycle.
KeyLocker pricing changes
Starting March 19, 2024, you will pay for signatures instead of a yearly fee for provisioning your certificate and its private key on KeyLocker.
New pricing model: Purchase signatures in increments of one thousand, $249.00 (USD) for 1,000 signatures.
Previous pricing model: Paid $90.00 (USD) a year to provision your certificate and its private key in KeyLocker.
March 16, 2024
Upcoming critical Document Trust Manager Switzerland location maintenance
On March 16, 2024, 09:00 – 11:00 MDT (15:00 – 17:00 UTC), DigiCert must perform critical maintenance on the ADSS signing service in our Document Trust Manager Switzerland location. During this time, Document Trust Manager and its ADSS signing service will be down for approximately 90 minutes.
How does this affect me?
The maintenance starts at 09:00 MDT (15:00 UTC). From 09:00 to 10:30 MDT (15:00 – 16:30 UTC), our Document Trust Manager Switzerland instance and its ADSS signing service will be down or experience service degradation for approximately 90 minutes.
What can I do?
Schedule high-priority document signings before or after the maintenance window.
Expect interruptions if you use the APIs for automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
March 13, 2024
CertCentral Services API: Secure Email for Business – secure_email_sponsor update only
This update does not affect Secure Email for Business requests submitted via CertCentral; it only affects requests submitted via the API.
We added a new optional subject DN attribute to the subject array of the Order Secure Email certificate endpoint. The new include_given_name_surname parameter lets you to control when the surname and given name are included in the subject distinguished name (DN) attributes of your issued Secure Email for Business (secure_email_sponsor) certificates.
To include the given name and surname in the subject distinguished name (DN) attributes on your issued Secure Email for Business (secure_email_sponsor) certificate, you must now use the subject object to submit values for the given name and surname (include_given_name_surname).
Wichtig
Default behavior change
Previously, when you submitted a Secure Email for Business certificate via the API, we automatically added the surname and given name from the individual array in the subject distinguished name (DN) attributes on the issued certificate.
Now, we will no longer include the surname and given name from the individual array in the subject distinguished name (DN) attributes on the issued certificate by default.
We also updated the Reissue certificate API reference to include details for using the subject object to submit values for the given name and surname (include_given_name_surname) in the subject distinguished name (DN) attributes on the issued certificate.
Example secure_email_sponsor
{
"certificate": {
"emails": [
"example@example.com"
],
...
},
...
"subject": {
"include_given_name_surname": true
},
...
}CertCentral: Updates to the user invitation process
We updated the CertCentral user invitation process to improve performance and make managing active invitations easier.
User invite expiration and deletion process
User invitations with the status Invitation Sent
CertCentral user invites expire 30 days from the time they are first sent.
Wichtig
Resending the invitation does not reset the invitation created date. After 30 days, you must send a new invitation.
User invitations with the status Needs Administrator Approval
Unapproved user invitations expire 60 days from when the invitation was created.
User invitation 365-day lifetime
After 365 days, user invitations are removed from your CertCentral account: Invitation Sent, Needs Administrator Approval, Approved, Rejected, Canceled, and Expired.
Reference documentation:
March 11, 2024
Upcoming critical Document Trust Manager Netherlands location maintenance
On March 11, 2024, 21:00 – 23:00 MDT (March 12, 03:00 – 05:00 UTC), DigiCert must perform critical maintenance on the ADSS signing service in our Document Trust Manager Netherlands location. During this time, Document Trust Manager and its ADSS signing service will be down for approximately 90 minutes.
Wichtig
We originally planned this work for April 1, 2024. However, due to business-critical needs, we must do the maintenance on March 11, 2024, MDT.
How does this affect me?
The maintenance starts at 21:00 MDT (03:00 UTC). From 21:00 to 22:30 MDT (03:00 – 04:30 UTC), our Document Trust Manager Netherlands instance and its ADSS signing service will be down or experience service degradation for approximately 90 minutes.
What can I do?
Schedule high-priority document signings before or after the maintenance window.
