CertCentral
2022 changes
2022 年 12 月 31 日
DigiCert 2022 維護排程
若要讓規劃您的憑證相關工作變得更容易,我們預先排程我們的 2022 維護視窗。請參閱 DigiCert 2022 排程的維護 — 此頁面有最新的所有維護排程資訊。
我們在全世界都有客戶,因此理解沒有對每個人的最佳時間。但在檢閱與客戶使用有關的資料後,我們選擇了會影響我們最少客戶量的時段。
關於我們的維護時程表
除非另有說明,否則維護的時間安排在每個月的第一個周末。
每個維護視窗都排程 2 個小時。
雖然我們有保護您的服務的適當備援,但有些 DigiCert 服務仍可能無法使用。
一完成維護時,即繼續所有一般操作。
若要取得即時維護更新,請訂閱 DigiCert 狀態頁面。此訂閱包括維護開始和維護結束時使用的電郵提醒。
如果您需要更多有關這些維護時段的資訊,請聯絡您的帳戶管理員或 DigiCert 支援團隊。
December 15, 2022
CertCentral: Single random value for completing DCV on OV and EV TLS certificate orders
To simplify the domain control validation (DCV) workflow for OV and EV TLS certificates, we've improved our random value generation process for OV and EV certificate orders.
Now, when using DCV methods that require a random value to complete the domain validation for your OV or EV TLS orders, you receive a single random value that you can use to complete the DCV check for every domain on the order.
Note
Before, DigiCert returned a unique random value for each domain submitted on the OV or EV TLS certificate order.
This change brings the DCV workflow for OV and EV orders into closer alignment with DV orders, which have always returned a single random value for all domains on the order.
Affected DCV methods:
DNS TXT Record
DNS CNAME Record
HTTP Practical Demonstration (also known as File or FileAuth)
CertCentral Services API: DCV enhancements
To improve API workflows for clients using DCV methods that require a random value for OV and EV TLS certificate orders, we made the following enhancements to the CertCentral Services API.
Updated API response for creating OV and EV TLS certificate orders
We updated the data returned when you submit an order request:
New response parameter:
dcv_random_valueNow, when you submit an OV or EV TLS certificate order request with a
dcv_methodofdns-txt-token,dns-cname-token, orhttp-token, the API returns a new top-level response parameter:dcv_random_value. This parameter contains a random value that you can use to complete the DCV check for every domain on the order.Enhanced
domainsarrayNow, when you submit an OV or EV TLS certificate order request with a DCV method of
dns-txt-token,dns-cname-token, orhttp-token, the API returns adcv_tokenobject for every domain in thedomainsarray.Additionally, each
domains[].dcv_tokenobject now includes the samedcv_random_valuethat is used for the entire order. Before, we returned a different random value for each domain.Note
Before, when you submitted an order for an OV or EV TLS certificate, the API response omitted the
dcv_tokenobject for these domains:Domains validated under the scope of another domain on the order.
Domains that already existed in your account.
Subdomains of existing domains.
This example shows the updated API response for an OV TLS certificate request using a DCV method of dns_txt_token. For this example, the order includes these domains: example.com, sub.example.com, and example.org.
Updated API response for reissuing OV and EV TLS certificates
Now, when you reissue an OV or EV TLS certificate order request with a dcv_method of dns-txt-token, dns-cname-token, or http-token, the API returns a dcv_random_value that you can use to validate any domains added with the reissue request. For more information, visit the Reissue certificate API reference.
Note
Before, the Reissue certificate API endpoint only returned a dcv_random_value parameter for DV certificate reissues.
Added support for OV and EV TLS certificate orders to endpoints for managing order DCV
We updated the order-level endpoints for managing DCV to accept requests when the order_id path parameter contains the ID of an OV or EV TLS certificate order:
With this change, you can complete DCV for OV and EV TLS certificate orders with fewer API requests by calling the endpoints for managing DCV at the order-level instead of the domain-level.
Now, you can complete DCV checks for a domain using:
Any valid random value that exists for the domain (order-level or domain-level).
Either of the endpoints for checking DCV: Check domain DCV or Check order DCV.
Note
Before, the order-level endpoints for managing DCV only accepted requests when the order_id path parameter contained the ID of a DV certificate order. To manage DCV for individual domains on OV and EV TLS certificate orders, API clients had to use our domain-level endpoints:
Domain info API enhancements
We updated the Domain info API endpoint to return a new response parameter: higher_level_domains.
The higher_level_domains parameter contains a list of existing higher-level domains with a complete domain control validation (DCV) check for the same organization as the queried domain. Use this list to see if there are any domains in your account with active validations you can reuse to prove control over the queried domain.
For example, if you query the domain ID for demo.sub.example.com and you have already completed DCV checks for the domains sub.example.com and example.com in your account, the Domain info API returns a higher_level_domains array with this structure:
{
...
"higher_level_domains": [
{
"name": "sub.example.com",
"id": 4316203,
"dcv_expiration_datetime": "2023-12-04T04:08:50+00:00"
},
{
"name": "example.com",
"id": 4316205,
"dcv_expiration_datetime": "2023-12-04T04:08:49+00:00"
}
],
...
} To get the higher_level_domains array in your response data, you must submit a request to the Domain info API endpoint that includes the query string include_dcv=true:
https://www.digicert.com/services/v2/domain/{{domain_id}}?include_dcv=trueFor more information, see the API reference: Domain info.
December 8, 2022
CertCentral Services API: Added verified contact details to Organization info API
To give API clients access to more information about the verified contacts that exist for an organization, we added a new array to the Organization info API response: verified_contacts.
The new verified_contacts array provides a list of objects with details about each verified contact that exists for the organization. The verified_contacts array:
Includes information about pending, valid, and expired verified contacts.
Provides a list of validation types (CS, EV, and EV CS) for each verified contact.
Note
Before, the Organization info API only returned valid verified contacts in the ev_approvers array. The ev_approvers array is still available, however it does not provide as much detail as the new verified_contacts array.
Bugfix: Duplicate verified contacts
We fixed a bug where submitting a verified contact with multiple validation types (for example, CS and EV) caused duplicate verified contacts to be created for the organization, one for each validation type. This bug affected verified contacts submitted through the CertCentral console or through the CertCentral Services API.
Now, when you submit verified contacts with multiple validation types, we assign each validation type to the same verified contact, instead of creating a duplicate.
Note
This change only affects new verified contacts submitted after the fix. We did not remove any existing duplicate verified contacts.
Before today, duplicate verified contacts were not visible in the CertCentral console or Services API. With our recent enhancements to the Organization info API endpoint (see CertCentral Services API: Added verified contact details to Organization info API), any duplicate verified contacts for the organizations you manage will appear in the newly added verified_contacts array.
December 6, 2022
CertCentral: Removing the permanent identifier in EV Code Signing certificates
On December 6, 2022, at 10:00 MST (17:00 UTC), DigiCert will no longer issue EV Code Signing certificates with a permanent identifier value in the Subject Alternative Name field.
What do I need to do?
Does your EV code signing process expect to find the permanent identifier when parsing your issued EV Code Signing certificates?
If yes, you need to update your process by December 6, 2022, so it no longer relies on a permanent identifier value.
If no, no action is required.
Does this change affect my existing EV Code Signing certificates?
This change does not affect existing EV Code Signing certificates with a permanent identifier value in the Subject Alternative Name field. However, if you reissue an EV Code Signing certificate after the change on December 6, 2022, your reissued certificate will not contain a permanent identifier.
Background
The permanent identifier is a unique code for EV code signing certificates that includes information about the certificate subject’s jurisdiction of incorporation and registration information. In 2016, the CA/Browser Forum removed the permanent identifier requirement from EV Code Signing certificates.
CertCentral Services API: Verified contact improvements
Starting December 6, 2022, DigiCert will require organizations on Code Signing (CS) and EV Code Signing (EV CS) certificate orders to have a verified contact.
This change was originally scheduled for October 19, 2022. However, we postponed the change to December 6, 2022. For more information, see the October 19, 2022 change log entry.
Learn more:
December 3, 2022
Upcoming scheduled maintenance
DigiCert will perform scheduled maintenance on December 3, 2022, 22:00 – 24:00 MST (December 4, 2022, 05:00 – 07:00 UTC).
