SAML を使用したシングルサインオンの設定
DigiCert ONE 用と IdP(ID プロバイダ)用にブラウザタブを 2 つ開いた状態での作業を推奨します。このようにセットアップすることで、両方のプラットフォームを簡単に参照しながら、中断することなく SAML(Security Assertion Markup Language)2.0 設定を完了させることができます。
前提条件
DigiCert ONE で SAML を設定する前に、以下のことを確認してください。
会社の IdP サービス(Microsoft Entra、Okta、Google Workspace、その他のユーザー管理サービスなど)に対して、管理者アクセス権があること。
PingOne や Okta などの自社のIDPサービスにアクセスでき、使い慣れていること。
デジサートの IdP への接続
DigiCert ONE アカウントを設定し、ユーザーが既存の会社の信用情報でサインインするようにします。
[マネージャ]メニュー()で、[アカウント]を選択します。
[アカウント]メニューで、[アカウント]を選択します。
アカウントページで、アカウントの名前を選択します。
[アカウントの詳細]ページで、[すべてのアカウントにアクセスできるユーザーのサインイン設定]セクションに移動します。
[SAML でシングルサインオン]の横にある鉛筆型アイコンを選択します。
[SSO URL]の内容をコピーします。
ヒント
この URL は、「IdP のデジサートへの接続」のステップ 8、9、10 で必要になります。
ステップ 16 を実行したら、別のブラウザを開きます。
[IDP メタデータのアップロード]を選択します。
ヒント
「IdP のデジサートへの接続」のステップ 16 で作成したメタデータファイルを選択します。
準備ができたら、保存を選択します。
IdP 側のユーザーと同じユーザー名を持つユーザーを作成します。
ヒント
そのユーザーが DigiCert ONE に存在する場合、ユーザー名を IdP 側のユーザー情報と一致するように更新してください。
IdP のデジサートへの接続
注記
以下の手順では、Okta を例に説明します。他の IdP を使用している場合は、同様のフィールドを探すか、お使いの IdP が発行するドキュメントを参照してください。
2 つ目のブラウザを使用して、IdP を設定し、DigiCert ONE アカウントを認識させます。
管理者として IdP にサインインします。
左側のペインで、[Applications]を選択します。
[Create App Integration]ボタンを選択します。
SAML 2.0 を選択します。
[作成]を選択します。
アプリケーションに名前を付けます。
ヒント
オプション: ロゴを追加します。
[次へ]を選択します。
Okta の [シングルサインオン URL]と[Audience URI (SP Entity ID)] に URL を入力します。
ヒント
「デジサートの IdP への接続」のステップ 6 を参照してください。
[次へ]を選択します。
[終了]を選択します。
[SAML Setup]セクションで、[View SAML Setup Instructions]を選択します。
IdP メタデータをコピーします。
ワードプロセッサ(メモ帳など)に貼り付けます。
.xml ファイルとして保存します。
Account Manager のタブに戻ります。
ヒント
「デジサートの IdP への接続」のステップ 8 に進みます。