Expect interruptions if you use the APIs for automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
March 2, 2024
Upcoming scheduled Europe maintenance
DigiCert will perform scheduled maintenance on March 2, 2024, 09:00 – 11:00 MST (16:00 – 18:00 UTC). Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page to get live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled global maintenance
PKI Platform 8 may experience downtime or delayed responses for approximately 15 minutes during scheduled maintenance on March 2, 2024, 22:00 – 24:00 MST (March 3, 05:00 – 07:00 UTC).
PKI Platform 8 maintenance
If everything goes as planned, the maintenance will not affect our PKI Platform 8 customers. However, this maintenance is high risk, so if things don't go as planned, there could be service interruptions, delayed responses, or even downtime.
The PKI Platform 8 maintenance starts at 22:00 MST (05:00 UTC). From 22:00 to 22:30 MST (05:00 to 05:30 UTC), PKI Platform 8 may experience interruptions such as downtime (up to 15 minutes), service interruptions, or delayed responses.
API note:
APIs may return "503 services unavailable" errors.
Requests placed during this window that receive a "503 services unavailable" error message will need to be placed again after services are restored.
What can I do?
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page to get live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Global 2024 maintenance schedule for maintenance dates and times.
Plan accordingly:
Services will be restored as soon as the maintenance is completed.
February 8, 2024
CertCentral: Improvements to the SSL/TLS Duplicate certificate process
We updated the duplicate certificate request process in CertCentral. Now, when requesting a duplicate certificate, you can modify the duplicate certificate's validity if needed.
Previously, the duplicate certificate always expired when the certificate you were duplicating expired. You couldn't modify the duplicate certificate's validity.
See for yourself
In your CertCentral account, in the left main menu, go to Certificates > Orders.
On the Orders page, select the Order # of the certificate you want to duplicate.
On the certificate's Order # details page, in the Certificate actions dropdown, select Request duplicate.
On the Request Duplicate certificate page, under Certificate validity, next to Certificate details, select the pencil (edit icon) to modify the certificate's validity date.
By default, a duplicate expiration date is set to match the certificate you are duplicating
CertCentral Services API: Duplicate certificate enhancement
We updated the duplicate certificate endpoint and added support for the custom_expiration_date parameter. Use this parameter to modify the certificate validity for your duplicate certificate.
Wichtig
We automatically truncate the certificate validity if you exceed the time remaining in the order, Multi-year Plan, or the maximum 397-day certificate validity period defined by CA/B Forum baseline requirements, whichever is shorter.
JSON example:
{ "certificate": {
"common name":"example.com",
"csr":"-----BEGIN CERTIFICATE REQUEST----- … -----END CERTIFICATE REQUEST-----",
"signature_hash":sha256
},
"custom_expiration_date": "2024-10-15"
}February 3, 2024
Upcoming scheduled Europe maintenance
Some DigiCert services will be down for approximately 10 minutes during scheduled Europe maintenance on February 3, 2024, 09:00 - 11:00 MST (16:00 - 18:00 UTC).
QuoVadis services maintenance-related downtime
During the two-hour maintenance window, some QuoVadis services will be down for approximately 10 minutes while we do infrastructure-related maintenance that requires server restarts.
Affected QuoVadis Services:
Sealsign signing service
TrustLink Switzerland instance
TrustLink Netherlands instance
ADSS signing service Netherlands instance
Certlookup
API note
APIs will return "503 services unavailable" errors.
Requests placed during this window that receive a "503 services unavailable" error message will need to be placed again after services are restored.
What can I do?
Plan accordingly:
Schedule high-priority certificate-related tasks and document signings before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
DigiCert will perform scheduled maintenance on February 3, 2024, 22:00 – 24:00 MST (February 4, 2024, 05:00 – 07:00 UTC).
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page for live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Global 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
January 30, 2024
CertCentral: Improved ACME Service
We are happy to announce that the CertCentral ACME service now supports DV certificates and domain control validation (DCV) as part of the ACME workflow, along with other changes needed to support these features.
Changes to the ACME workflow:
New ACME URLs
Existing ACME URLs will continue to work as they did before this update. However, only the new URLs will support DV TLS certificates and domain control validation.