Note
Maintenance will be one hour later for those who do not observe daylight savings.
Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window, including Automation events and Discovery scans.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
Subscribe to the DigiCert Status page to get live maintenance updates. This subscription includes email alerts for when maintenance begins and when it ends.
See DigiCert 2022 scheduled maintenance for scheduled maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
November 5, 2022
Upcoming Scheduled Maintenance
DigiCert will perform scheduled maintenance on November 5, 2022, 22:00 –24:00 MDT (November 6, 2022, 04:00 – 06:00 UTC). Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
November 3, 2022
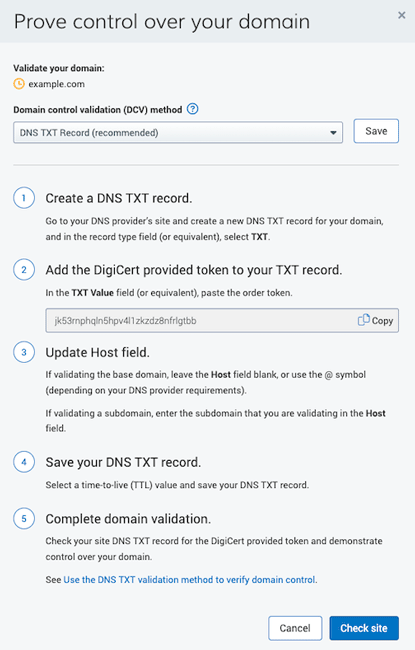
CertCentral: Improved DV certificate domain control validation
We updated the Prove control over your domain popup window for pending DV orders, making it easier to see what you need to do to complete the domain validation for all domains included on your certificate.
Now, when you select a domain control validation (DCV) method, you can see basic instructions for completing the domain validation along with a link to more detailed instructions on our product documentation website.
Note
For DV orders, you must use the same DCV method for all the domains on the certificate.
See for yourself
In the left main menu, go to Certificates > Orders.
On the Orders page, locate and select the order number of a pending DV order.
On the DV order details page, under What do I need to do, select the Prove control over domain link.
Improved Prove control over your domain popup window
November 1, 2022
CertCentral: upgrade your product when renewing your order
DigiCert is happy to announce that CertCentral allows you to upgrade your product when renewing your order.
Are you tired of placing a new order and reentering all your information when upgrading to a new product?
Now you don’t have to. We’ve improved our order renewal process so you can upgrade your product when renewing your certificate order.
Don’t see that option to upgrade your product when renewing your order, or already have the products you need and don’t want to see the option to upgrade?
Don’t worry; you can enable and disable this feature as needed. When ready to upgrade, you can enable it to save the hassle of placing a new order. When done, you can disable it until the next time you want to upgrade a product. See Upgrade product on renewal settings.
CertCentral: Improved Code Signing and EV Code Signing request forms
DigiCert is happy to announce that we updated the Code Signing and EV Code Signing request forms making it easier to view and add organization-related information when ordering a certificate.
This update allows you to select an organization and review the contacts associated with that organization or enter a new organization and assign contacts to the new organization.
Changes to note
You can now add a new organization along with all its contacts: organization, technical, and verified.
When adding an existing organization, you can now:
View the contacts assigned to that organization
Replace the organization contact
Replace or remove the technical contact
Select the verified contact(s) you want to receive the approval email
Add verified contacts
Before, you could only see and select an existing organization and could not see the contacts assigned to the organization.
See for yourself
In your CertCentral account, in the left main menu, go to Request a Certificate > Code Signing or Request a Certificate > EV Code Signing to see the updates to the request forms.
CertCentral: Code Signing certificate reissue bug fix
When reissuing your code signing certificate, we now include the Subject Email Address on your reissued certificate. Adding a subject email is optional and only available in enterprise accounts.
Note that we will not include the subject email address in the reissued certificate if the domain validation on that email domain has expired.
Background
When you order a code signing certificate, you can include an email address on your code signing certificate—subject email. Including an email address on the certificate provides an additional layer of trust for end users when checking your code signing signature.
See 訂購 Code Signing 憑證.
October 21, 2022
CertCentral: Ability to require an additional email on certificate request forms
We are happy to announce that you can now make the Additional emails field a required field on CertCentral, Guest URL, and Guest Access request forms.
Tired of missing important expiring certificate notifications because the certificate owner is on vacation or no longer works for your organization?
The change helps prevent you from missing important notifications, including order renewal and expiring certificate notifications when the certificate owner is unavailable.
See for yourself:
To change this setting for CertCentral request forms:
In the left menu, go to Settings > Preferences.
On the Preferences page, expand Advanced settings.
In the Certificate Requests section, under Additional email field, select Required so requestors must add at least one additional email to their requests.
Select Save Settings.
To change this setting for Guest Access:
In the left main menu, go to Account > Guest Access.
On the Guest access page, in the Guest access section, under Additional emails, select Required so requestors must add at least one additional email to their requests.
Select Save Settings.
To change this setting for Guest URLs:
In the left main menu, go to Account > Guest Access.
On the Guest access page, in the Guest URLs section, to make it required in an existing guest URL, select the name of the guest URL. Under Emails, check Require additional emails field so requestors must add at least one additional email to their requests.
To make it required on a new guest URL, select Add Guest URL and then under Emails, check Require additional emails field so requestors must add at least one additional email to their requests.
Select Save Settings.
October 20, 2022
Change log RSS feed is going down
On October 20, 2022, the RSS feed for the docs.digicert.com change log is going down due to a platform migration.
It will return. Check back here for updates or contact us at docs@digicert.com to be notified when the new RSS feed is available.
October 19, 2022
CertCentral Services API: Verified contact improvements
Note
Update: This API change has been postponed until December 6, 2022.
DigiCert continues to recommend you follow our guidance to update affected API implementations before December 6.
What if I already made changes to get ready for October 19?
You are prepared for December 6. You don’t need to make additional changes. DigiCert will continue processing your order requests for Code Signing (CS) and EV Code Signing (EV CS) certificates as usual now and after we update the API on December 6.
Starting October 19, 2022, DigiCert will require organizations on Code Signing (CS) and EV Code Signing (EV CS) certificate orders to have a verified contact.
DigiCert has always required a verified contact from the organization to approve code signing certificate orders before we issue the certificate. Today, DigiCert can add a verified contact to an organization during the validation process. After October 19, verified contacts must be submitted with the organization.
To make the transition easier, when you submit a request to the Order code signing certificate API endpoint, DigiCert will default to adding the authenticated user (the user who owns the API key in the request) as a verified contact for the organization.
DigiCert will apply this default when:
The organization in the API request has no verified contacts who can approve CS or EV CS orders.
The API request body does not specify a new verified contact to add to the organization.
The authenticated user has a job title and phone number.
To avoid a lapse in service, make sure users in your CertCentral account with active API keys have a job title and phone number.
Learn more
October 17, 2022
CertCentral: Updated the DigiCert site seal image
We are happy to announce that we updated the DigiCert site seal image and replaced the checkmark with a padlock.

The updated site seal continues to provide your customers with the assurance that your website is secured by DigiCert—the leading provider of digital trust.
October 13, 2022
CertCentral: Updated the Code Signing and EV Code Signing request forms
In CertCentral, we reorganized and updated the look of the Code Signing and EV Code Signing certificate request forms. These forms are now more consistent with the look and flow of our TLS/SSL certificate request forms.
CertCentral: Code Signing certificate request form bug fix
On the code signing request form, when adding a Subject email address to appear on the certificate, you can now see the validated domains assigned to the organization with which the code signing certificate is associated.
Note
Previously, the option for viewing the validated domains assigned to the organization did not show any domains.
October 10, 2022
New Dedicated IP addresses for DigiCert Services
Update: IP Address change postponed until February 15, 2023
When we sent notifications in June 2022 about the IP address change, one of the IP addresses was incorrect. The same IP address was incorrect in this change log. We fixed that, and the information in the change log has been corrected.
To provide you with time to verify and update the IP addresses in your allowlist, we have postponed the IP address change until February 2023.
