Using Yubico tokens
Prerequisites
Install Yubico PIV tool version 2.4.0 or higher in the default directory.
For Windows: C:\Program Files\Yubico\Yubico PIV Tool\
For macOS: /usr/local/ (User should have no option to choose)
Install YubiKey Manager version 1.2.3 or higher in the default directory.
For Windows: C:\Program Files\Yubico\YubiKey Manager\
For macOS: /Applications/YubiKey Manager.app/ (User should have no option to choose)
Install YubiKey Smart Card Minidriver (scroll down to the Yubico PIV Tool section) version 4.6.3.252 or higher for Windows only.
You must configure your token. Follow the instructions provided in Configure your Yubico token.
Configure Management Key to protect with User PIN . Follow the instructions provided in Configure your Yubico token.
If you are using a new token or have already configured your token, it is recommended to change your PIN, PUK, and Management Key. Follow the instructions provided in Configure your Yubico token.
Note
DigiCert provides third-party URLs on this page as a convenient resource for accessing required software and installation instructions. While we strive to recommend reputable third-party sources, DigiCert is not responsible for, nor can we guarantee, the content or availability of these URLs.
Configure your Yubico token
To configure your Yubico token, change the default values for the following:
User PIN
User PUK
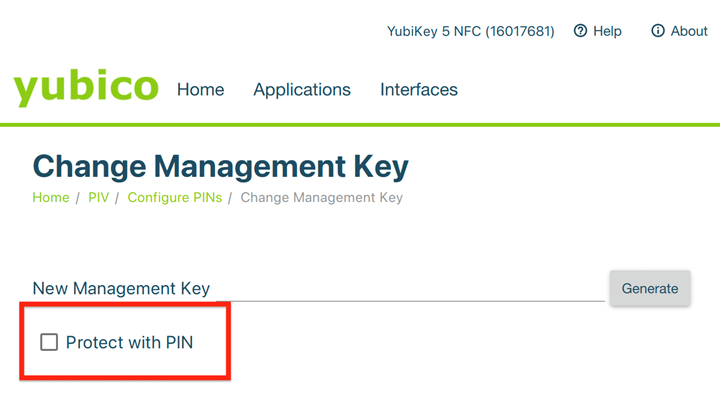
Management Key - This needs to be additionally protected by User PIN.
On Yubi Manager, while setting Management Key , user needs to select the Protect with PIN checkbox.
 |
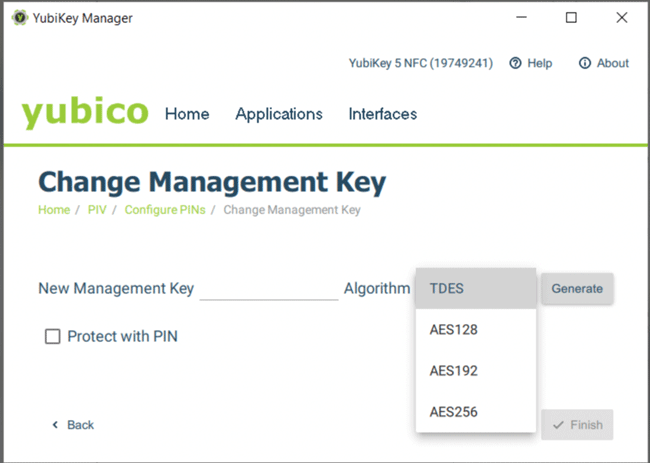
Yubico tokens may allow you to select an algorithm when setting or changing your Management Key. You can choose any supported algorithm, such as TDES or AES (AES-128, AES-192, AES-256), and proceed.
 |
Restrictions
Yubico tokens cannot import Certificate Authorities (CA) because each slot is limited to storing one certificate.
When a certificate is deleted from DigiCert® Trust Assistant, the private key associated with the certificate will not be removed from the token. The same restriction applies when using YubiKey Manager.
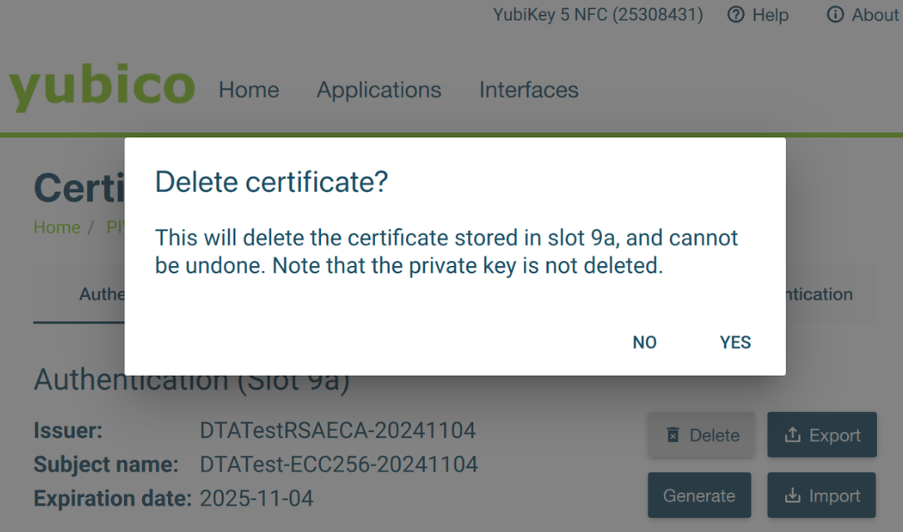
When the Yubico token is used by the operating system or other third-party applications, it may lose connection with DigiCert® Trust Assistant. Refer to the troubleshooting steps in the next section to resolve the issue.
Troubleshooting
For detailed troubleshooting information, see the section on Yubico tokens in Troubleshooting.