Certificate profiles
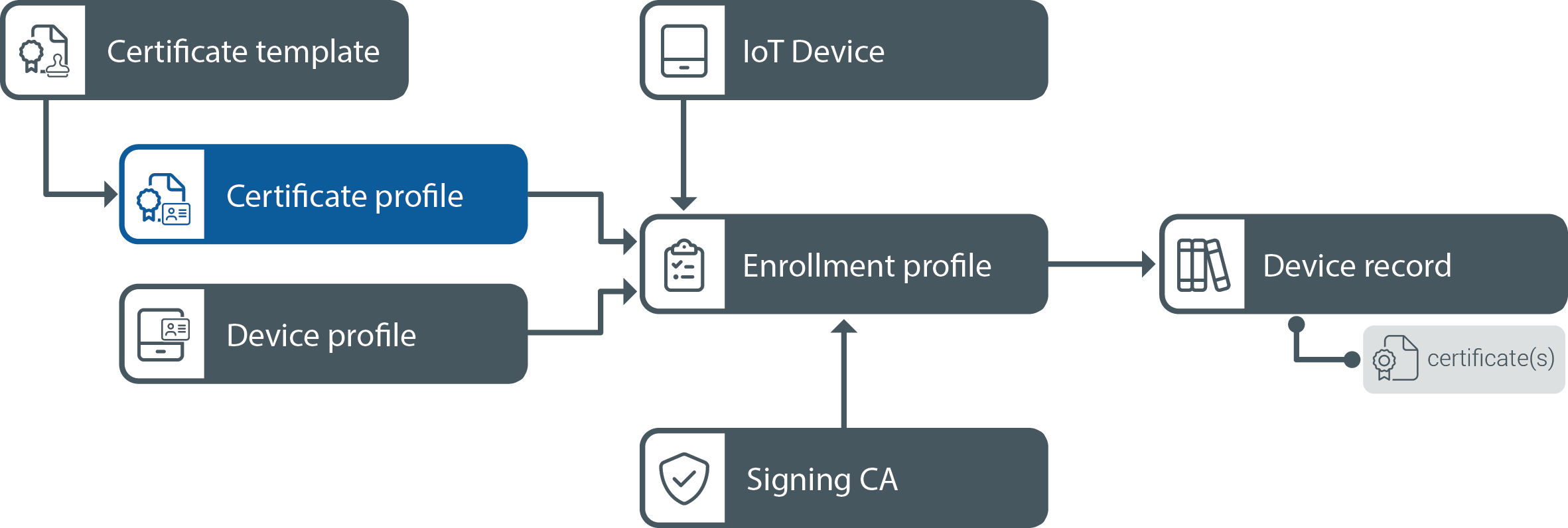
In DigiCert® IoT Trust Manager, Certificate Profiles are used to define criteria for components and their values in a certificate. It aims to create consistent certificates with a focus on security and compatibility.
To start with a certificate profile, choose a certificate template that fits your device specifications. If none of the available templates meet your needs, reach out to your account representative. For more information on creating templates, refer to Step 1: Create your certificate templates.
With a template ready, you can make adjustments to fit the requirements of your desired certificate profile. The basic structure of the template shows which details can be modified, such as:
Common name
Organization name
Organization unit
Country
State
Locality
Street Address
Postal code
Unique identifier
Email
Validity duration unit
Validity duration value
Key usage: additional usages for RSA
Key usage: additional usages for ECDSA
Key usage: critical
Extended key usage: additional usages
Extended key usage: critical
SAN extension: DNS name
Certificate policies
Key features
Content Directives The profile mandates certain fields and pinpoints their complementary values within certificates.
Effortless Configuration Sidestepping the traditionally tedious Certificate Signing Request (CSR), the Certificate Profile within IoT Trust Manager introduces a refined paradigm for certificate molding.
Consistency Commitment At its core, the Certificate Profile vouches for a homogeneous certificate product.
Attributes Emphasis It affirms the comprehensive inclusion of pivotal attributes alongside their associated values.
Rooted in Certificate Template Every Certificate Profile stands on the bedrock of a predetermined Certificate Template.
Benefits of using certificate templates
Tapping into the Certificate Profile's capabilities in IoT Trust Manager enables you to adeptly mold certificates that respect industry benchmarks. This forward-thinking strategy not only simplifies certificate generation, but also strengthens security cohesion across your device landscape.
Distinctive certificates might call for specialized "Key Usage" or "Extended Key Usage" evaluations.
A subset of certificate parameters could demand predefined default settings, effortlessly set within the Certificate Profile's confines.