For more information:
New Dedicated IP Addresses knowledge base
October 8, 2022
Upcoming Scheduled Maintenance
DigiCert will perform scheduled maintenance on October 8, 2022, 22:00 –24:00 MDT (October 9, 2022, 04:00 – 06:00 UTC). Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance begins and when it ends.
See DigiCert 2022 scheduled maintenance for scheduled maintenance dates and times.
Services will be restored as soon as the maintenance is completed.
End of support for CBC ciphers in TLS connections
DigiCert will end support for Cipher-Block-Chaining (CBC) ciphers in TLS connections to our services on October 8, 2022, at 22:00 MDT (October 9, 2022, at 04:00 UTC).
This change affects browser-dependent services and applications relying on CBC ciphers that interact with these DigiCert services:
CertCentral and CertCentral Services API
Certificate Issuing Services (CIS)
CertCentral Simple Certificate Enrollment Protocol (SCEP)
This change does not affect your DigiCert-brand certificates. Your certificates will continue to work as they always have.
Why is DigiCert ending support for the CBC ciphers?
To align with Payment card industry (PCI) compliance standards, DigiCert must end support for the following CBC:
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
TLS_RSA_WITH_AES_256_CBC_SHA
What do I need to do?
If you are using a modern browser, no action is required. Most browsers support strong ciphers, such as Galois/Counter Mode (GCM) ciphers, including Mozilla Firefox, Google Chrome, Safari, and Microsoft Edge. We do recommend updating your browser to its most current version.
If you have applications or API integrations affected by this change, enable stronger ciphers, such as GCM ciphers, in those applications and update API integrations before October 8, 2022.
If you do not update API integrations and applications, they will not be able to use HTTPS to communicate with CertCentral, the CertCentral Services API, CIS, and SCEP.
Knowledge base article
See our Ending Support for CBC Ciphers in TLS connections to our services for more information.
Contact us
If you have questions or need help, contact your account manager or DigiCert Support.
September 27, 2022
CertCentral Services API: Keep the "www" subdomain label when adding a domain to your account
To give you more control over your domain prevalidation workflows, we added a new optional request parameter to the Add domain API endpoint: keep_www. Use this parameter to keep the www. subdomain label when you add a domain using a domain control validation (DCV) method of email, dns-txt-token, or dns-cname-token.
By default, if you are not using file-based DCV, the Add domain endpoint always removes the www. subdomain label from the name value. For example, if you send www.example.com, DigiCert adds example.com to your account and submits it for validation.
To keep the www and limit the scope of the approval to the www subdomain, set the value of the keep_www request parameter to true:
{
"name": "www.example.com",
"organization": {
"id": 12345
},
"validations": [
{
"type": "ov"
}
],
"dcv_method": "email",
"keep_www": true
}September 16, 2022
CertCentral: Revocation reasons for revoking certificates
CertCentral supports including a revocation reason when revoking a certificate. Now, you can choose one of the revocation reasons listed below when revoking all certificates on an order or when revoking an individual certificate by ID or serial number.
Supported revocation reasons:
Key compromise* - My certificate's private key was lost, stolen, or otherwise compromised.
Cessation of operation - I no longer use or control the domain or email address associated with the certificate or no longer use the certificate.
Affiliation change - The name or any other information regarding my organization changed.
Superseded - I have requested a new certificate to replace this one.
Unspecified - None of the reasons above apply.
*Note: Selecting Key compromise does not block using the associated public key in future certificate requests. To add the public key to the blocklist and revoke all certificates with the same key, visit problemreport.digicert.com and prove possession of the key.
Revoke immediately
We also added the Revoke this certificate immediately option that allows Administrators to skip the Request and Approval process and revoke the certificate immediately. When this option is deselected, the revocation request appears on the Requests page, where an Administrator must review and approve it before it is revoked.
Background
The Mozilla root policy requires Certificate Authorities (CAs) to include a process for specifying a revocation reason when revoking TLS/SSL certificates. The reason appears in the Certificate Revocation List (CRL). The CRL is a list of revoked digital certificates. Only the issuing CA can revoke the certificate and add it to the CRL.
September 10, 2022
Upcoming Scheduled Maintenance
DigiCert will perform scheduled maintenance on September 10, 2022, 22:00 –24:00 MDT (September 11, 2022, 04:00 – 06:00 UTC). Although we have redundancies to protect your services, some DigiCert services may be unavailable during this time.
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance begins and when it ends.
See DigiCert 2022 scheduled maintenance for scheduled maintenance dates and times.
September 7, 2022
CertCentral Services API: Revocation reason for TLS/SSL certificates
In the CertCentral Services API, we added the option to choose a revocation reason when you submit a request to revoke a TLS/SSL certificate.
You can choose a revocation reason when revoking all certificates on an order or when revoking an individual certificate by ID or serial number.
To choose a revocation reason, include the optional revocation_reason parameter in the body of your request.
Example JSON request body:
{
"revocation_reason": "superseded"
}
For information about each revocation reason, visit the API documentation:
Revoke certificate (by ID or serial number)
August 30, 2022
CertCentral Services API: Added label for verified contacts
In the CertCentral Services API, we added a new contact_type label for verified contacts: verified_contact.
Use the verified_contact label to identify verified contacts for an organization when you submit a request for an EV TLS, Verified Mark, Code Signing, or EV Code Signing certificate. The updated label applies to all verified contacts, regardless of which product type the order is for.
For example, this JSON payload shows how to use the verified_contact label to add a verified contact to an organization in a new certificate order request:
{
"certificate": {
...
}
"organization": {
"id": 12345,
"contacts": [
{
"contact_type": "verified_contact",
"user_id": 12345
}
},
...
} Note: Before this change, verified contacts were always identified with the label ev_approver. The CertCentral Services API will continue accepting ev_approver as a valid label for verified contacts on EV TLS, VMC, Code Signing, and EV Code Signing certificate orders. The verified_contact label works the same as the ev_approver label, but the name is updated to apply to all products that require a verified contact.
Improved API documentation for adding organizations to Code Signing and EV Code Signing orders
We updated the Order code signing certificate API documentation to describe three ways to add an organization to your Code Signing (CS) or EV Code Signing (EV CS) order requests:
Add an existing organization already validated for CS or EV CS certificate issuance.
Add an existing organization not validated for CS or EV CS and submit the organization for validation with your order.
Create a new organization and submit it for validation with your CS or EV CS order request.
Learn more: Order code signing certificate – CS and EV CS organization validation
August 24, 2022
CertCentral: Edit SANs on pending orders: new, renewals, and reissues
DigiCert is happy to announce that CertCentral allows you to modify the common name and subject alternative names (SANs) on pending orders: new, renewals, and reissues.
Tired of canceling an order and placing it again because a domain has a typo? Now, you can modify the common name/SANs directly from a pending order.
Items to note when modifying SANs
Only admins and managers can edit SANs on pending orders.
Editing domains does not change the cost of the order.
You can only replace a wildcard domain with another wildcard domain and a fully qualified domain name (FQDN) with another FQDN.
The total number of domains cannot exceed the number included in the original request.
Removed SANs can be added back for free, up to the amount purchased, any time after DigiCert issues your certificate.
To reduce the certificate cost, you must cancel the pending order. Then submit a new request without the SANs you no longer want the certificate to secure.
See for yourself
In your CertCentral account, in the left main menu, go to Certificates > Orders.
On the Orders page, select the pending order with the SANs you need to modify.
On the certificate’s Order details page, in the Certificate status section, under What do you need to do, next to Prove control over domains, select the edit icon (pencil).
See Edit common name and SANs on a pending TLS/SSL order: new, renewals, and reissues.
CertCentral Services API: Edit SANs on a pending order and reissue
To allow you to modify SANs on pending new orders, pending renewed orders, and pending reissues in your API integrations, we added a new endpoint to the CertCentral Services API. To learn how to use the new endpoint, visit Edit domains on a pending order or reissue.
August 22, 2022
CertCentral Services API: New response parameters for Domain info and List domains endpoints
To make it easier for API clients to get the exact date and time domain validation reuse periods expire, we added new response parameters to the Domain info and List domains API endpoints:
dcv_approval_datetime: Completion date and time (UTC) of the most recent DCV check for the domain.dcv_expiration_datetime: Expiration date and time (UTC) of the most recent DCV check for the domain.