[Directory] > [People]を選択します。
[Add person]を選択するか、一覧からユーザーを特定します。
ヒント
DigiCert ONE のユーザ名は IdP のユーザ名と一致している必要があります。
ユーザーを選択します。
ユーザー詳細ページの[アプリケーションの割り当て]に移動します。
アプリケーションの一覧から DigiCert ONE を割り当てます。
ヒント
アクティベーションメール(件名は「DigiCert ONE へのシングルサインオンアクセス」)がユーザーに届きます。ユーザーは、メールの指示に従って操作することで、Okta 経由で DigiCert ONE にサインインできるようになります。
シングルサインオンユーザーの追加
新規ユーザー
SSO が有効になっている DigiCert ONE アカウントに新規ユーザーを追加するには、DigiCert ONE で割り当てられたユーザー名が IdP のユーザー名と一致している必要があります。
注記
標準サインオンが無効化されている場合、アクティブなのは SAML 2.0 ユーザー名です。
標準サインオンが有効な場合、DigiCert ONE と IdP ユーザー名および DigiCert ユーザー名が一致している必要があります。
DigiCert ONE 現在、IdP 経由でのユーザーの自動作成/登録はサポートされていません。
既存ユーザー
ユーザー名: 既存の DigiCert ONE ユーザーについては、SSO を有効化する前から、ユーザー名が(標準サインオンが無効になっている場合でも)標準サインオンに関連付けられています。[ユーザーの編集]の詳細に、[SAML 2.0 SSO ユーザー名]という新しいフィールドが表示されます。デフォルトで、DigiCert ONE のユーザー名が入力されています。必要な場合、ここでユーザー名を修正して IdP と一致させます。
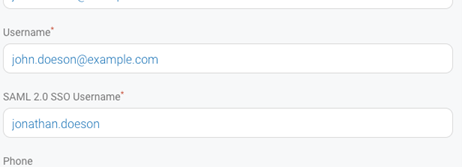
通知: SSO を有効化すると、サインイン方法を記載したメールが既存ユーザーに送られます。
別のソースからの Azure AD の場合
アサーションが確実に署名されるよう、Azure の SAML 設定を変更する必要があります。このために、以下を行います。
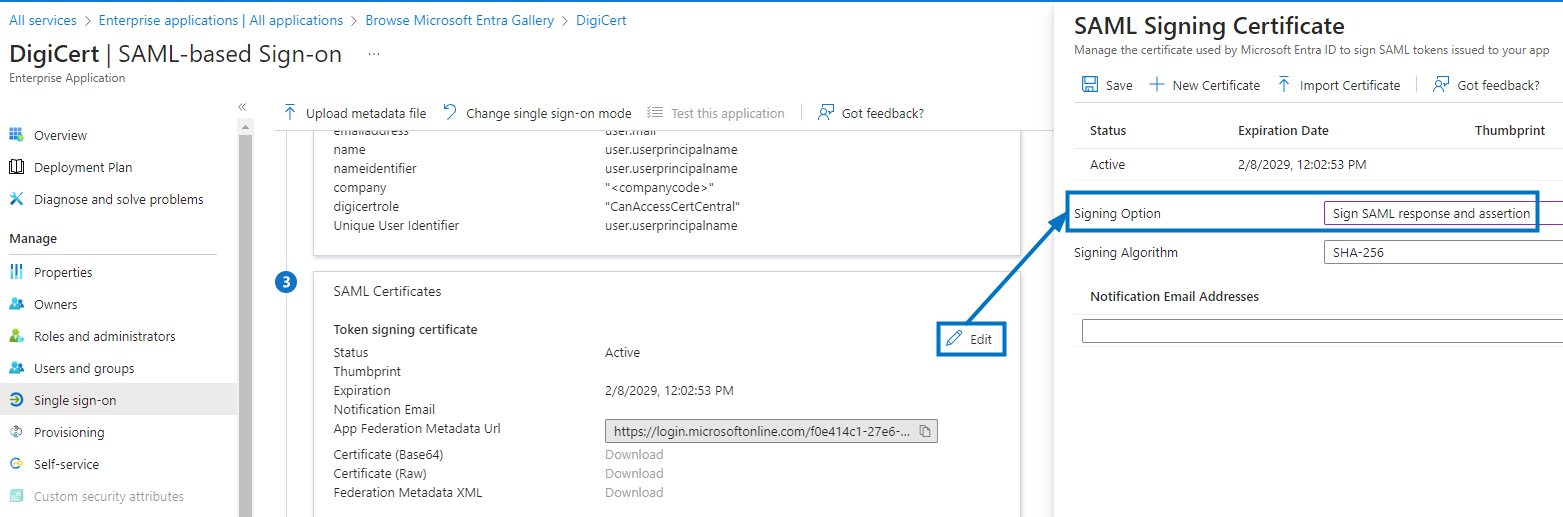
SAML 設定を開きます。
[SAML Signing Certificate]の横にある[編集]を選択します。
[サイニングオプション]の横にある[Sign SAML assertion]を選択し、[Save]を選択します。
二要素認証と SAML を使用した SSO
2FA が有効になっている場合、たとえ IdP (ID プロバイダ)に対してすでに OTP を入力していても、デジサートはサインイン時に OTP の入力を再度求めます。
次の操作
DigiCert メタデータをIDPに追加したら、サインインして、DigiCert ONE へのシングルサインオン接続を確立させます。
DigiCert ONE は、お使いのアカウントの既存ユーザーにDigiCert ONEへのシングルサインオンアクセスメールを送信します。このメールでは、自分のアカウントであなたがSSOを有効にしたことを知らせます。SSOサインインページにアクセスするには、DigiCert ONEにサインインを選択する必要があります。アカウントへのサインインには、SSO URLを使用します。