Support for DV TLS products
You may now create ACME URLs for your DV products if available in your CertCentral account.
Previously, ACME URLs only supported Organization Validated (OV) and Extended Validation (EV) TLS products.
ACME domain control validation for all TLS products
You may now automate validation for the domains in your certificate requests using ACME. This works for all TLS products.
DV certificates are typically issued immediately upon completion of domain validation. OV and EV certificates also require organization validation to be completed before issuance.
Progressive user interface with product selection
The user interface determines if an organization is required based on your selected product.
Dynamic detection logic
Determines the action based on the previous order (if one exists). If a certificate is issued, then the next request for the same common name will automatically go into one of the following flows:
Renewal, if in the renewal window
Reissue, if not in the renewal window
Dynamic logic can be overwritten by providing a URL parameter.
No changes were made to CertCentral's managed agent-based automation with this update.
For more information, see our ACME documentation.
January 22, 2024
Update: Access to older expired certificate data postponed
On December 7, 2023, we let you know that as part of our database optimization process, expired certificate data older than 14 months would be unavailable until January 22, 2024.
This post is to let you know that access to this older expired certificate data has been delayed. As soon as access is restored, we will post another change log entry to let you know.
What if I need to view or access older expired certificate data?
If you need to access your older expired certificate data before access is restored, please contact DigiCert Support.
January 17, 2024
DigiCert user and account deactivation
Starting January 17, 2024, DigiCert may suspend users and accounts that have been inactive for 39 or more months. See the DigiCert user and account deactivation and deletion policy to learn more.
January 16, 2024
CertCentral: Updates to Sign in to your account page
We updated the DigiCert CertCentral Sign in to your account page. The next time you sign in to your account, add your username first. Then, after selecting Next, add your password and select Sign in.
Updated Sign in to your account page
Add username
Add password
January 9, 2024
CertCentral: Improvements to the code signing certificate revocation process
We are happy to announce that in CertCentral, you can now set a revocation date and time when revoking a code signing certificate due to a key compromise.
Signatures applied before the revocation date remain valid and trusted.
Signatures applied after the revocation date are invalidated and untrusted.
Previously, you had to contact DigiCert Support to set a revocation date and time when revoking a code signing certificate due to a key compromise. Now, you can do it yourself from your CertCentral account.
Java signatures
Java uses the status of the certificate, not the revocation date, to determine signature trust. Thus, all Java signatures are invalidated regardless of the certificate revocation date.
Revoking multiple certificates
When revoking all certificates on an order, DigiCert uses the date of the most recently issued certificate to establish the earliest allowed revocation date for all certificates on the order (i.e., you cannot set a revocation date before the certificate issuance date). If this issuance date does not match your key compromise date, we recommend revoking certificates individually from the Certificate history tab.
See for yourself
In your CertCentral account, in the left main menu, go to Certificates > Orders.
On the Orders page, select the code signing or EV code signing certificate order.
On the certificate's Order details page, in the Order actions dropdown, select Revoke all certificates.
On the Request to Revoke Certificate page, in the Why do you want to revoke this certificate dropdown, select Key compromise – My certificate's private key was lost, stolen, or otherwise compromised.
Under Do you know when the private key was compromised, select Yes.
In the date picker, select the day your key was compromised. In the time picker, select the time the key was compromised.
Unless you plan to revoke the certificate, select Cancel.
For more detailed instructions, see Submit a request to revoke a Code Signing/EV Code Signing certificate.
January 6, 2024
Upcoming scheduled Europe maintenance
DigiCert will perform scheduled maintenance on January 6, 2024, 09:00 – 11:00 MST (16:00 – 18:00 UTC).
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page to get live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Europe 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
Upcoming scheduled Global maintenance
DigiCert will perform scheduled maintenance on January 6, 2024, 22:00 – 24:00 MST (January 7, 2024, 05:00 – 07:00 UTC).
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page to get live maintenance updates, including email alerts for when maintenance starts and ends.
See the DigiCert Global 2024 maintenance schedule for maintenance dates and times.
Services will be restored as soon as the maintenance is completed.