Tip
For domain validation expiration dates, use the new dcv_expiration_datetime response parameter instead of relying on the dcv_expiration.ov and dcv_expiration.ev fields. Since October 1, 2021, the domain validation reuse period is the same for both OV and EV TLS/SSL certificate issuance. The new dcv_expiration_datetime response parameter returns the expiration date for both OV and EV domain validation.
Learn more:
August 6, 2022
Upcoming scheduled maintenance
Some DigiCert services will be down for about 15 minutes during scheduled maintenance on August 6, 2022, 22:00 – 24:00 MDT (August 7, 2022, 04:00 – 06:00 UTC).
What can I do?
Plan accordingly:
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance starts and when maintenance ends.
For scheduled maintenance dates and times, see DigiCert 2022 scheduled maintenance.
July 11, 2022
CertCentral Services API: Archive and restore certificates
To give API clients the option to hide unused certificates from API response data, we released new API endpoints to archive and restore certificates. By default, archived certificates do not appear in response data when you submit a request to the List reissues or List duplicates API endpoints.
New API endpoints
Use this endpoint to archive a certificate.
Use this endpoint to restore an archived certificate.
Updated API endpoints
We updated the List reissues and List duplicates endpoints to support a new optional URL query parameter: show_archived. If the value of show_archived is true, the response data includes archived certificates. If false (default), the response omits archived certificates.
July 9, 2022
Upcoming Schedule Maintenance
Some DigiCert services will be down for a total of 20 minutes during scheduled maintenance on July 9, 2022, 22:00 – 24:00 MDT (July 10, 2022, 04:00 – 06:00 UTC).
What can I do?
Plan accordingly
Schedule high-priority orders, renewals, and reissues before or after the maintenance window.
Expect interruptions if you use the APIs for immediate certificate issuance and automated tasks.
To get live maintenance updates, subscribe to the DigiCert Status page. This subscription includes email alerts for when maintenance begins and when it ends.
For scheduled maintenance dates and times, see the DigiCert 2022 scheduled maintenance.
July 5, 2022
CertCentral: Improved Order details page
DigiCert is happy to announce that we improved the layout and design of the Order details page.
We took your feedback and updated the Orders page to make managing your certificates and orders easier throughout their lifecycle.
When we reorganized the information on the Order details page, we didn’t remove anything. So, everything you did before the updates, you can still do now. However, there are a few things you asked for that you can do now that you couldn’t do before.
Summary of changes:
We added new banners, alerts, and icons to help you better understand the actions you need to take on your certificates and orders.
We added a Certificate history tab to the Order details page. Now, you can view and interact with all the certificates associated with the order: reissues, duplicates, expired, and revoked.
We added the ability to revoke an individual certificate or all the certificates on the order.
We also updated the Orders page to add Certificate and Order alert banners, advanced search features, and columns in the orders list.
These changes do not affect Guest access. When accessing an order via guest access, you will not see any of the updates.
See the changes for yourself. In your CertCentral account, in the left main menu, go to Certificates > Orders.
Want to provide feedback?
The next time you are in your CertCentral account, locate the “d” icon in the lower right corner of the page (white “d” in a blue circle) and click it. Use the Share Your Feedback feature to let us know your thoughts on the changes. And don’t hesitate to provide feedback about other CertCentral pages and functionality.
June 28, 2022
CertCentral: Improved DNS Certification Authority Authorization (CAA) resource records checking
DigiCert is happy to announce that we improved the CAA resource record checking feature and error messaging for failed checks in CertCentral.
Now, on the order’s details page, if a CAA resource record check fails, we display the check’s status and include improved error messaging to make it easier to troubleshoot problems.
Background
Before issuing an SSL/TLS certificate for your domain, a Certificate Authority (CA) must check the DNS CAA Resource Records (RR) to determine whether they can issue a certificate for your domain. A Certificate Authority can issue a certificate for your domain if one of the following conditions is met:
They do not find a CAA RR for your domain.
They find a CAA RR for your domain that authorizes them to issue a certificate for the domain.
How can DNS CAA Resource Records help me?
CAA resource records allow domain owners to control which certificate authorities (CAs) are allowed to issue public TLS certificates for each domain.
June 21, 2022
CertCentral: Bulk domain validation support for DNS TXT and DNS CNAME DCV methods
DigiCert is happy to announce that CertCentral bulk domain validation now supports two more domain control validation (DCV) methods: DNS TXT and DNS CNAME.
Remember, domain validation is only valid for 397 days. To maintain seamless certificate issuance, DigiCert recommends completing DCV before the domain's validation expires.
Don't spend extra time submitting one domain at a time for revalidation. Use our bulk domain revalidation feature to submit 2 to 25 domains at a time for revalidation.
See for yourself
In your CertCentral account, in the left main menu, go to Certificates > Domains.
On the Domains page, select the domains you want to submit for revalidation.
In the Submit domains for revalidation dropdown, select the DCV method you want to use to validate the selected domains.
2022 年 6 月 6 日
CertCentral Report Library API 增強
DigiCert 很榮幸宣佈以下的 CertCentral Report Library API 增強:
刪除排程的報告以中止報告的執行
我們新增了新端點:刪除排程的報告。刪除排程的報告會中止將來的報告執行。刪除排程的報告後,完成的報告以保持適用於下載的相同報告 ID 執行。
Note
之前,您只可以編輯報告的排程,或刪除排程的報告和所有完成的報告執行。
產生只有子帳戶資料的報告
關於建立報告和編輯報告端點,我們新增了新選項到允許的 division_filter_type 值的清單中:EXCLUDE_ALL_DIVISIONS。使用此值從報告中排除所有父項帳戶資料。使用此選項的報告僅納入來自所選擇的子帳戶的資料 (sub_account_filter_type)。
Note
之前,若未在父項帳戶中納入來自一個或多個分部的資料即無法產生子帳戶報告。
深入了解
2022 年 6 月 4 日
即將到來的排程維護
DigiCert 將在 2022 年 6 月 4 日北美山區夏令時間 22:00 到 -24:00 (2022 年 6 月 5 日世界協調時間 04:00 到 06:00) 執行排程的維護。雖然我們有保護您的服務的適當備援,但有些 DigiCert 服務在這段時間內仍可能無法使用。
我可以做什麼?
