Configure single sign-on with SAML
We recommend keeping two browser tabs open: one for DigiCert ONE and another for your identity provider (IdP). This setup allows you to easily reference both platforms and complete Security Assertion Markup Language (SAML) 2.0 configuration without interruptions.
Prerequisites
Before configuring SAML in DigiCert ONE:
Have administrator access to your company's IdP service, such as Microsoft Entra, Okta, Google Workspace, or other user management service.
Make sure authentication from your IdP signs the response and the assertion.
Connect DigiCert to your IdP
Use one browser to configure your DigiCert ONE account to recognize your IdP:
In the Managers () menu, select Account.
In the Account menu, go to Accounts.
On the Accounts page, select the Name of the account.
On the Account details page, navigate to the Sign in settings for all-account-access users section.
Select the pencil icon next to Single sign-on with SAML.
Copy the SSO URL.
提示
This URL is required in step 8, 9, and 10 of the Connect your IdP to DigiCert instructions.
Open another browser when you have finished step 16.
Select Upload IdP metadata.
提示
Select the metadata file that you created in with step 16 of the Connect your IdP to DigiCert instructions.
Select Save.
Create a user with the same username as the user in your IdP.
提示
If the user exists in DigiCert ONE, update their username to match their user details in your IdP.
Connect your IdP to DigiCert
注意
These instructions are based on Okta. If you’re using a different IdP, look for similar fields or refer to your IdP's documentation for guidance.
Use a second browser to configure your IdP to recognize your DigiCert ONE account:
Sign in to your IdP as an administrator.
In the left pane, select Applications.
Select Create App Integration button.
Select SAML 2.0.
Select Create.
Name the Application.
提示
Optional: Add a logo.
Select Next.
Enter URL into Okta under Single sign-on URL & Audience URI (SP Entity ID).
提示
See step 6 of the Connect DigiCert to IdP instructions.
Select Next.
Select Finish.
In the SAML Setup section, select View SAML Setup Instructions.
Copy your IdP metadata.
Enter into word processor (like Notepad)
Save as an .xml file.
Switch back to the Account Manager tab.
提示
Proceed with step 8 of the Connect DigiCert to IdP instructions.
Select Directory > People.
Select Add person or identify the user in the list.
提示
The DigiCert ONE username must match IdP username.
Select the user.
Go to Assign Application on the user details page.
Assign DigiCert ONE from application list.
提示
The user receives an activation email (Subject line: Single sign-on access for DigiCert ONE). The user needs to follow the instructions in the email to be able to sign in to DigiCert ONE via Okta.
Add single sign-on users
New users
To add new users to DigiCert ONE accounts with SSO, the assigned username in DigiCert ONE must match that of the IdP username.
注意
When Standard Sign-on is disabled, the SAML 2.0 username is active.
When Standard sign-on is enabled, the DigiCert ONE and IdP and DigiCert usernames must match.
DigiCert ONE currently doesn’t support auto-creation/registration of users via the IdP.
Existing users
Usernames: For existing DigiCert ONE users, the username is tied to the Standard Sign-on (even if standard sign-on is disabled), before enabling SSO. In the Edit user details, a new field SAML 2.0 SS0 username appears. By default, it takes the DigiCert ONE username. Modify the username here to match with the IdP, if required.
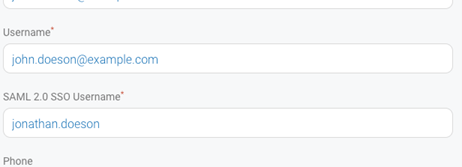
Notification: Existing user receives an email on SSO activation notifying them how to sign in.
For Azure AD from another source
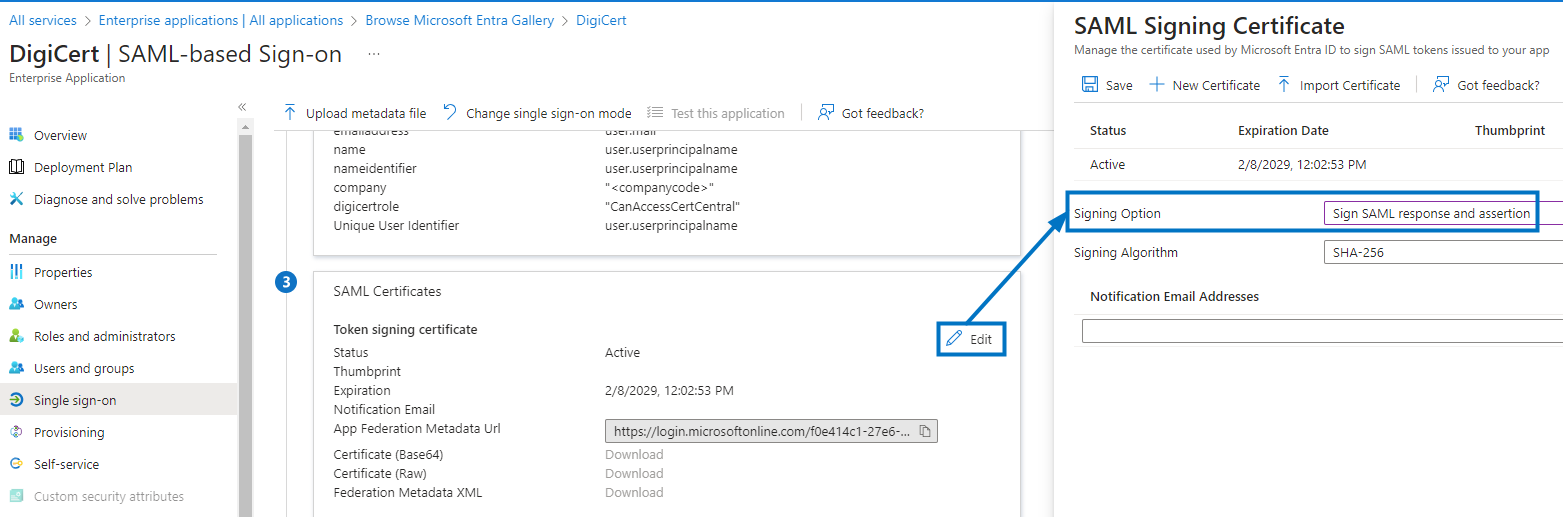
Users need to modify their SAML configuration in Azure to ensure the assertion signed. To do this:
Open the SAML configuration.
Select Edit beside SAML Signing Certificate.
Select Sign SAML assertion beside Signing Option, and select Save.
Two-factor authentication and SSO with SAML
When 2FA is enabled, DigiCert prompts you to enter an OTP when signing in, even if you have already provided an OTP to your identity provider (IdP).
What's next
After adding the DigiCert metadata to your IDP, sign in and finalize the single sign-on to DigiCert ONE connection.
DigiCert ONE sends existing users in your account the Single sign-on access to DigiCert ONE email. The email lets them know you enabled SSO for their account. To access the SSO sign-in page, they need to select Sign in to DigiCert ONE. They will use the SSO URL to sign in to their account.