Introduction
You should have a thorough knowledge of Windows domain and network administration and an understanding of PKI components, workflows, and cryptographic systems. However, it is not necessary to have an in-depth knowledge of how cryptographic algorithms or other technical details work.
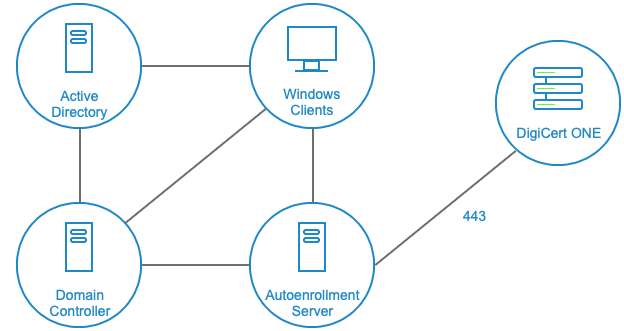
DigiCert Autoenrollment Server deployment
DigiCert Autoenrollment Server handles the following aspects of the autoenrollment process:
Requesting certificates
Managing pending requests
Renewing certificates
DigiCert Autoenrollment Server enables you to provide your network computers and end users with certificates issued by DigiCert ONE DigiCert® Trust Lifecycle Manager.
DigiCert Autoenrollment Server needs to be installed on a supported Windows server within a Windows domain. DigiCert Autoenrollment Server utilizes Active Directory (AD) services to provide information on policies, certificate templates, and end users. This is managed by the AD administrator to apply policies to specific groups of users or computers. The operating system uses the Windows autoenrollment client to automatically request certificates for authorized users or computers when they log onto the network. Windows keeps track of the certificates' validity and requests a renewal when a certificate is about to expire.
Autoenrollment process
The Windows autoenrollment client sends a certificate request to the Autoenrollment server. The server verifies the information that is contained in the request against the user's account details. Autoenrollment Server can retrieve information from Active Directory to perform further checks or to enforce restrictions regarding the certificate's content. The Autoenrollment server then submits the request to the DigiCert Certificate Authority (CA) and waits for the request to be processed.
The DigiCert CA processes the request according to the certificate profile specification, issues the certificate, and returns it to the Autoenrollment server. The Autoenrollment server then returns it to the client. If configured to do so, the Autoenrollment server also publishes the certificate to the Active Directory.
 |
The data flow of the autoenrollment process.
Renewal of certificates and private keys for autoenrollment clients
The process of renewing expiring certificates is nearly identical to the process of requesting new certificates. The only exception is that the autoenrollment client includes a reference to the certificates that must be renewed. You configure the certificate renewal period in DigiCert® Trust Lifecycle Manager. The Windows autoenrollment client automatically requests renewal of certificates when 80% of the certificate’s validity period has expired. The autoenrollment client also requests renewal when the certificate renewal period has been reached, whichever time frame is smaller.
Autoenrollment deployments
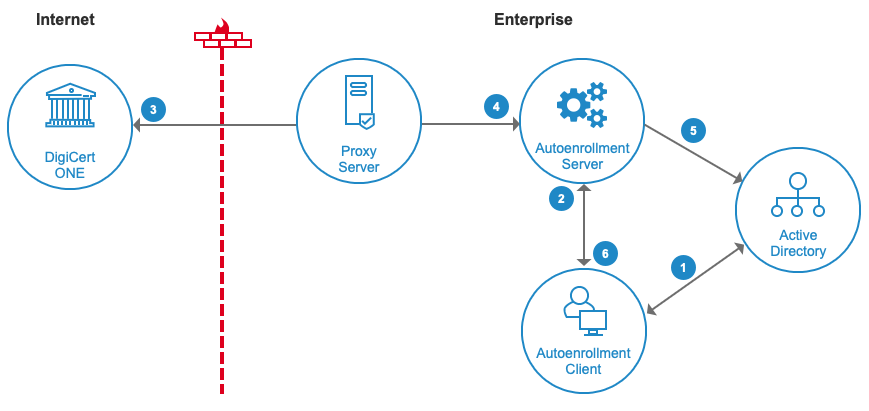 |
Autoenrollment server in a typical Enterprise deployment. Although this diagram illustrates a single-server deployment, the Autoenrollment server deployment is identical for both single and multiple server deployments.
A typical certificate enrollment flow consists of the following steps:
When an end user logs into a computer, the autoenrollment client checks the Active Directory. Or, when a certificate policy is pushed to an end user’s computer, the autoenrollment client checks the Active Directory. It then checks the local certificate store to determine the certificate template to which the end user has access for enrollment.
Based on this determination, the autoenrollment client sends a request to the Autoenrollment Server to initiate an enrollment for the appropriate certificate type.
The Autoenrollment Server sends a web service request to the DigiCert ONE CA to request the certificate. This request is authenticated via an API key (see Obtain the API token).
If the user data and certificate request are correct, the DigiCert ONE CA returns the end-user certificate to the Autoenrollment Server.
If the Autoenrollment Server is configured to do so in the certificate profile, it publishes the certificate to the Active Directory.
The Autoenrollment Server provides the certificate to the autoenrollment client for installation to the end user's certificate store.
Integration with Windows Hello for Business
Autoenrollment Server can integrate with Windows Hello® for Business, a feature in Microsoft® Windows 10 or later that allows certificate issuance through DigiCert® Trust Lifecycle Manager.
To learn more, see the Windows Hello for Business integration guide.
Integration with Citrix Federated Authentication Service (FAS)
DigiCert Autoenrollment Server can integrate with Citrix FAS to support single-sign on (SSO) for virtualized environments, using DigiCert® Trust Lifecycle Manager to monitor and manage the user authentication certificates.
To learn more, see the Citrix FAS integration guide.
Security Identifier (SID) extension and ECDSA key type support
DigiCert Autoenrollment server v 2.23.2.0 and later supports:
The Security Identifier (SID) extension with dynamic values used for Windows login, which can be Fixed value set per certificate profile or automatically read from an Active Directory attribute (ex: objectSID) using the DigiCert Autoenrollment Server.
Certificate issuance and renewal using ECDSA key type (except for Windows Hello for Business specific templates).
Custom private extensions and new Subject DN fields support
DigiCert Autoenrollment server v2.24.2.0 and later supports:
Custom private extensions that can dynamically retrieve values from Active Directory based on the certificate profile configuration.
Additional Subject Distinguished Name (DN) fields:
TitleGiven nameSurnameDN qualifier
Support for multi-valued string AD attributes and comma-separated DNS Names
Starting with Autoenrollment Server v2.25.1.0, the following enhancements are supported:
Active Directory attributes with multi-valued strings, such as the
ouattribute.DNS Names with comma-separated values, allowing multiple entries in a single field.
To configure the profiles with multiple values, see Create the autoenrollment certificate profile.