在維護時段前後安排高優先順序訂單、續訂和重新發行的時間。
預期在您使用 API 進行立刻發行憑證和自動化工作時中斷。
若要取得即時維護更新,請訂閱 DigiCert 狀態頁面。此訂閱包括維護開始和維護結束時使用的電郵提醒。
請參閱 DigiCert 2022 排程的維護的排程的維護日期和時間。
服務將在維護完成時盡快還原。
2022 年 5 月 31 日
CertCentral Services API:改進的訂單資訊 API 回應
更新:為了提供更多時間給 API 消費者評估他們的整合上的訂單資訊 API 回應的影響,我們將此更新延期到 2022 年 5 月 31 日。我們原本計畫在 2022 年 4 月 25 日釋出以下所述的變更。
2022 年 5 月 31 日,DigiCert 將對 Order info API 做出以下的改進。這些變更移除了未使用的值與,並將訂單詳細資料物件的資料結果更新為與不同產品類別的不同狀態中的訂單更一致。
如需更多有關公用 TLS、代碼簽署、文件簽署和第 1 類 S/MIME 憑證的資訊與回應範例,請參閱訂單資訊端點的參考文件。
如果您有疑問或需要這些變更的協助,請聯絡您的客服代表或 DigiCert 支援團隊。
一般增強
以下的變更適用於與訂單狀態無關的多種憑證類型的訂單。
移除的參數:
public_id(字串)對於所有訂單,API 將停止傳回
public_id參數。DigiCert 不再支援需要public_id值的快速安裝工作流程。certificate.ca_cert_id(字串)對於 DV 憑證訂單,API 將開始傳回
ca_cert_id參數。此參數的值是一個用於發行 ICA 憑證的內部 ID,而且無法在外部使用。API 已從其他產品類型的訂單詳細資料排除ca_cert_id參數。若要取得與發行訂單關聯的 ICA 憑證的名稱和公用 ID,請改用
ca_cert物件。verified_contacts(物件的陣列)對於未核准的憑證訂單,API 將停止傳回
verified_contacts參數。API 已從其他產品類型的訂單詳細資料中排除verified_contacts陣列。certificate.dns_names(字串的陣列)如果沒有和訂單關聯的 DNS 名稱 (例如,如果訂單是用於代碼簽署、文件簽署和第 1 類 S/MIME 憑證),API 將停止傳回
dns_names陣列。之前,API 傳回有空字串的
dns_names陣列:[" "]certificate.organization_units(字串的陣列)如果沒有與訂單關聯的組織單位,API 將停止傳回
organization_units陣列。之前,為了某些產品類型,API 傳回有空字串的
organization_units陣列:[" "]certificate.cert_validity在
cert_validity物件中,API 僅傳回在建立訂單時,使用於設定憑證有效期間的單位的金鑰/值組合。例如,如果憑證的有效期間是 1 年,cert_validity物件將傳回有值 1 的years參數。之前,
cert_validity物件有時會傳回用於days和years的值。
新增的參數:
order_validity(物件)關於代碼簽署、文件簽署和用戶端憑證訂單,API 將開始傳回
order_validity物件。order_validity物件傳回訂單有效期間的days、years或custom_expiration_date。API 已在公用 SSL/TLS 產品的訂單詳細資料中納入order_validity物件。payment_profile(物件)關於 DV 憑證訂單,如果訂單與儲存的信用卡關聯,API 將開始傳回
payment_profile物件。API 已在其他產品類型的訂單詳細資料中納入payment_profile物件。server_licenses(整數)關於 DV 憑證訂單,API 將開始傳回
server_licenses參數。API 已在其他產品類型的訂單詳細資料中納入server_licenses參數。
未核准的訂單要求
以下的變更僅適用於擱置的核准或已遭到拒絕的憑證訂單要求。在核准要求和提交訂單給 DigiCert 進行驗證和發行後,這些變更使回應的資料結構更接近 API 傳回的內容。
若要管理未核准和遭到拒絕的要求,建議使用要求端點 (/request) 取代擷取訂單詳細資料。我們設計 /request 端點來管理擱置的與遭到拒絕的憑證訂單要求,而且這些端點保持不變。
Note
為了更快發行憑證,我們建議使用跳過或省略新憑證訂單的要求核准步驟的工作流程。如果您的 API 工作流程已跳過或省略核准步驟,您可以安全的忽略以下的變化。瞭解更多有關移除核准步驟的資訊:
新增的參數:
disable_ct(布林)allow_duplicates(布林)cs_provisioning_method(字串)
移除的參數:
server_licenses(整數)關於未核准的訂購要求,API 將停止傳回
server_licenses參數。API 將繼續在核准的訂單要求的訂單詳細資料中加入server_licenses參數。
改進的 organization 物件
若要在未核准與核准的訂單要求的訂單詳細資料中提供一致的資料結果,API 將在未核准的訂單要求上傳回修改的 organization 物件。
API 將停止傳回所有憑證類型的未核准訂單要求上的以下預期的屬性:
organization.status(字串)organization.is_hidden(布林)organization.organization_contact(物件)organization.technical_contact(物件)organization.contacts(物件的陣列)
如果存在所有產品類型的未核准訂單要求,API 將開始傳回以下預期的屬性:
organization.name(字串)organization.display_name(字串)organization.assumed_name(字串)organization.city(字串)organization.country(字串)
若要取得未納入訂單資訊回應中的組織詳細資料,請使用組織資訊 API端點。
2022 年 5 月 24 日
從新的中繼 CA 憑證發行 GeoTrust 和 RapidSSL DV 憑證的 CertCentral
2022 年 5 月 24 日 9:00 am 和 11:00 am MDT (3:00 pm 和 5:00 pm UTC) 之間,DigiCert 將取代以下所列的 GeoTrust 和 RapidSSL 中繼 CA (ICA) 憑證。我們不再發行來自這些中繼授權單位的最長有效期 (397 天) DV 憑證。
GeoTrust TLS DV RSA Mixed SHA256 2020 CA-1
GeoTrust TLS DV RSA Mixed SHA256 2021 CA-1
RapidSSL TLS DV RSA Mixed SHA256 2020 CA-1
RapidSSL TLS DV RSA Mixed SHA256 2021 CA-1
GeoTrust Global TLS RSA4096 SHA256 2022 CA1
RapidSSL Global TLS RSA4096 SHA256 2022 CA1
請參閱 DigiCert ICA 更新知識庫文章。
這如何影響我?
推出新的 ICA 憑證不會影響現有的 DV 憑證。自取代的 ICA 憑證發行的啟用憑證直到到期時仍保持信任。
但將發行來自 ICA 憑證的所有新憑證,包括重新發行憑證。為了確保忽略取代 ICA 憑證,請務必加入所提供的 ICA 憑證和您安裝的每一份 TLS 憑證。
固定舊版的中繼 CA 憑證
將接受舊版中繼 CA 憑證的寫入硬碼中
經營包括舊版中繼 CA 憑證的信任商店
需要的行動
如果進行固定、接受硬碼或操作信任存放區,請盡快更新您的環境。您應停止固定和將 ICA 憑證編成硬碼,或做必要的變更以確保自新的 ICA 憑證發行的 GeoTrust DV 和 RapidSSL DV 憑證受到信任。換言之,請確定它們可以鏈結到它們的新 ICA 憑證和信任的根。
請參閱 DigiCert 信任的根權限憑證頁面以下載新的中繼 CA 憑證的副本。
若我需要更多時間,我該怎麼辦?
如果您需要更多時間更新環境,您可以繼續使用舊的 2020 ICA 憑證,直到到期為止。請聯絡 DigiCert 支援團隊,他們可以設定您的帳戶。但在 2022 年 5 月 31 日後,從 2020 ICA 憑證發行的 RapidSSL DV 和 GeoTrust DV 憑證將修改為不到一年。
2022 年 5 月 18 日
CertCentral:DigiCert KeyGen,我們的新金鑰產生服務
DigiCert 很榮幸發佈我們的新金鑰產生服務 - KeyGen。使用 KeyGen 從您的瀏覽器產生和安裝您的用戶端和代碼簽署憑證。KeyGen 可以使用在 macOS 和 Windows 上,而且所有主要瀏覽器都支援。
使用 KeyGen 不需要產生 CSR 即可訂購您的用戶端和代碼簽署憑證。不使用 CSR 下訂單。在我們處理訂單和您的憑證就緒後, DigiCert 傳送附有關於使用 KeyGen 的指示的 "Generate your Certificate" (產生您的憑證) 電郵以取得您的憑證。
KeyGen 如何運作?
KeyGen 產生金鑰組,然後使用公用金鑰建立憑證簽署要求 (CSR)。KeyGen 將 CSR 傳送到 DigiCert,然後 DigiCert 將憑證傳回給 KeyGen。接著 KeyGen 下載包含憑證和私密金鑰的 PKCS12 (.p12) 檔案到您的桌面上。您在憑證產生程序期間建立的密碼可以保護 PKCS12 檔案。當您使用密碼開啟憑證檔案時,憑證安裝在您的個人憑證存放區中。
若要瞭解更多與從您的瀏覽器產生用戶端和代碼簽署憑證的資訊,請參閱以下的指示:
2022 年 5 月 9 日
CertCentral Services API:修復的資料類型,用於訂單資訊 API 回應中的空白使用者值
我們修復了在沒有使用者與訂單關聯時,訂單資訊 API (GET https://www.digicert.com/services/v2/order/certificate/{{order_id}}) 傳回 user 欄位的錯誤資料類型的問題。現在,對於沒有使用者資料的訂單,訂單資訊端點傳回空白的 user 物件 ("user": {} ),而非傳回空白的陣列 ("user": [])。
2022 年 5 月 7 日
即將到來的排程維護
更新:在 5 月 7 日 MDT 時間 (5 月 8 日 UTC 時間) 維護期間沒有計畫的停機時間。
DigiCert 將在 2022 年 5 月 7 日 22:00 到 24:00 MDT (2022 年 5 月 8 日 4:00 到 06:00 UTC) 之間執行排程的維護。雖然我們有保護您的服務的適當備援,但有些 DigiCert 服務在這段時間內仍可能無法使用。
服務將在我們完成維護時盡快還原。
我可以做什麼?
訂出相應計畫:
在維護時段前後安排高優先順序訂單、續訂和重新發行的時間。
預期在您使用 API 進行立刻發行憑證和自動化工作時中斷。
若要取得即時維護更新,請訂閱 DigiCert 狀態頁面。此訂閱包括維護開始和維護結束時使用的電郵提醒。
請參閱 DigiCert 2022 維護排程的維護日期和時間。
2022 年 4 月 18 日
CertCentral:多年期套餐現在可用於經過驗證的標章憑證
我們很榮幸宣佈現在 CertCentral 和 CertCentral Services API 中的經過驗證的標章憑證 (VMC) 可使用多年期套餐。
DigiCert® 多年期套餐允許您支付一次優惠費用即可得到最長六年的經過驗證的標章憑證涵蓋時間。在多年期套餐中,您可以選取想要的涵蓋時間長度 (最長 6 年)。訂單到期前,每次重新發行憑證時都無需其他費用,直到有效期間結束為止。
Note
視您套餐的時間長度而定,您可能需要在您的多年期套餐期間重新驗證您的網域和組織多次。
Services API 中適用於 VMC 的多年期套餐
在 Services API 中,當您提交 VMC 的訂購要求時,請使用 order_validity 物件設定您的多年期套餐的涵蓋時間長度 (1-6 年)。如需更多資訊,請參閱:
什麼是「經過驗證的標章憑證」?
經過驗證的標章憑證 (VMC)是新型的憑證,允許公司將通過認證的品牌標誌放在客戶收件匣的「寄件者」欄位旁邊。
開啟訊息前可看到您的標誌。
您的標誌作為您網域的 DMARC 狀態和您組織的驗證身分的確認。
2022 年 4 月 11 日
CertCentral Services API:網域鎖定 API 端點
DigiCert 很榮幸發佈現在在 CertCentral Services API 中可使用我們的網域鎖定功能。
Note
在您可以使用網域鎖定端點前,您必須先啟用您的 CertCentral 帳戶的網域鎖定。請參閱網域鎖定 – 啟用您的帳戶的網域鎖定。
新 API 端點
啟用指定網域的網域鎖定。
停用指定網域的網域鎖定。
檢查指定網域的網域鎖定帳戶權杖的 DNS CAA 資源記錄。
更新的 API 端點
我們更新了網域資訊和列出網域端點的回應,納入以下有網域鎖定資料的參數:
domain_locking_status(字串)網域鎖定狀態。僅在啟用帳戶的網域鎖定時傳回。
account_token(字串)網域鎖定帳戶權杖。僅在啟用帳戶的網域鎖定時,或已啟用網域的網域鎖定至少一次時傳回。
若要瞭解更多資訊,請參閱 :
2022 年 4 月 5 日
CertCentral: Domain locking is now available
DigiCert is happy to announce our domain locking feature is now available.
Does your company have more than one CertCentral account? Do you need to control which of your accounts can order certificates for specific company domains?
Domain locking lets you control which of your CertCentral accounts can order certificates for your domains.
How does domain locking work?
DNS Certification Authority Authorization (CAA) resource records allow you to control which certificate authorities can issue certificates for your domains.
With domain locking, you can use this same CAA resource record to control which of your company's CertCentral accounts can order certificates for your domains.
How do I lock a domain?
To lock a domain:
Enable domain locking for your account.
Set up domain locking for a domain.
Add the domain's unique verification token to the domain's DNS CAA resource record.
Check the CAA record for the unique verification token.
To learn more, see:
帳戶從 Symantec、GeoTrust、Thawte 或 RapidSSL 升級至 CertCentral™ 的使用壽命結束
從 2022 年 4 月 5 日 MDT 起,您再也無法將您的 Symantec、GeoTrust、Thawte 或 RapidSSL 帳戶升級至 CertCentral™。
如果您尚未轉移到 DigiCert CertCentral,請立刻升級,保持您的網站安全並持續使用您的憑證。
我如何更新我的帳戶?
若要升級您的帳戶,請立刻聯絡 DigiCert 支援團隊。如需更多有關帳戶升級程序的資訊,請參與升級至 CertCentral: 您需要知道的事項
如果我未將我的帳戶升級至 CertCentral 會發生什麼情況?
在 2022 年 4 月 5 日後,您必須取得新的 CertCentral 帳戶和手動新增所有帳戶資訊,例如網域和組織。此外,您將無法將您任何的啟用憑證移轉到您的新帳戶。
如需 2022 年 4 月 5 日後設定您的新 CertCentral 帳戶的協助,請聯絡 DigiCert 支援團隊。
2022 年 4 月 2 日
即將到來的排程維護
DigiCert 將在 2022 年 4 月 2 日 22:00 到 24:00 MDT (2022 年 4 月 3 日 04:00 到 06:00 UTC) 之間執行排程的維護。在此期間,有些服務可能停機最多兩小時。
Note
維護將比沒有實施日光節約時間的時區早一小時。
基礎設備相關維護停機時間
我們將在 22:00 MDT (04:00 UTC) 開始此基礎設備相關維護。然後以下所列的服務可能停機最多兩小時。
CertCentral® TLS 憑證發行:
在此期間提交 TLS 憑證要求將會失敗
失敗的要求應在還原服務後重新提交
CIS 和 CertCentral® SCEP:
憑證發行服務 (CIS) 將停用
CertCentral 簡易憑證註冊通訊協定 (SCEP) 將停用
在此時間提交要求將會失敗
CIS API 將傳回「503 服務無法使用」錯誤
失敗的要求應在還原服務後重新提交
Direct Cert Portal 新網域和組織驗證:
在此時間提交新網域進行驗證將會失敗
在此時間提交新組織進行驗證將會失敗
失敗的要求應在還原服務後重新提交
QuoVadis® TrustLink® 憑證發行:
在此期間提交 TrustLink 憑證要求將會延遲
要求將新增到佇列中供稍後處理
在還原服務後,處理佇列中的要求
PKI Platform 8 新網域和組織驗證:
在此時間提交新網域進行驗證將會失敗
在此時間提交新組織進行驗證將會失敗
要求將新增到佇列中供稍後處理
在還原服務後,處理佇列中的要求
存取使用者授權代理程式 (UAA) 服務將遭到停用:UAA 系統管理員和使用者網頁入口網站
我可以做什麼?
訂出相應計畫:
在維護時段前後安排高優先順序訂單、續訂和重新發行的時間。
預期在您使用 API 進行立刻發行憑證和自動化工作時中斷。
若要取得即時維護更新,請訂閱 DigiCert 狀態頁面。此訂閱包括維護開始和維護結束時使用的電郵提醒。
關於排程的維護日期和時間,請參閱 DigiCert 2022 排程的維護。
服務將在我們完成維護時盡快還原。
2022 年 3 月 30 日
CertCentral:現在可使用大量網域重新驗證
DigiCert 很榮幸宣佈我們的大量網域驗證功能現在已可以使用。不要花費額外的時間一次提交一個網域進行重新驗證。使用我們的大量網域重新驗證功能,一次提交 2 到 25 個網域進行重新驗證。
請記住,網域驗證的有效期間只有 397 天。若要保持無縫發行憑證,DigiCert 建立在網域的驗證到期前預先完成網域控制驗證 (DCV)。
Note
目前,大量網域功能僅支援電郵 DCV 方法。若要使用其他 DCV 方法,您需要個別提交每個網域。
自己查看
在您的 CertCentral 帳戶的左側主功能表中,前往憑證 > 網域。
在網域頁面上,選取您要提交以進行重新驗證的網域。
在提交網域進行重新驗證下拉清單中,選取提交網域進行基於電郵的驗證。
請參閱 網域預先驗證:大量網域重新驗證。
2022 年 3 月 24 日
SSL 工具使用壽命結束
自 2022 年 3 月 24 日起,當您瀏覽 SSL 工具時,您將看到讓您知道 SSL 工具再也無法使用的彈出訊息。我們鼓勵您使用 DigiCert® SSL 安裝診斷工具。
Note
如果您瀏覽其他 SSL 工具功能/頁面,我們將引導您到提供相同或類似服務的 digicert.com 上的其他網頁。
什麼是「SSL 安裝診斷工具」?
「SSL 安裝診斷工具」是一款免費、公開可用的工具,用於檢查:
憑證安裝
網頁伺服器設定
我需要做什麼?
開始使用 DigiCert® SSL 安裝診斷工具。您將進行以下事項:
在您的瀏覽器中,以「DigiCert® SSL 安裝診斷工具」取代 SSL 工具書籤。
如果您有到您的網站上的「SSL 工具」的連結,請以到「SSL 安裝診斷工具」的連結取代它們。
2022 年 3 月 21 日
DigiCert 網站圖章現在可使用於 Basic OV 和 EV 憑證訂單
DigiCert Basic OV 和 EV 憑證訂單包含 DigiCert 網站圖章。現在,您可以在相同的網站上,安裝您的 Basic SSL 憑證保護的 DigiCert 網站圖章。網站圖章向您的客戶提供您的網站安全受到 DigiCert (TLS/SSL 安全性之中最著名的名稱之一) 保護的保證。
當您按下網站圖章時,您會看到更多與網域、組織、TLS/SSL 憑證和驗證有關的詳細資料。
DigiCert 智慧圖章
DigiCert 也提供更新型的網站圖章 — DigiCert 智慧圖章。此進階圖章比 DigiCert 網站圖章更有互動性和關聯性。我們新增了懸浮效果、動畫和以懸浮效果和動畫功能顯示您的公司標誌的能力。
2022 年 3 月 10 日
CertCentral: DV 憑證訂單現在可使用 DNS CNAME DCV 方法
在 CertCentral 和 CertCentral Services API 中,現在您可以使用 DNS CNAME 網域控制驗證 (DCV) 方法驗證您的 DV 憑證訂單上的網域。
Note
之前,您僅可以使用 DNS CNAME DCV 方法驗證 OV 和 EV 憑證訂單上的網域和在預先驗證網域時使用。
若要使用您的 DV 憑證訂單上的 DNS CNAME DCV 方法:
在 CertCentral 中:
訂購 DV TLS 憑證時,您可以選取 DNS CNAME 作為 DCV 方法。
在 DV TLS 憑證的訂單詳細資料頁面上,您可以將 DCV 方法變更為 DNS CNAME 記錄。
在 Services API 中:
要求 DV TLS 憑證時,將 dcv_method 要求參數的值設定為 dns‑cname‑token。
Note
產生立刻發行 DV 憑證的要求權杖的驗證金鑰程序不支援 DNS CNAME DCV 方法。但您可以使用檔案驗證 (http‑token) 和 DNS TXT (dns‑txt‑token) DCV 方法。若要瞭解更多資訊,請瀏覽 DV 憑證立刻發行。
若要瞭解更多有關使用 DNS CNAME DCV 方法的資訊:
對於 CertCentral:
對於 Services API:
2022 年 3 月 8 日
CertCentral Services API:改進的網域端點回應清單
為了更容易找到與您的 CertCentral 帳戶中的網域控制驗證 (DCV) 狀態有關的資訊,我們在列出網域 API 回應的網域物件中加入這些回應參數:
dcv_approval_datetime:網域的最新 DCV 檢查的完成日期和時間。last_submitted_datetime:上次提交網域進行驗證的日期和時間。
如需更多資訊,請參閱列出網域端點的參考文件。
2022 年 3 月 5 日
即將到來的排程維護
DigiCert 將在 2022 年 3 月 5 日 22:00 到 24:00 MST (2022 年 3 月 6 日 05:00 到 07:00 UTC) 之間執行排程的維護。在此期間,有些服務可能停機最多兩小時。
基礎設備相關維護停機時間
我們將在 22:00 MST (05:00 UTC) 開始此基礎設備相關維護。然後以下所列的服務可能停機最多兩小時。
CertCentral™ TLS 憑證發行:
在此期間提交 TLS 憑證要求將會失敗
失敗的要求應在還原服務後重新提交
CIS 和 CertCentral™ SCEP:
憑證發行服務 (CIS) 將停用
CertCentral 簡易憑證註冊通訊協定 (SCEP) 將停用
在此時間提交要求將會失敗
CIS API 將傳回「503 服務無法使用」錯誤
失敗的要求應在還原服務後重新提交
Direct Cert Portal 新網域和組織驗證:
在此時間提交新網域進行驗證將會失敗
在此時間提交新組織進行驗證將會失敗
失敗的要求應在還原服務後重新提交
QuoVadis™ TrustLink™ 憑證發行:
在此期間提交 TrustLink 憑證要求將會延遲
要求將新增到佇列中供稍後處理
在還原服務後,處理佇列中的要求
PKI Platform 8 新網域和組織驗證:
在此時間提交新網域進行驗證將會失敗
在此時間提交新組織進行驗證將會失敗
要求將新增到佇列中供稍後處理
在還原服務後,處理佇列中的要求
我可以做什麼?
訂出相應計畫:
在維護時段前後安排高優先順序訂單、續訂和重新發行的時間。
預期在您使用 API 進行立刻發行憑證和自動化工作時中斷。
若要取得即時維護更新,請訂閱 DigiCert 狀態頁面。此訂閱包括維護開始和維護結束時使用的電郵提醒。
關於排程的維護日期和時間,請參閱 DigiCert 2022 維護排程。
服務將在我們完成維護時盡快還原。
2022 年 2 月 17 日
CertCentral:改進的經過驗證的聯絡人 EV TLS 憑證要求核准程序
在 CertCentral 和 the CertCentral Services API 中,我們已更新 EV TLS 憑證請求程序為僅傳送 EV TLS 請求核准電郵給在您的憑證要求上納入的經過驗證的聯絡人。
Note
之前,當您要求 EV TLS 憑證時,我們會將 EV 訂單核准電郵傳送給組織所有經過驗證的聯絡人。
新增經過驗證的聯絡人到 EV TLS 憑證要求中:
CertCentral
要求 EV TLS 憑證時,您可以:
保持指派給組織的現有經過驗證的聯絡人
移除聯絡人 (需要至少一個)
新增新的聯絡人 (我們必須驗證每個新聯絡人,可能導致發行憑證延遲)
Sevices API
請求 EV TLS 憑證時,在 JSON 要求的
organization.contacts陣列中納入經過驗證的聯絡人。關於經過驗證的聯絡人,contact_type欄位中的值是ev_approver。
若要瞭解更多有關 EV TLS 憑證要求的資訊:
關於 CertCentral,請參閱訂購 EV SSL/TLS 憑證。
關於 Services API,請參閱 Order Basic EV、Order Secure Site EV 和 Order Secure Site Pro EV。
2022 年 2 月 12 日
展開使用於 DigiCert 服務的 IP 位址範圍
在 2022 年 2 月 12 日 22:00 – 24:00 MST (2022 年 2 月 13 日 05:00 - 07:00 UTC) 的排程維護是我們的排程維護的一部份,DigiCert 正在擴大我們用於我們的服務的 IP 位址範圍。這些其他 IP 位址是我們努力增加服務運作時間,以及減少排程維護時間所做的努力的一部份。
我需要做什麼?
如果您的公司使用允許清單*,在 2022 年 2 月 12 日前加入以下所列的 IP 位址的區塊,以便保持您的 DigiCert 服務和 API 整合如預期般運作。
Note
*允許清單是使用於防火牆的清單,僅允許指定的 IP 位址執行特定工作或與您的系統連線。
新的 IP 位址範圍
新增此 IP 位址範圍到您的允許清單*中:216.168.240.0/20
Important
我們未正在取代或移除任何 IP 位址。我們僅展開我們提供我們的服務所使用的 IP 位址的範圍。
如需簡易參考,請參閱我們的知識庫文章展開 DigiCert 服務使用的 IP 位址範圍。如果您有疑問,請聯絡您的帳戶管理員或 DigiCert 支援團隊。
受影響的服務:
CertCentral/Services API
ACME
Discovery/API
探索感應器防火牆設定
ACME 自動化/API
憑證發行服務 (CIS)
單一憑證註冊通訊協定 (SCEP)
API 存取 URL
Direct Cert Portal/API
DigiCert 網站
驗證服務
PKI Platform 8
PKI Platform 7 (日本和澳大利亞)
QuoVadis TrustLink
DigiCert ONE
Account Manager
CA Manager
IoT Device Manager
Document Signing Manager
Secure Software Manager
Enterprise PKI Manager
Automation Manager
2022 年 2 月 9 日
CertCentral Services API:網域資訊增強
我們更新了網域資訊 API 回應,納入與網域關聯的 DCV 權杖的 expiration_date 參數。現在,當您呼叫 Domain info API 並將 include_dcv 查詢參數的值設定為 true 時,回應中的 dcv_token 物件加入了網域的 DCV 權杖的 expiration_date。
{
...
"dcv_token": {
"token": "91647jw2bx280lr5shkfsxd0pv50ahvg",
"status": "pending",
"expiration_date": "2022-02-24T16:25:52+00:00"
},
...
}2022 年 2 月 8 日
l帳戶安全性功能:核准的使用者電郵網域
CertCentral 系統管理員現在可指定電郵網域使用者建立 CertCentral 帳戶所針對的內容。這有助於防止將電郵傳送到未核准、一般的電郵網域 (@gmail.com, @yahoo.com) 或第三方擁有的網域。如果使用者嘗試將使用者電郵地址設定或變更為未核准的網域,他們會收到錯誤。
在設定 > 喜好設定中尋找此設定。展開進階設定,然後尋找核准的電郵網域區段。
Note
此設定不會影響有未核准的電郵地址的現有使用者。只會影響新的使用者和設定此設定後所做的電郵變更。
2022 年 2 月 1 日
經過驗證的標章憑證 (VMC):三個新核准的商標局
我們很榮幸宣佈 DigiCert 現在可識別的驗證您的 VMC 憑證所使用標誌的智慧財產局增加了三個。這些新的辦事處位於韓國、巴西和印度。
新核准的商標局:
其他核准的商標局:
什麼是「經過驗證的標章憑證」?
經過驗證的標章憑證 (VMC)是新型的憑證,允許公司將通過認證的品牌標誌放在客戶收件匣的「寄件者」欄位旁邊。
開啟訊息前可看到您的標誌。
您的標誌作為您網域的 DMARC 狀態和您組織的驗證身分的確認。
Bugfix:Code Signing (CS) 憑證產生電郵僅傳送給 CS 驗證的聯絡人
我們修復 Code Signing (CS) 憑證發行程序中的 Bug,其中我們僅傳送憑證產生電郵給 CS 驗證的聯絡人。此 Bug 只會發生在要求者未要求者未納入有代碼簽署憑證要求的 CSR 時。
現在,對於提交的沒有 CSR 的訂單,我們將代碼簽署憑證產生電郵傳送到:
憑證要求者
CS 驗證的聯絡人
訂單包括的其他電郵
Note
DigiCert 建議提交有您的 Code Signing 憑證要求的 CSR。目前,Internet Explorer 是唯一支援產生金鑰組的瀏覽器。請參閱我們的知識庫文章:放棄對 Firefox 69 的 Keygen 支援。
2022 年 1 月 25 日
更新至 OV 和 EV TLS 憑證設定檔
我們致力於統一我們的 DV、OV 和 EV TLS 憑證設定檔,因此對我們的 EV TLS 憑證設定檔做了小變更。2022 年 1 月 25 日,我們在我們的 OV 和 EV TLS 憑證設定檔中,將 Basic Constraints 延伸程式設定為非重大。
Note
DV TLS certificates 已發行,Basic Constraints 延伸程式設定為非重大。
我需要做什麼?
您的方面不需要採取動作。您應該不會注意到您的憑證發行程序中的任何差別。但如果您的 TLS 憑證程序需要將 Basic Constraints 延伸程式設定為重大,請立刻聯絡您的帳戶管理員或 DigiCert 支援團隊。
2022 年 1 月 24 日
改進的網域頁面、驗證狀態篩選器 — 已完成/已驗證
在網域頁面的驗證狀態下拉清單中,我們更新了已完成/已驗證篩選器,因此更容易找到已完成和啟用網域控制驗證 (DCV) 的網域。
Note
之前,當您搜尋有已完成/已驗證 DCV 的網域時,我們傳回所有已完成 DCV 的網域,即使網域驗證已到期。
現在,當您搜尋有已完成/已驗證 DCV 的網域時,我們僅傳回您的搜尋結果中已完成和啟用 DCV 的網域。若要尋找 DCV 已到期的網域,請使用驗證狀態下拉清單中的已到期篩選器。
尋找已完成和啟用 DCV 的網域
在 CertCentral 的左側主功能表中,前往憑證 > 網域。
在網域頁面的驗證狀態下拉清單中,選取已完成/已驗證。
CertCentral Services API:列出網域增強
對於 List domains API,我們更新了 filters[validation]=completed 篩選條件,因此更容易找到為了發行 OV 或 EV 憑證而驗證的網域。
之前,此篩選條件傳回完成 DCV 檢查的所有網域,即使網域驗證已到期。現在,篩選條件僅傳回 OV 或 EV 網域驗證狀態為啟用的網域。
2022 年 1 月 10 日
CertCentral 網域和網域詳細資料頁面:改進的網域驗證追蹤
我們更新了網域和網域詳細資料頁面,因此更容易追蹤和保持您的網域的最新驗證。這些更新符合去年業界對網域驗證重新使用期*的變更。將您的網域驗證保持為最新減少了憑證發行時間:新的、重新發行、重複發行和續訂。
Note
*2021 年 10 月 1 日,業界將所有網域驗證重新使用期減少為 398 天。DigiCert 實施 397 天網域驗證重新使用期,確保憑證不是使用到期的網域驗證發行。如需更多與此變更有關的資訊,請參閱我們的知識庫文章:2021 年網域驗證原則變更。
網域頁面改進
當您瀏覽「網域」頁面時 (在左側的主功能表中,選取憑證 > 網域),您將看到三個新欄:DCV 方法、驗證狀態和驗證到期。現在您可以檢視用於證明網域控制權、網域驗證的狀態 (擱置、已驗證、即將到期和已到期)和網域驗證到期時間的網域控制驗證 (DCV) 方法。
由於 OV 和 EV 驗證重新使用期相同,因此我們簡化了驗證狀態排序功能。除了顯示 OV 驗證和 EV 驗證各自的篩選期外,我們僅顯示一組篩選器:
已完成/已驗證
擱置中驗證
0-7 天內到期
0-30 天內到期
31-60 天內到期
61-90 天內到期
已到期
網域詳細資料頁面改進
當您瀏覽網域的詳細資料頁面時 (在網域頁面上,選取網域),您將在頁面頂端看到狀態列。此狀態列讓您檢視網域的驗證狀態、網域驗證到期的時間、網域驗證最近完成的時間和證明網域控制權所使用的 DCV 方法。
我們也更新了頁面的網域驗證狀態區段。我們以一個項目「網域驗證狀態」取代了 OV 和 EV 網域驗證狀態的個別項目。
2022 年 1 月 8 日
即將到來的排程維護
DigiCert 將在 2022 年 1 月 8 日 22:00 到 24:00 MST (2022 年 1 月 9 日 05:00 到 07:00 UTC) 之間執行排程的維護。雖然我們有保護您的服務的適當備援,但有些 DigiCert 服務在這段時間內仍可能無法使用。
我可以做什麼?
訂出相應計畫:
在維護時段前後安排高優先順序訂單、續訂和重新發行的時間。
如果您使用 API 進行立刻發行憑證和自動化工作,預期會中斷。
若要取得即時維護更新,請訂閱 DigiCert 狀態頁面。此訂閱包括維護開始和維護結束時使用的電郵提醒。
關於排程的維護日期和時間,請參閱 DigiCert 2022 排程的維護。
服務將在我們完成維護時盡快還原。